Blogs

TLP CLEAR // [CS-SA-26-0102] Iranian Cyber Threat Activity on U.S. Financial Institutions
Executive Summary
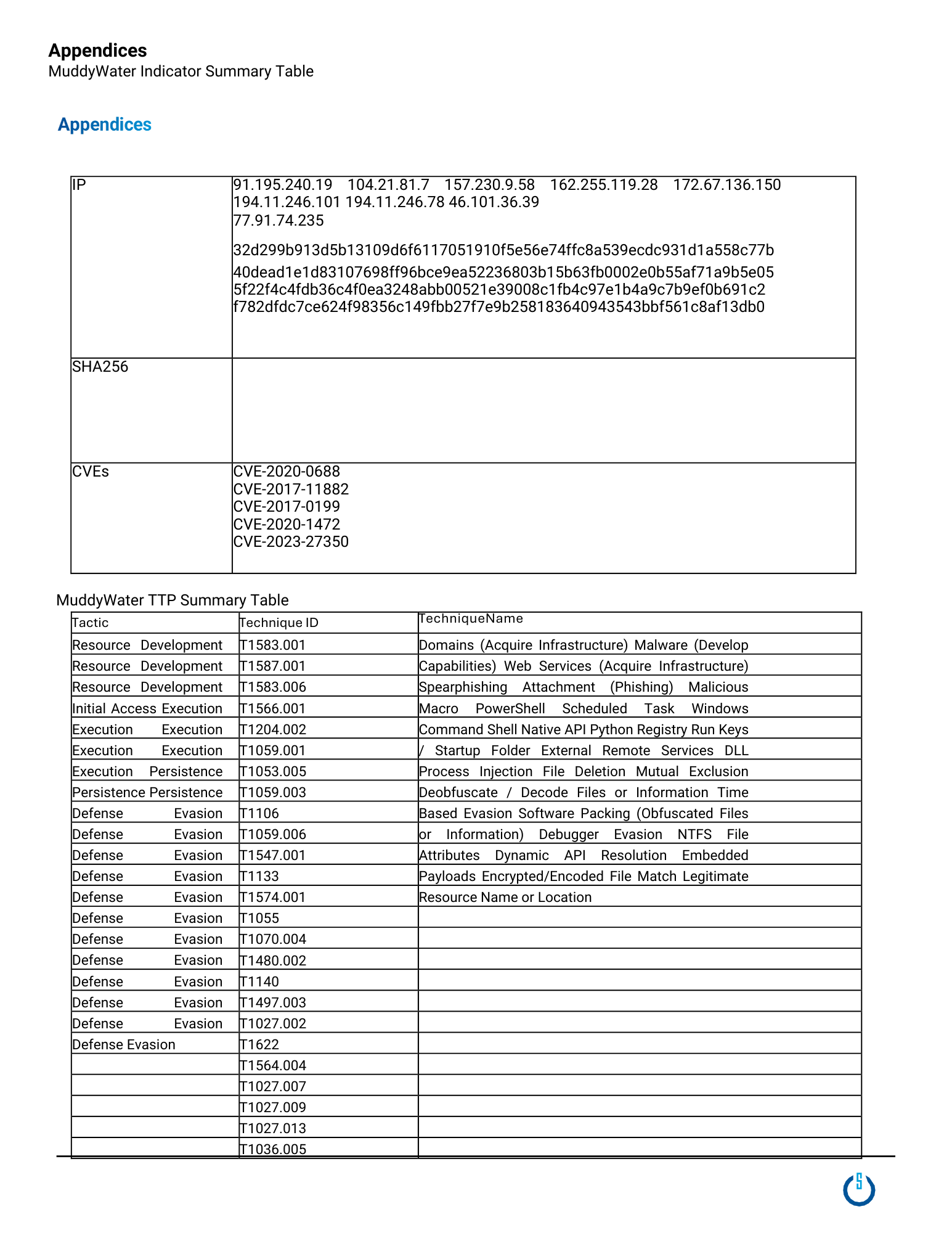
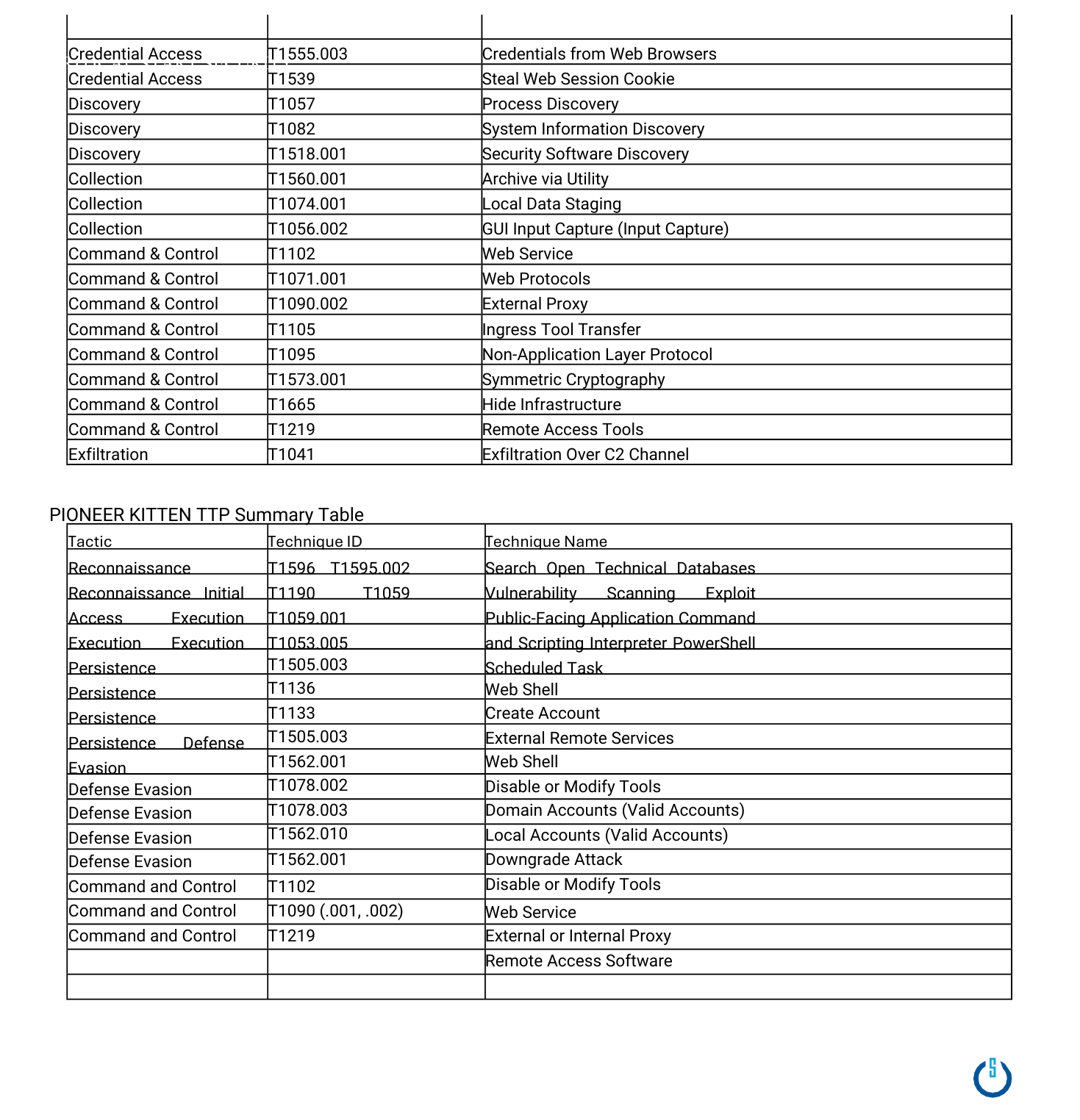
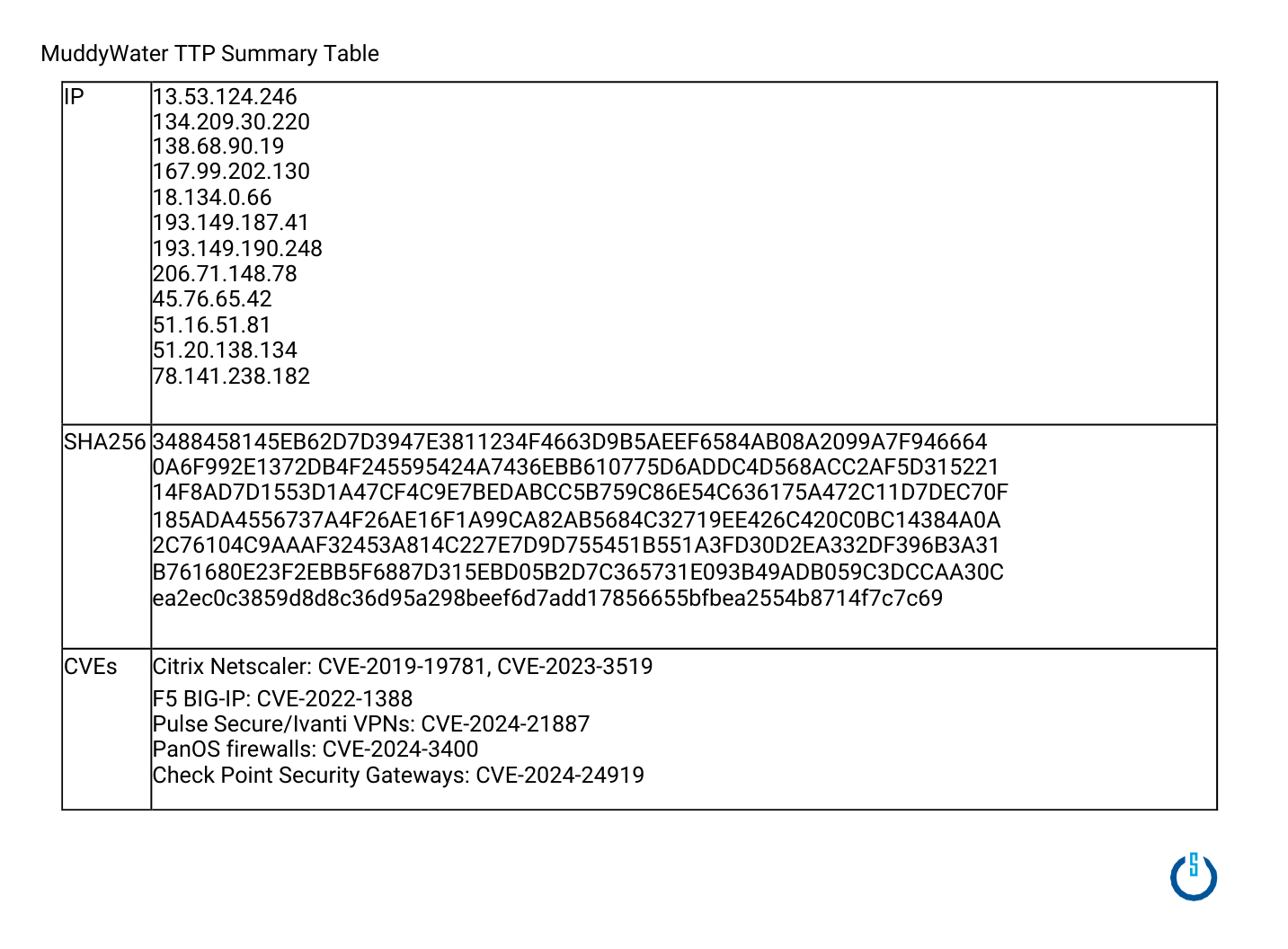
Geopolitical relations and tensions significantly impact cyber threat activity, as state-aligned cyber groups often escalate operations in response to regional conflicts, sanctions, and shifts in foreign policy. As tensions between the U.S. and Iran remain high, the risk of cyberattacks targeting U.S. organizations is on the rise.
,
 ,
,
 ,
,

CRITICALSTART® Threat Research TLP WHITE // [CS-TR-26-0101] Geo-Political Tensions Exploited for Cyberattacks
Executive Summary
Geo-political events increasingly shape the cyber threat landscape. State and non-state actors capitalize on periods of political tension to advance strategic objectives through cyber operations, often targeting governments, critical infrastructure, private enterprises, and civil society.

CRITICALSTART® Security Advisory: TLP AMBER // [CS-SA-26-0101] Strategic Phishing Campaigns Leverage CAPTCHA and Email Routing Misconfiguration
Executive Summary
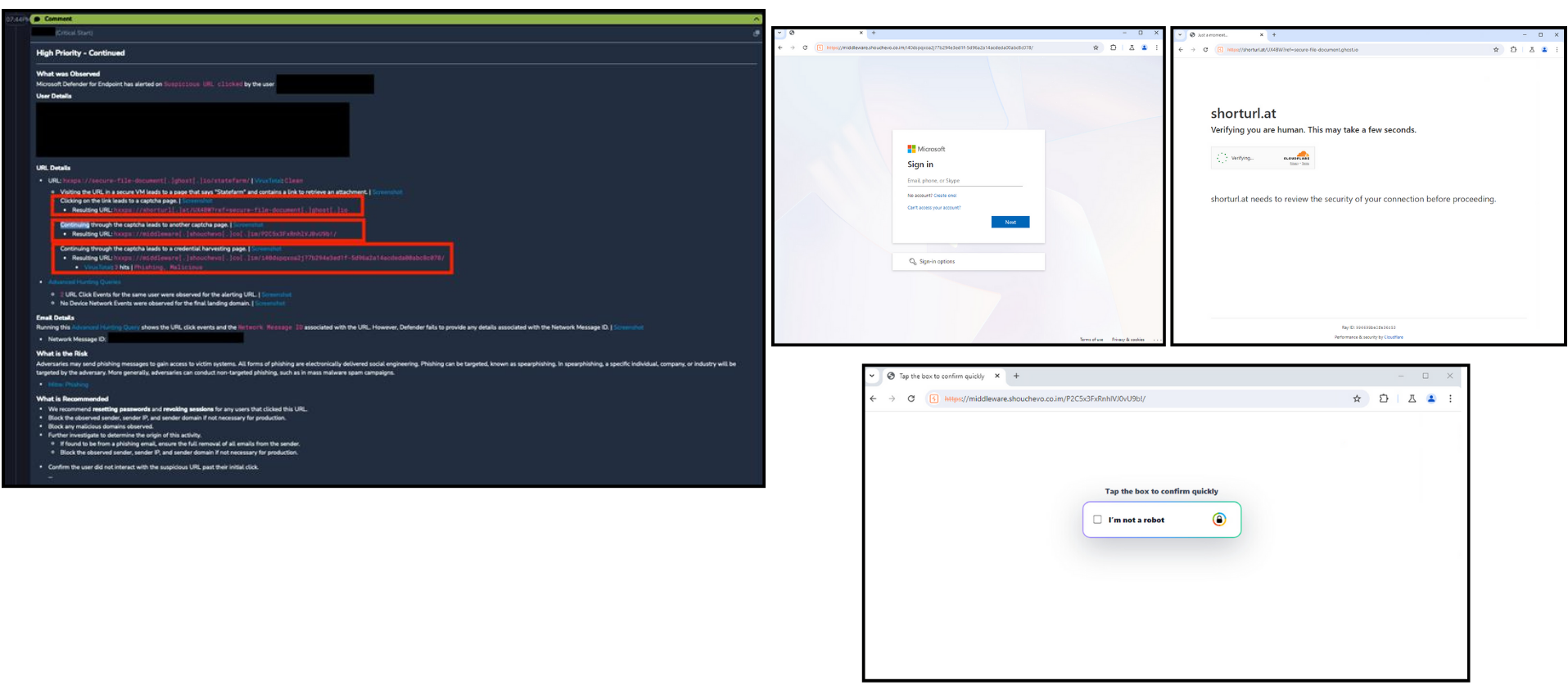
Critical Start is tracking an increase in advanced phishing attacks that move beyond simple links and attachments delivered via email. These campaigns rely on layered social engineering and alternative delivery techniques to gain initial access, with primary activity centered on fake CAPTCHA pages, phishing messages that appear to originate from inside the organization, among others.
, ,
,
,

MDR for Outcomes: Moving Past Alerts to Real Results
If you’ve ever felt like your MDR provider just hands you a pile of alerts and says, “Good luck!”, you’re not alone. That’s one of the big realities Umair Masud of Critical Start and Joe Campbell of Verinext tackled head‑on in our recent Fireside Chat: MDR for Outcomes.
And if you missed it live, don’t worry — you can watch the replay on demand (trust me, you’ll want to).

Security Snapshot: The One Click That Costs a Fortune (And How We Stop It)
The biggest security risk to your company isn't a zero-day exploit; it's a well-worded email. Phishing is the engine of cybercrime, the initial spark for over 78% of security incidents. Attackers are targeting industries like Banking & Finance (17%) and Manufacturing (13%) because they know one successful phish can unlock a treasure trove of data and access.
They aren't just looking for passwords; they're looking for a way in.
Enter Critical Start MDR. Here’s the deal:

Beyond Alert Fatigue: Why Your MDR Provider Needs to Prove Real Outcomes
Is your security team drowning in alerts? If you're tired of watching threats slip through while your analysts chase endless false positives, you're not alone. But the problem might not be what you think.

Security Snapshot: How Attackers Are Bypassing Your MFA (And How We Stop Them)
Think your MFA is a silver bullet? It’s not. Attackers are now sidestepping it entirely, and they’re targeting industries like Insurance (75% of orgs hit), Consulting (40%), and Construction (32%). They aren’t just stealing passwords; they’re hijacking entire user sessions, giving them the keys to your kingdom. It’s a silent, sophisticated threat that leaves your team in the dark.
Enter Critical Start MDR. Here’s the deal:

WEBINAR RECAP: The Biggest Threat Shifts of 2025 (So Far)
What security leaders need to know from the Critical Start H1 2025 CTI Report
The first half of 2025 brought major changes in how, when, and where attackers operate. If your threat models haven’t been updated yet, well, there’s no time like the present.

Why Traditional MDR Is Failing — and What Best-in-Class Looks Like
The $10,000-Per-Hour Question
Security teams today face a frustrating paradox: despite millions invested in tools, analysts still drown in noise.
Randy Watkins, CTO at Critical Start, and Tim Bandos, VP of Presales Engineering at Critical Start, tackled this head-on in our latest webinar. Bandos shared how downtime at DuPont (where he was VP of Cybersecurity) could cost $10,000 per hour, making missteps in detection and response not just risky, but potentially catastrophic.

Human-Guided Machine Learning: A Different Approach to Alert Fatigue
Chris Carlson explains why the Critical Start MDR platform favors determinism over autonomy at a time when cybersecurity vendors are rushing to bolt generative AI into every product layer.
In a recent interview with ISMG at Black Hat 2025, Carlson, Chief Product Officer at Critical Start, described how the company is tackling alert fatigue, reducing false positives, and supporting SOC analysts without handing over critical decisions to AI.

If "R" Stands for Response, Then Show Me the Response
That’s the argument Randy Watkins, CTO of Critical Start, made during a recent interview with Dark Reading at the Black Hat USA 2025 News Desk. In his view, the "R" in MDR is where everything falls apart.
"Response is a fairly ambiguous term. We see response meaning everything from actual containment of threats to escalation of alerts in different scenarios. They're both warranted, but what we really want to do is better set expectations of what customers are going to get."

Drowning in Alerts: How to Cut the Noise and Focus on Real Threats
92 percent of organizations say they’re overwhelmed by an endless sea of alerts.
It’s not just annoying. It’s dangerous.
In a recent Dark Reading Webinar hosted by contributing editor Terry Sweeney and featuring Critical Start Field CISO Tim Bandos, security leaders got a behind-the-scenes look at how top teams fight back against alert fatigue and focus on what matters most: stopping real threats.





