- Services
- Solutions
- Why Critical Start?
- Resources
- About
- Partner Programs
- Breach Response
- Contact an Expert
- Intelligence Hub
Build vs. Buy
How MDR boosts the value provided by a traditional Security Operations Center (SOC)

What You’ll Learn
In this paper, you will learn how to uncover the hidden costs involved in deploying and staffing a SOC. We’ll take a realistic look at the effort, expertise and infrastructure necessary and break down the best option for a cost-effective yet strong approach to information security.
-
-
![]()
Navigating the Cyber World: Understanding Risks, Vulnerabilities, and Threats
Cyber risks, cyber threats, and cyber vulnerabilities are closely related concepts, but each plays a...The Next Evolution in Cybersecurity — Combining Proactive and Reactive Controls for Superior Risk Management
Evolve Your Cybersecurity Program to a balanced approach that prioritizes both Reactive and Proactiv...![]()
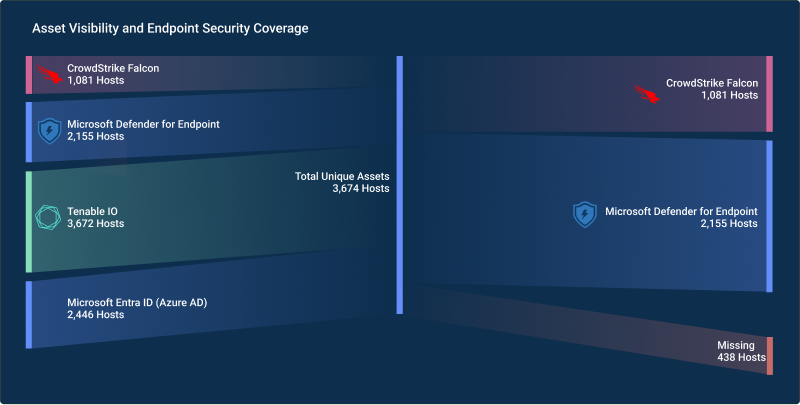
CISO Perspective with George Jones: The Top 10 Metrics for Evaluating Asset Visibility Programs
Organizations face a multitude of threats ranging from sophisticated cyberattacks to regulatory comp...![]() eBook
eBookInfosec Reborn
In this paper, you will learn how to evaluate security risks and why legacy detection and response e...![]() eBook
eBookGuide to Managed Detection & Response
Managed Detection and Response is reinventing information security. In this paper, you will learn ho...![]() Customer Stories
Customer StoriesCentennial School District Case Study
Fran Watkins, Network and Systems Administrator for Centennial School District, was solely responsib...
Newsletter Signup
Stay up-to-date on the latest resources and news from CRITICALSTART.
Thanks for signing up!