
Critical Start MDR for Operational Technology (OT)
Protect your industrial operations from escalating cyber risks.
IT/OT convergence is putting critical processes at risk. We can help.
“Air gapping” IT and OT systems isn’t sufficient to prevent a threat actor from reaching from one critical system to another, and the detection and reporting of cyberattacks in Operational Technology (OT) and Industrial Control Systems (ICS) environments can’t rely on OT system monitoring alone.
Get Practical Security Steps For Industrial Operations
How are you protecting your OT systems and the IT networks that affect them?
Critical Start Managed Detection and Response (MDR) for OT provides the network visibility you need across your OT systems to protect your industrial operations from cyber threats.
Leveraging your existing infrastructure and security tools, we deliver cost-effective protection for your industrial operations with 24x7x365 monitoring, threat detection, and response across your IT and OT environments.
Gain visibility and reduce risk across your OT environment
End-to-End Visibility Across IT/OT Environments
Broad visibility enables your industrial organization to detect and respond to threats across your entire infrastructure
Real-Time Collaboration
Our native MOBILESOC® mobile app enables instant communication between OT teams and our security analysts for rapid threat response
Scalable & Adaptable for Evolving OT Security Needs
You can start monitoring your OT environment, even without dedicated OT security tools
Customizable Alerting & Escalation Workflow
Read-only visibility prevents unauthorized changes to operational processes and ensures the right personnel are informed of potential threats in a timely manner
24x7x365 Monitoring & Response Support
Our Security Operations Center (SOC) analysts provide around-the-clock monitoring and response support to reduce the burden on your internal security teams
Differentiated IT/OT Threat Detection & Response Handling
Separate IT and OT alerts, threat detection, and response actions, plus adapting to different levels of network segmentation, provide a tailored and flexible approach to OT threat monitoring and response
How it works
- We collect and analyze log data from your existing:
- OT data sources, such as Windows hosts, firewalls, switches
- IT data sources, such as EDR/EPP solutions
- OT-specific security tools (if available), including Dragos, Claroty, Nozomi, Otorio, Armis, Microsoft Defender for IoT, etc.
- Our Cyber Operations Risk & Response™ (CORR) platform ingests this data, correlates it with threat intelligence, and identifies potential security incidents
- Security analysts with read-only visibility into your OT environment investigate alerts and notify your experts of threats based on customized alerting workflows
- Incident response is performed according to predefined OT Rules of Engagement to ensure operational integrity
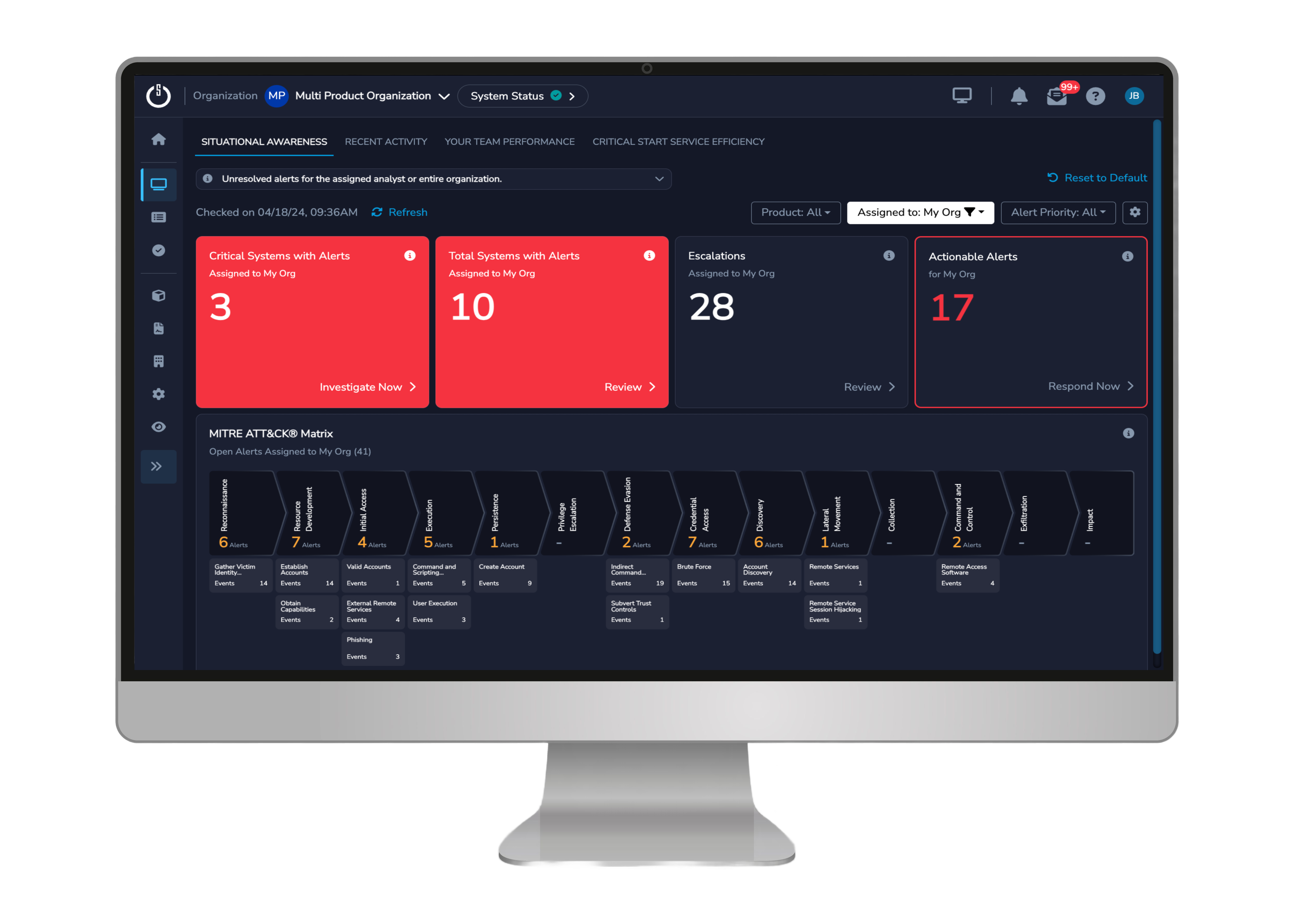
How we’re different
Whether you are just beginning your OT security journey or looking to augment an existing program, now you can reduce the risk of disruption and get the visibility you need across your critical systems.
Critical Start MDR for OT provides the adaptable, scalable solution you need to protect your industrial operations with an end-to-end security solution that enables risk management and reduction through OT-specific threat analytics, with or without dedicated OT security tools.
Ready to take the first step towards defensible industrial operations? With MDR for OT you can:
Augment your investment in OT security monitoring and prevention
Use predictable pricing and 24x7x365 threat monitoring, detection, and response to help reduce financial and operational risks associated with cyberattacks targeting industrial environments.
Bridge the gap across OT security tools and resources
Leverage increased OT visibility and a team of experienced security professionals ready to notify you when suspicious activity is identified to help overcome the absence of dedicated OT security tools and the lack of in-house resources.
Simplify the complexity of converged IT/OT security management
Increase risk resilience with a unified approach that addresses the growing complexity of managing IT/OT convergence to ensure the safety, reliability, and compliance of your industrial processes.
Choose your service tier
Base Service Tier
Enhance your risk resilience and achieve OT monitoring and threat detection using existing infrastructure and IT security tools without the burden of investing in additional security resources
Extended Service Tier
Adds support for dedicated OT security tools like Dragos, Claroty, Nozomi, Otorio, Armis, Microsoft Defender for IoT, etc., for deeper visibility





