- Services
- Solutions
- Why Critical Start?
- Resources
- About
- Partner Programs
- Breach Response
- Contact an Expert
- Intelligence Hub
How much risk are you accepting?
Learn how Critical Start Managed Detection and Response services can reduce your risk.
Breaches and ransomware can shut down your business for days, putting revenues and productivity at risk.
Input values specific to your organization and calculate your risk acceptance.
Reduce risk acceptance, increase efficiency, accelerate return on investment.
Decrease time spent on alerts by 99.3%.*
Through the combination of our Cyber Operations Risk & Response™ platform and MDR services, we enable a single analyst to fully resolve all alerts regardless of priority level – what would have previously taken 80 full-time analysts.
* Assumption of workload based on average of 7-minute Critical Start alert investigation time. Client workload with the platform and MDR is 22 hours/week. For the same volume of alert resolution without Critical Start MDR service and the platform it would take 3,179 hours/week.
24x7x365 RSOC.
Critical Start security analysts undergo 200 on-boarding hours and 40-60 hours annually for continuous training.
Reduce alert volume by 99%.
With our Trusted Behavior Registry™ (TBR) resolving 99% of alerts and 1% investigated by our expert SOC, we only escalate an average of .1% of alerts. No more getting the same alert twice, and no more wasting precious time.
100% transparency.
100% transparency means you can always see actions taken by our team in the platform and MOBILESOC®.
How much risk should you accept? None.
Discover the financial consequences of risk acceptance

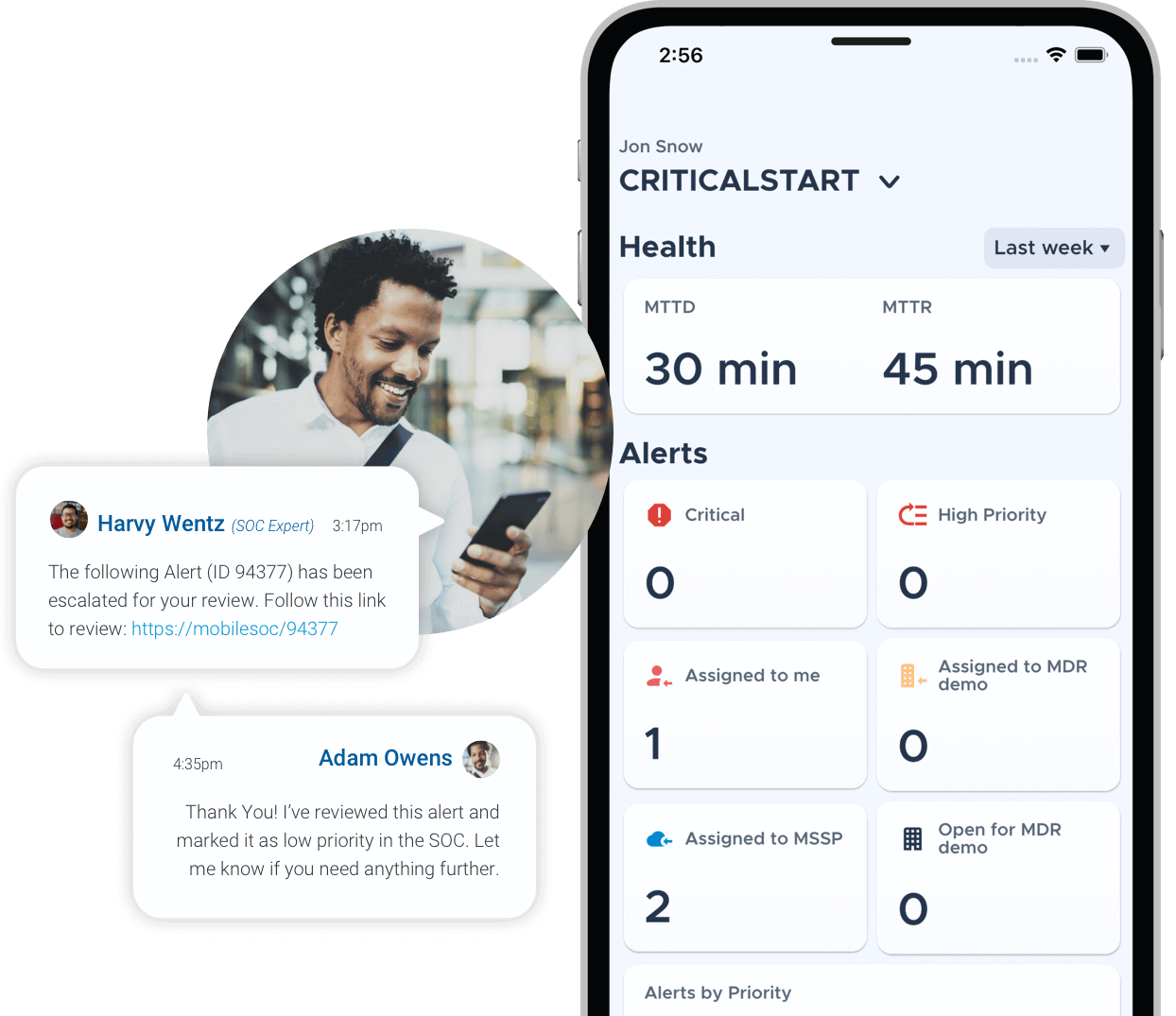
Untether your analysts.
Drive down attacker dwell time with Critical Start MobileSOC. Through this iOS and Android app, we go beyond ticketing and instant notifications, giving you the ability to action incidents immediately with information gathered in our platform.
Untether your analysts.
Triage, containment, and collaboration just went portable. With our MOBILESOC, you can do it all from anywhere. Note: Desks may experience separation anxiety.

Take it from our clients
-

PRESTON BROESCHE
The main difference between the other options and this one is the quality of the personnel within the SOC. It’s their knowledge and depth and the way they handle customers.
Kirby Corporation -
CHARLES F.
The service has increased our analysts’ efficiency to the point that they can focus on other areas of the business. It gives me the ability to allow analysts to do Level 3 and 4 work and stay out of the weeds of the alerts, where you tend to get alert fatigue. The service takes care of much of the Tier 1 and Tier 2 triage…This leaves less for us to handle, which is a good thing.
Financial Services Firm -

RYAN CARTER
Outside of using the platform to manage alerts, the feature of the service that we get the most value from is being able to reach out to them and say, “Hey, we might go buy a SIEM,” for example. They give us their overview of what’s out there, what they’ve dealt with, what they integrate with, and what that looks like. That’s been pretty powerful over the years for us.
StackPath -

DMITRI CHERNYSHEV
This has been a positive experience and money well spent. If we had to do it again, we would gladly choose the solution that CRITICALSTART provides, versus going with other solutions or using something in-house where we would probably have to spend double what we are spending now.
Energy/Utilities Company
-
 WHITEPAPER
WHITEPAPEREconomic Value from a Managed Detection and Response (MDR) Solution
This white paper discusses how organizations can leverage an external MDR solution to help accelerate their business growth without compromising security.
-
 WHITEPAPER
WHITEPAPERBuild vs. Buy
In this paper, you will learn how to uncover the hidden costs involved in deploying and staffing a SOC. We’ll take a realistic look at the effort, expertise and infrastructure necessary and break down the best option for a cost-effective yet strong approach to information security.