
Critical Start Vulnerability Prioritization
Identify what to fix first with vulnerability prioritization based on real-world exploit weaponization.
Make Every Vulnerability Scan Actionable
Critical Start Vulnerability Prioritization enriches the data from the tools you already own with expertly curated threat intelligence and customizable asset criticality.
With Vulnerability Prioritization, you’ll fix what matters most, first. Then you can deal with the rest.
What’s Wrong with Vulnerability Scanners Today?
- Lack critical business context, leading to inefficient patching
- Don’t identify which vulnerabilities are being actively exploited by threat actors
- Result in lengthy lists of vulnerabilities that cannot be used to inform leadership of risks without significant manual input and effort
Organizations like yours need a better way to gather actionable data that helps them reduce risk quickly. You need a risk-based vulnerability prioritization solution that...
Gets the greatest value out of the tools you already own by prioritizing and categorizing data in a way that makes sense.
Helps you measurably reduce exposure with scan results enriched with business context, asset criticality, and exploit-aware threat intelligence.
Enhances cross-functional collaboration so that each stakeholder, from implementation to leadership teams, stays informed and ahead of vulnerability-based risks.
Accelerate Risk Reduction with Vulnerability Prioritization
Critical Start Vulnerability Prioritization helps your team overcome the challenges of addressing an overwhelming number of vulnerabilities. By integrating seamlessly with your vulnerability scanning tools and enhancing scan results with threat data, exploitability, asset criticality, and more, you can take decisive action to reduce exposure. With dynamic risk scores assigned to each vulnerability, Vulnerability Prioritization accelerates patching efforts, improves vulnerability reporting, and provides metrics that prove risk reduction across the organization.
Your Tools, but Better
Get better scan results with actionable vulnerability prioritization, generated daily from the vulnerability management tools you already have in place.
Actionable
Replace volumes of unprioritized scan data with actionable insights.
Repeatable and Transparent
Set your schedule for vulnerability scans and deliver results directly to stakeholders through your workflows and ticketing tools.

Timely
Know which systems are at the greatest risk of exploitation with timely insights into weaponization intelligence.
Integrated
Connect your Vulnerability Management tools with the Critical Start platform using your credentials and start scanning.
Collaborative
Give each stakeholder the data they need to understand what’s at risk and make informed decisions with confidence.
Impactful
Easily identify, prioritize, and patch vulnerabilities with the biggest impact based on known weaponization, ransomware attacks, exploit kits, APTs, and more.
Measurably Reduce Exposure
Decide, Respond, and Communicate with Confidence
How do you know which vulnerabilities to patch first to reduce risk? If you’re like most security leaders, you rely on CVSS scores and do your best to patch critical assets. There is a lot of dangerous guesswork involved.Start Vulnerability Prior
Knowing which vulnerabilities are present in your environment isn’t enough. You need an efficient and effective way to communicate with IT teams and app owners so that they know what they need to fix, why it’s important, and how to remediate.
Vulnerability Prioritization gives cross-functional teams a single source of truth for prioritized vulnerability data so your cross-functional teams can communicate faster and make impactful decisions with confidence.
Prioritized vulnerability remediation is a highly efficient strategy that significantly reduces the potential for breaches or incidents. Here’s how it works:
PLATFORM
RISK PRIORITIZATION
ASSET CRITICALITY
PLATFORM
The Critical Start platform continuously monitors and analyzes data from connected vulnerability management tools and applies risk scoring and prioritization. Scan results are enriched by threat intelligence, including vulnerability weaponization, zero-day threat activity, exploitability, exploit probability, and more.
RISK PRIORITIZATION
You can tag and group assets according to location, function, owner, or business impact, and assign weights based on asset importance. Vulnerability Prioritization automatically adjusts risk scores of vulnerability findings to reflect the potential impact of each vulnerability on the organization.
ASSET CRITICALITY
Daily asset criticality computations keep you up to date with your attack surface. Automated and continuous analysis of vulnerability and contextual information from external sources (threat intelligence, exploit databases, patch availability, etc.) all contribute to accelerated and improved vulnerability prioritization
See why vulnerability management is a critical component of guarding against cyber threats
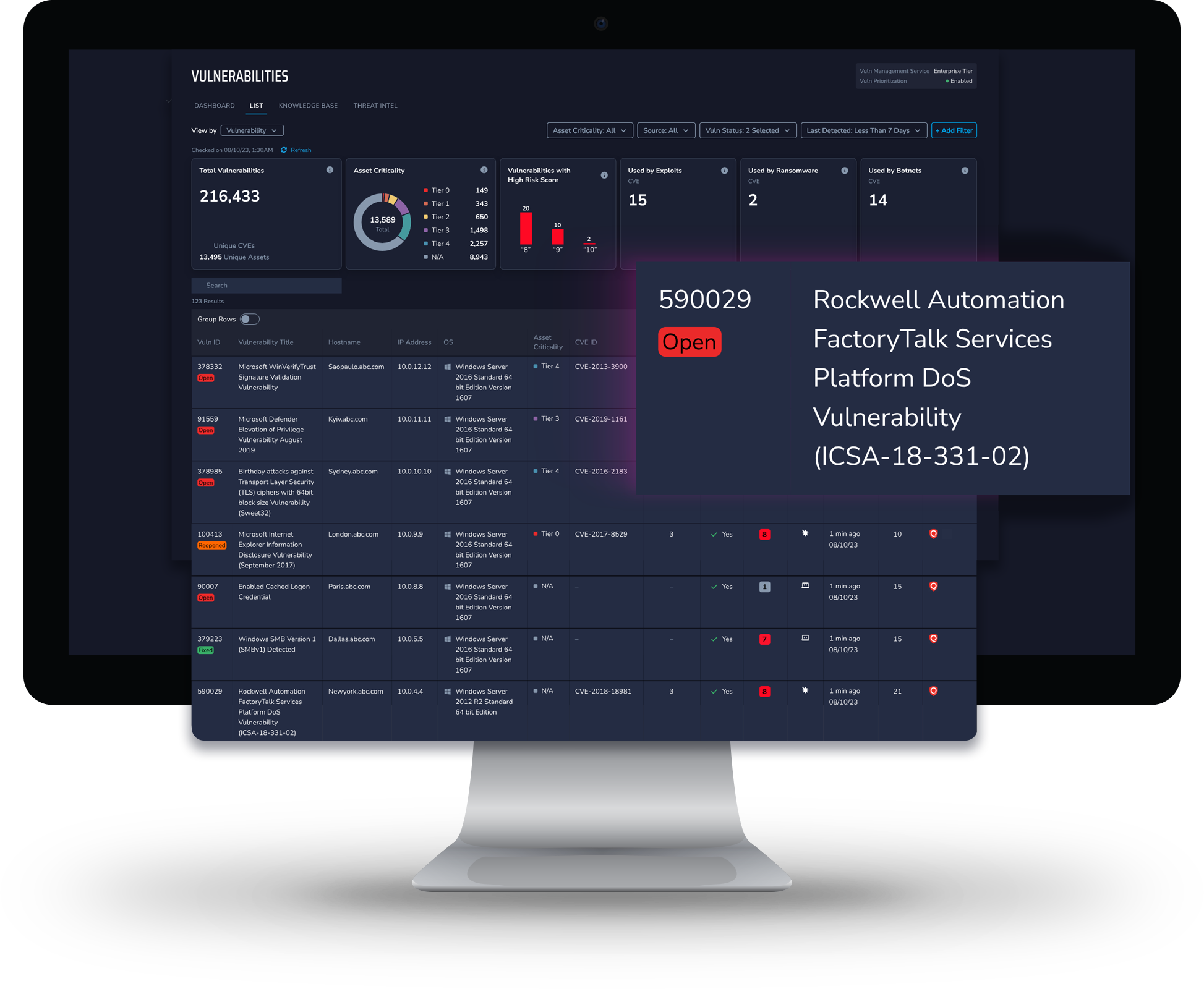
View By Vulnerability
Simplify vulnerability management with an enriched view of host and vulnerability information. Each row clearly represents CVE and non-CVE vulnerabilities along with asset criticality, risk scores, number of weaponized CVEs, detection dates, aging data, and more.
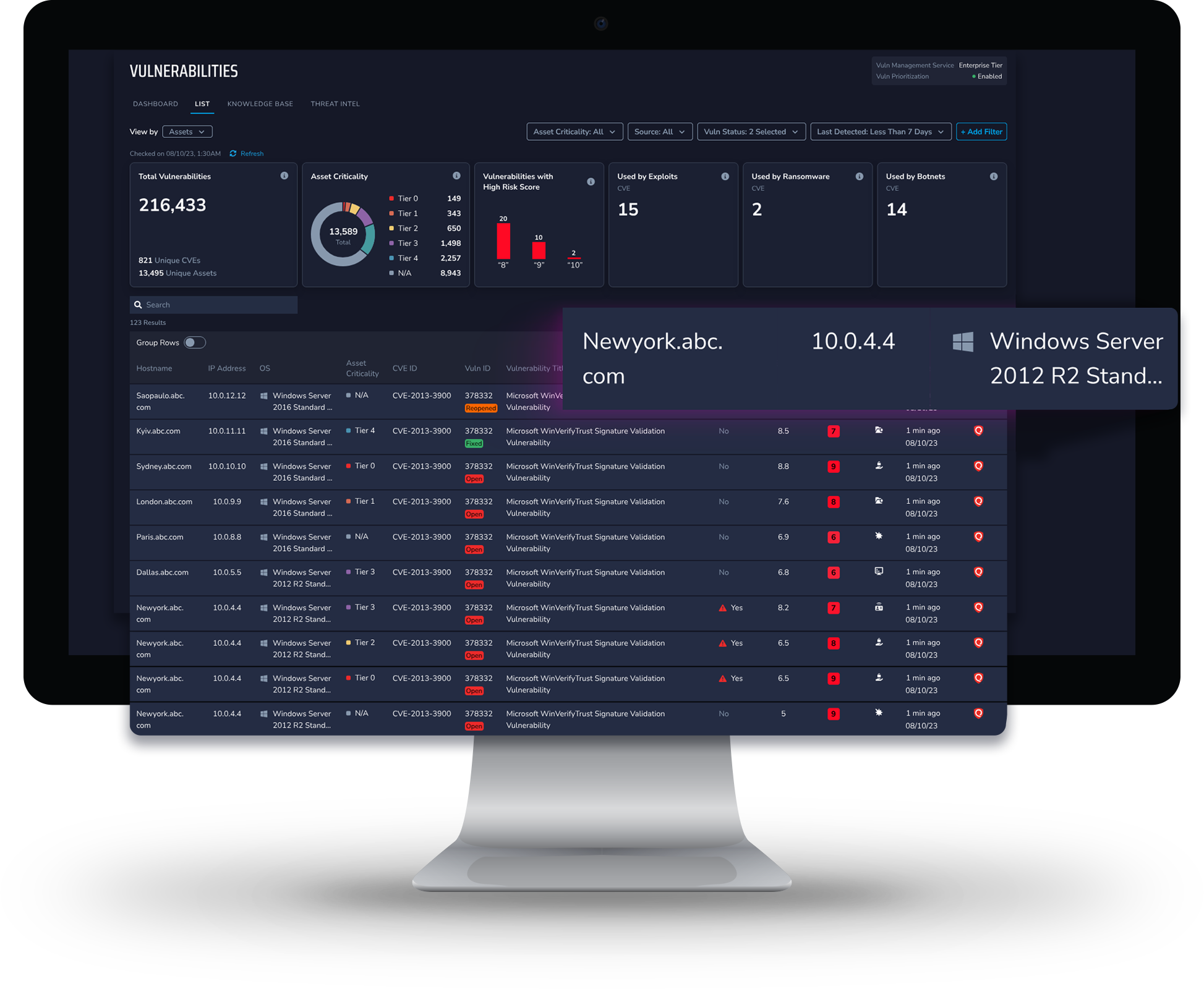
View By Asset
Remediate with confidence with this asset-centric view that shows prioritized findings by asset. In the grouped view, you'll see asset data from all vulnerability management sources, including the total number of vulnerabilities and CVEs, weaponized vulnerabilities present, and risk scoring that lets you determine what assets to patch first for the greatest impact.
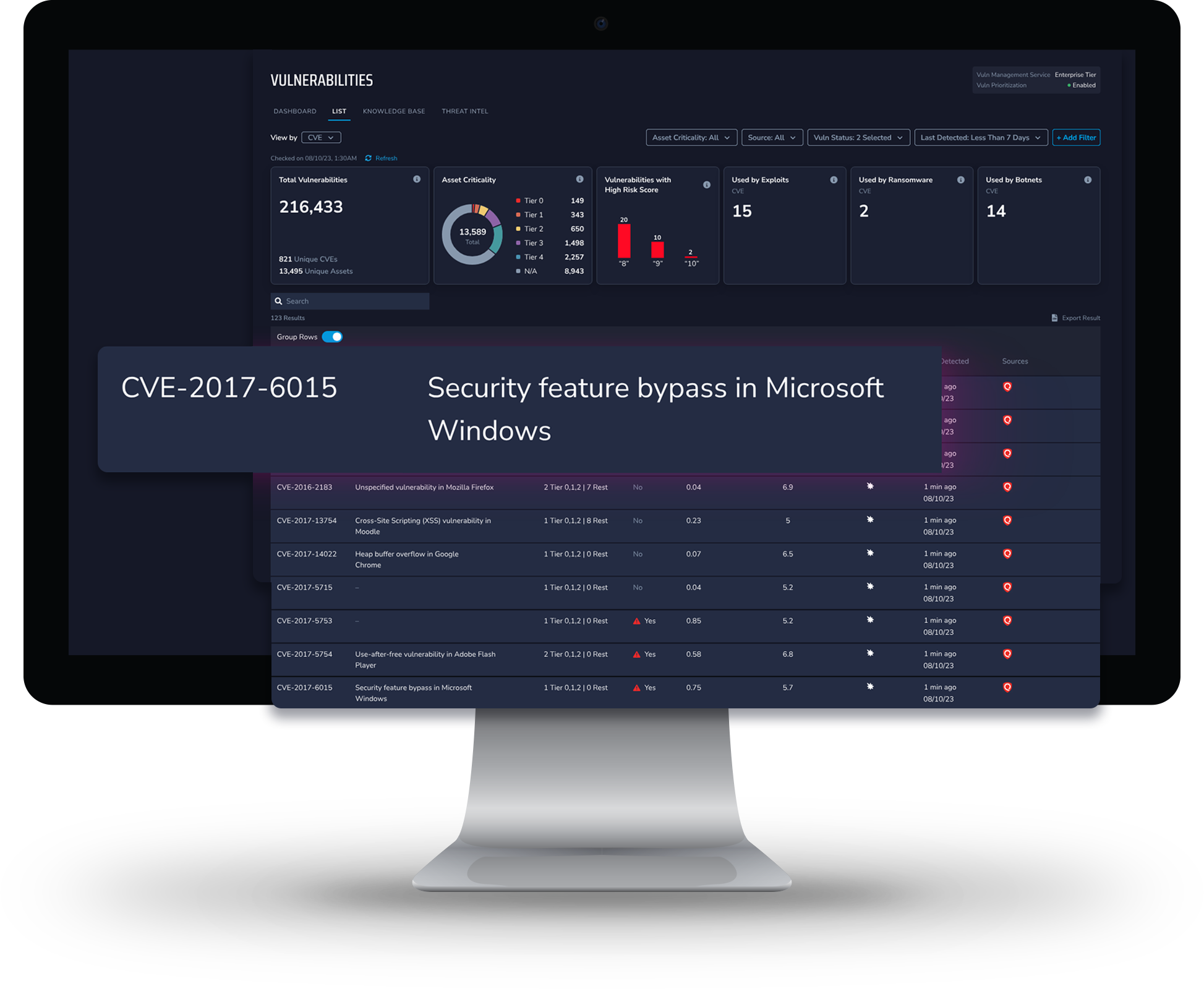
View By CVE
Gain an advantage over would-be attackers with a CVE view that shows you prioritization based on risk scores, exploitability, weaponization, ransomware use, and more. With this view, you can make critical decisions that inform next steps to protect your most valuable assets, and communicate with operations and management teams to ensure cross-team collaboration and unified efforts.
Choose Your Path to Vulnerability Prioritization
No two organizations are alike. Whether you need the complete cyber risk monitoring, posture and event analytics, and response orchestration of our industry-leading Managed Detection and Response (MDR), or you want a stand-alone, turnkey Vulnerability Management Service (VMS), we have you covered.





