TLP CLEAR // [CS-SA-26-0102] Iranian Cyber Threat Activity on U.S. Financial Institutions
Executive Summary
Geopolitical relations and tensions significantly impact cyber threat activity, as state-aligned cyber groups often escalate operations in response to regional conflicts, sanctions, and shifts in foreign policy. As tensions between the U.S. and Iran remain high, the risk of cyberattacks targeting U.S. organizations is on the rise. Iranian cyber threat actors execute a variety of tactics, from sophisticated espionage campaigns using spear-phishing, credential harvesting, and advanced malware by advance persist threat (APT groups), to less technical attacks such as denial-of-service and web defacements by hacktivist groups. The targets of these cyber operations typically include sectors of high strategic value, such as financial institutions, energy providers, and critical infrastructure. These industries are particularly vulnerable due to their economic significance and visibility. As U.S. foreign policy increasingly aligns with Israel, an adversary of Iran, the likelihood of sustained cyberattacks against the U.S. grows. This reality makes it imperative for U.S. organizations, particularly those in critical sectors, to remain vigilant. The implications of Iran-sponsored cyberattacks are far-reaching, affecting operational continuity, financial stability, and regulatory compliance.
Introduction
Attackers Iran’s state-directed cyber operations are carried out by the Islamic Revolutionary Guard Corps (IRGC) and the Ministry of Intelligence and Security (MOIS). Each organization manages distinct advanced persistent threat (APT) groups that support Iran’s strategic objectives. These state-aligned actors run targeted intrusion campaigns using a mix of social engineering techniques, exploitation of known vulnerabilities, credential harvesting, custom malware, and legitimate administration tools. Their primary goal is to gain persistent access and gather intelligence on foreign targets, including both U.S. government and private sector entities. Each APT group follows its own operational approach, tailored to its specific mission and target. Some focus on espionage, while others aim to exploit exposed infrastructure for strategic advantage.
The following sections provide a detailed examination of MuddyWater and secondary mentions of PIONEER KITTEN, and APT35 respectively. According to security researchers, these APT groups’ tradecraft and operational behaviors advance the agenda of both MOIS and IRGC. MuddyWater executes persistent, espionage campaigns supported by a diverse malware ecosystem and credential‑centric techniques. PIONEER KITTEN focuses on exploiting internet‑facing services and edge infrastructure for initial access and sustained access. APT35 techniques of spear-phishing for credential harvesting and initial access overlaps with MuddyWater, though with slight differences post-compromise.
Primary Mention
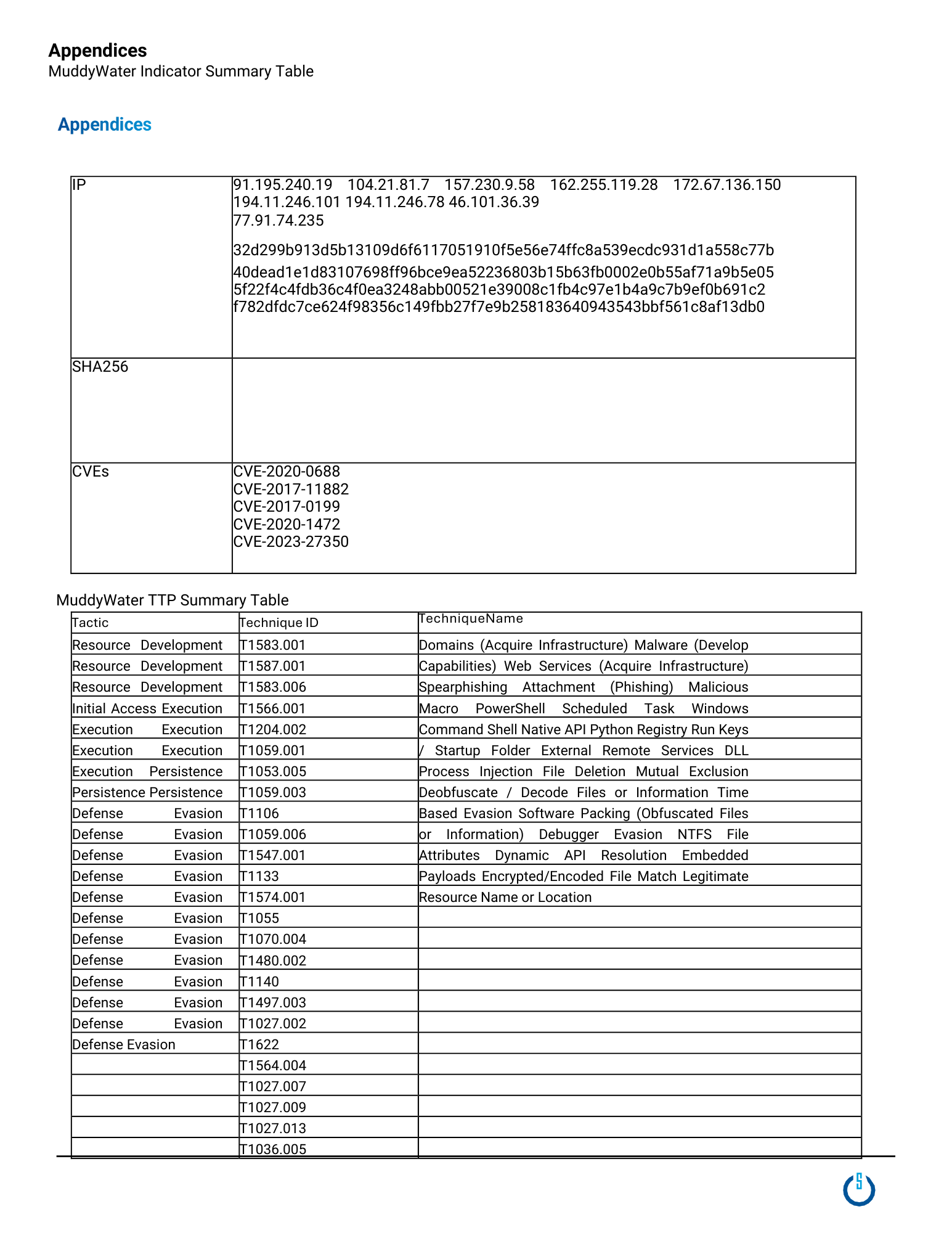
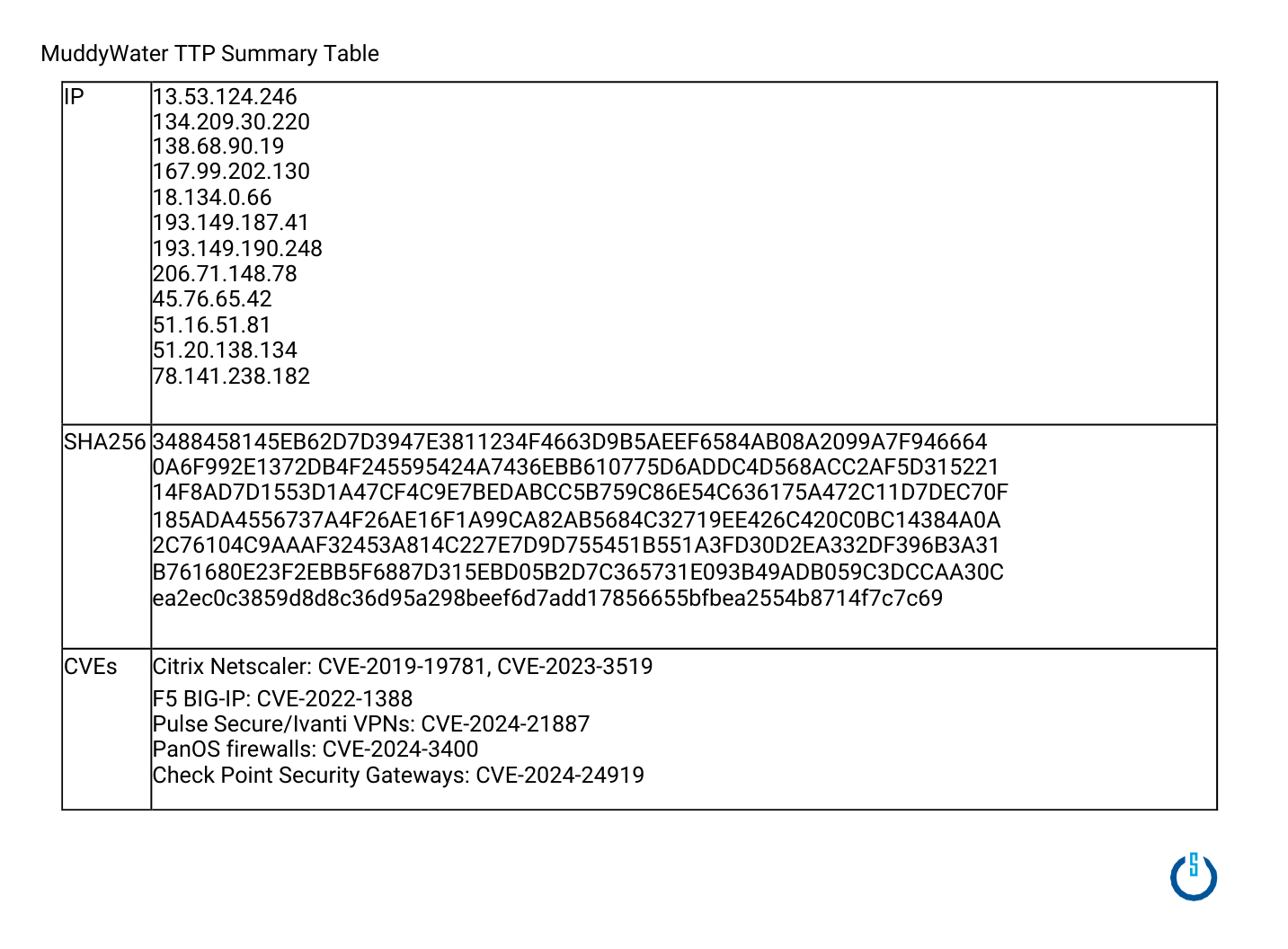
MuddyWater is an Iran-linked advanced persistent threat (APT) group known for its espionage activities and other cyberattacks. It operates as a subordinate of the Iranian Ministry of Intelligence and Security (MOIS). The group's primary targets include organizations in the Government, Energy, Telecommunications, and Financial Services sectors, among others. Geographically, MuddyWater targets the Middle East, but its operations also extend to regions such as North America and Asia.
The group is known by several aliases, including Seedworm, MERCURY, Earth Vetala, TEMP.Zagros, COBALT ULSTER, TA450, Boggy Serpens, and Static Kitten.
MuddyWater primarily uses spear-phishing, exploitation of known vulnerabilities, custom malware, and obfuscated PowerShell scripts to gain initial access, maintain persistence, and exfiltrate data. CISA's earlier reports also highlight the group's use of credential-driven campaigns, such as password spraying and MFA push techniques, to gain valid access for follow-up operations. Once access is obtained, the group often performs network and identity discovery to escalate privileges, harvest additional credentials, and ensure continued access. In many cases, MuddyWater positions itself as an initial access broker, enabling espionage, fraud, or other targeted operations.
Initial Access
- MuddyWater commonly gains initial access through spear‑phishing emails that deliver malicious Microsoft Word documents impersonating government, telecommunications, or business communications relevant to the target region. These documents prompt users to enable macros, which immediately spawn child processes such as powershell.exe, cmd.exe, or mshta.exe. The embedded macro code typically launches Base64‑encoded PowerShell commands and FakeUpdate‑style loaders, with payloads written to user‑writable directories including %TEMP%, %APPDATA%, and %ProgramData%.
- MuddyWater also leverages legitimate Remote Monitoring and Management (RMM) tools such as ScreenConnect and Atera Agent for initial access. Commercial file‑sharing services including Dropbox, Egnyte, and OneDrive adversarial operations of MuddyWater.
- MuddyWater also conducts credential driven campaigns, including password spraying, MFA fatigue attacks, and self-service password reset, to obtain valid access that can be leveraged for follow-on operations.
Execution and Persistence
- MuddyWater maintains execution and persistence through a diverse malware ecosystem that includes LiteInject (injector), BugSleep (backdoor), and Fooder (loader), enabling capabilities such as backdoor access, remote administration, information theft, and payload delivery.
- The group commonly establishes persistence through registry-based mechanisms, including modification of the HKCU\Software\Microsoft\Windows\CurrentVersion\Run key and alteration of the Winlogon\Shell value, notably observed in Phoenix malware deployments. MuddyWater frequently executes unsigned Golang or Rust binaries without installers or user prompts and creates structured, non-random mutexes to coordinate malicious processes.
- PowerShell abuse is a consistent tradecraft element, characterized using Invoke-Expression, AMSI bypass techniques, and the disabling or evasion of PowerShell logging.
Secondary Mentions
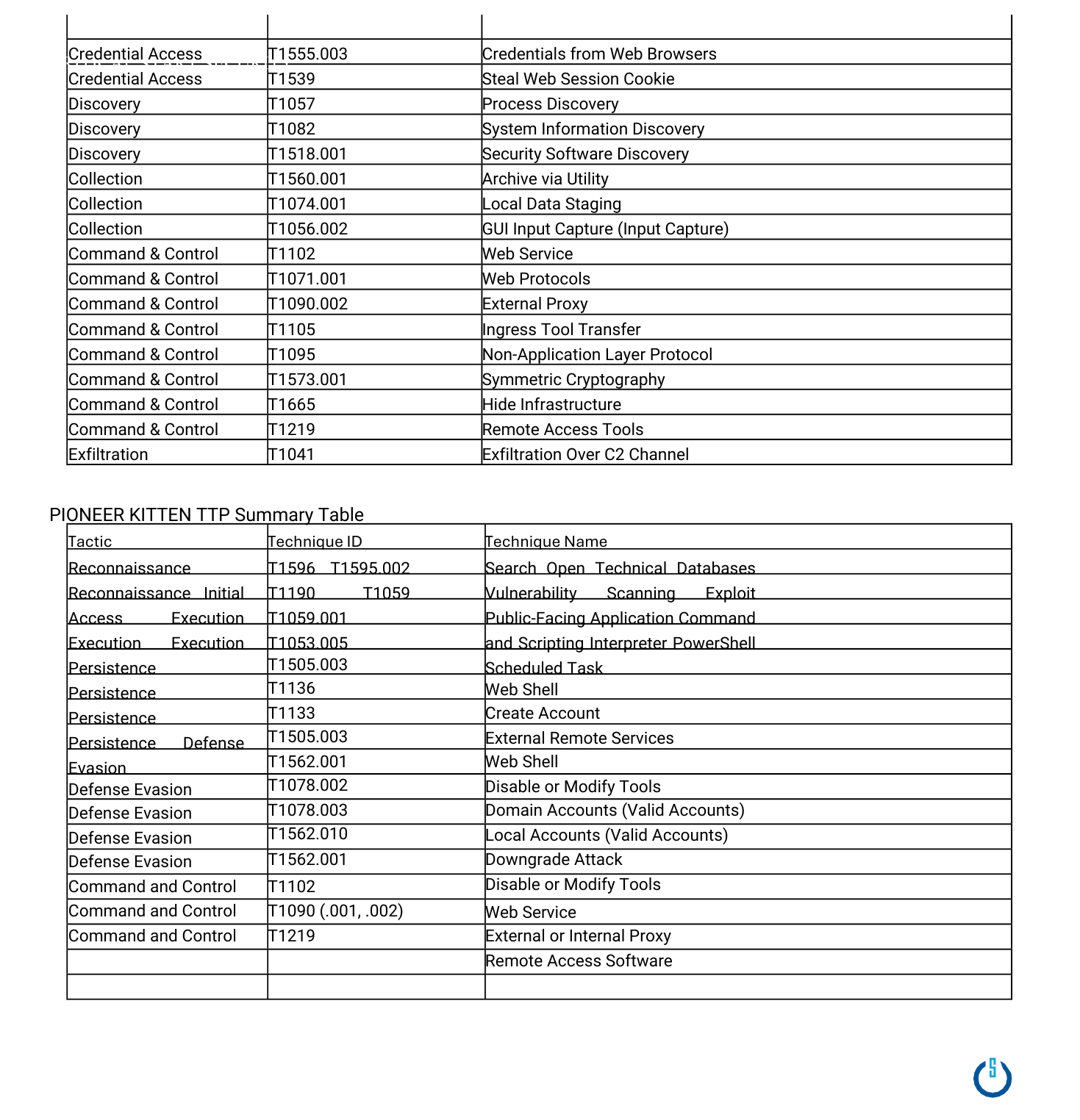
PIONEER KITTEN is an Iran-linked threat actor that primarily exploits internet-facing services to gain initial access, relying heavily on open-source tooling throughout operations. The group frequently targets VPNs and network appliances, leveraging known vulnerabilities such as CVE-2019-11510, CVE-2019-19781, and CVE-2020-5902, reflecting an opportunistic operational approach. Its hallmark tradecraft includes SSH tunneling using open-source tools like Ngrok and its custom tool SSHMinion, as well as hands-on-keyboard activity via Remote Desktop Protocol (RDP). Identified targeting focuses on North American and Israeli entities of probable intelligence interest to Iran, with key sectors including technology, government, defense, and healthcare, though activity spans a broad range of industries including aviation, media, academia, engineering, consulting, chemical, manufacturing, financial services, insurance, and retail.
APT35 is an Iran-linked advanced persistent threat group that primarily relies on spear-phishing to gain initial access, often impersonating scholars, journalists, or organizations. The group uses fraudulent domains and compromised third-party accounts to increase the credibility of phishing lures, while also exploiting vulnerabilities like ProxyShell.
Once inside, APT35 deploys credential-harvesting tools, spyware, and custom malware, including HYPERSCRAPE for email account compromise and PowerShell-based reconnaissance. Persistence is maintained through stolen credentials, email forwarding rules, and backdoors like DownPaper or Telegram-based C2 channels. The group leverages a broad infrastructure
of fraudulent domains and cloud instances to ensure resilience across operations. Targets include high-value sectors such as financial services, government, energy, and telecommunications, with a focus on entities in the Middle East and North America. While PIONEER KITTEN and APT35 are secondary mentions, they are no less of a threat. Their tactics remain effective, and they continue to target critical sectors, regardless of their less frequent mention.
Implications for Financial Services Sector
The financial services industry is a prime target due to its strategic value and role in the global economy. Cyberattacks on banks, payment systems, and lenders can lead to severe financial losses, reputational damage, and disruption of essential services. In addition, these attacks may involve the theft of confidential customer data, intellectual property, or proprietary financial information, which can be exploited for further cyberattacks or sold on the dark web. Notably, IBM’s 2025 Cost of a Data Breach Report notes an average cost of 5.56 million USD for data breaches impacting the Financial Services sector.
Financial institutions are also at heightened risk during periods of geopolitical tension, particularly when Iran's national interests are threatened. Given Iran’s adversarial relationship with Western governments, including the U.S. and Israel, the financial sector may be targeted as part of broader retaliation efforts. In this context, financial organizations may experience an increase in cyber espionage, data exfiltration, and even operational disruption intended to cause widespread economic damage. Since APT groups are known for maintaining persistent access over long periods, financial organizations should expect not just short-term vigilance but ongoing, sustained monitoring and defense, even when geopolitical tensions appear to subside.
Organizational Mitigation Strategies
In light of Iranian cyber threat activities, organizations must adopt proactive, structured approaches to reduce exposure to cyber threats. Key strategies include:
- Harden email and document handling controls. Block or sandbox attachments that attempt to execute macros or scripts, especially from untrusted sources, and enforce policies that allow only signed or pre-approved macros to run.
- Enforce strict identity and access protections. Implement least-privilege access, monitor for abnormal MFA activity, and restrict self-service password resets that could be abused for persistent access.
- Patch and secure internet-facing services. Prioritize remediation of known vulnerabilities in VPNs, network appliances, and other exposed systems targeted by Iranian APTs, and monitor for exploitation attempts.
- Monitor and control remote administration tools. Audit legitimate RMM software and SSH/RDP access for anomalous usage, unauthorized tunnels, or connections outside of normal business hours.
- Proactively hunt for indicators of compromise. Query endpoints, servers, and cloud environments for malware signatures, suspicious PowerShell commands, credential theft patterns, and other IOCs reported for MuddyWater and Pioneer Kitten, and validate detection efficacy through regular testing.
- Enhance social engineering defenses. Conduct targeted employee training and phishing simulations that reflect Iranian APT tactics, such as politically themed lures, fake government or business communications, and credential-stealing schemes, to strengthen human resilience against initial access attempts.
- Engage with Information Sharing and Analysis Centers (ISACs). Actively share and consume threat intelligence through sector-specific ISACs to receive early warnings, understand emerging Iranian cyber tactics, and coordinate mitigation strategies across organizations with similar risk profiles.
Conclusion
Iran-aligned cyber actors continue to pose a significant threat to U.S. interests, particularly in sectors such as finance, energy, and critical infrastructure. Their tactics, ranging from strategic espionage to ideologically driven disruptions, require organizations to adopt proactive cybersecurity measures. Understanding the specific methods used by these actors can help mitigate the risks they present. By enhancing defenses, fostering awareness, and collaborating through information-sharing platforms, organizations can improve their resilience against these evolving threats and minimize the potential impact of cyberattacks.
Further Reading
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-290a
- https://www.cybercom.mil/Media/News/Article/2897570/iranian-intel-cyber-suite-of-malware-uses-open-source-tools/
- https://attack.mitre.org/groups/G0069/
- https://www.ibm.com/downloads/documents/us-en/131cf87b20b31c91
- https://www.group-ib.com/blog/muddywater-infrastructure-malware/
- https://www.csis.org/blogs/strategic-technologies-blog/beyond-hacktivism-irans-coordinated-cyber-threat-landscape
- https://www.crowdstrike.com/en-us/blog/who-is-pioneer-kitten/