Blogs

Secure the Cloud—All Hands on Deck
The cloud is storming. There has been intense surge of cloud adoption in businesses throughout every vertical over the past year, but I believe this astonishing trend is only the beginning. I feel that a massive, measured adoption of the cloud will continue, but—perhaps even more shockingly—without the security planning, controls, tools, and skillsets that would be considered standard when protecting a traditional technology infrastructure.

Women in Cybersecurity: Katy Lietzau
Katy Lietzau, Director of Channel for the Central Region at CRITICALSTART, believes in the power of a good conversation within the partner community.

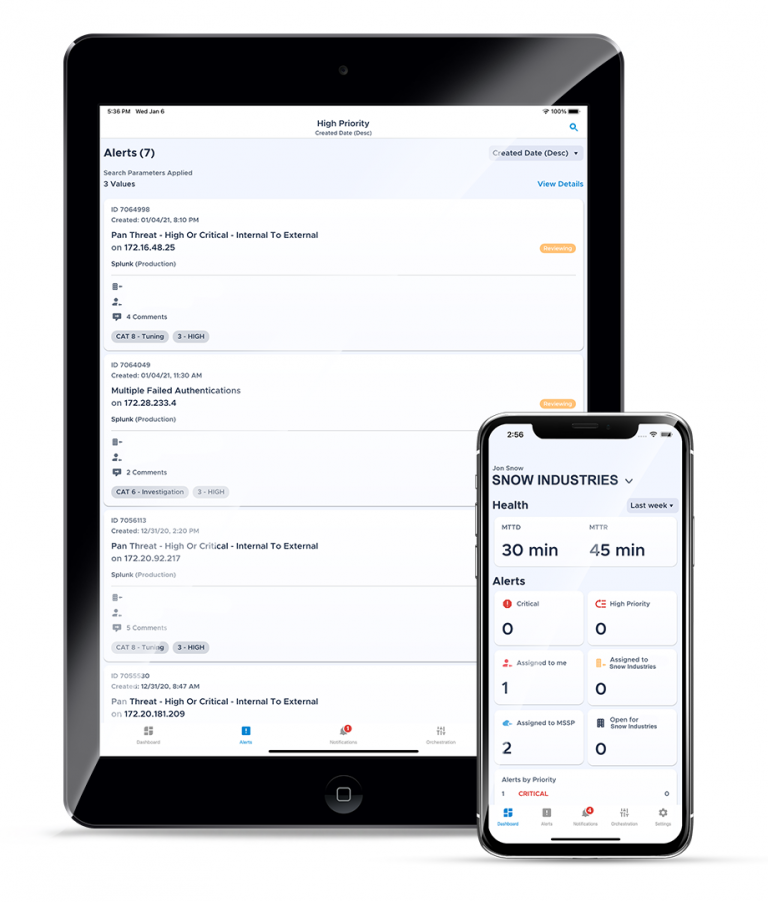
MOBILESOC: You’ll Take this Threat Alert to Go.
Smoked brisket, poached eggs, sliced tomatoes, and sourdough toast—it’s the brunch you’ve been waiting for all week. It’s weekend perfection…right up to the moment when you’re notified that your business — the one you’re charged to protect — is under cyber-attack.
At this point, your day can take one of two directions.

Zero-day Targeting Exchange Servers: Steps to Evaluate the Risk to Your Organization
By: Charlie Smith & Travis Farral
A zero-day has been announced targeting Exchange Servers. If you are running on-premises Exchange Servers within your environment, public facing or in a hybrid configuration, stop what you are doing, finish reading this article, and patch your Exchange Servers immediately!

The Top Three Issues Robbing You Of SIEM ROI
Upon inception, the function of the Security Information and Event Management (SIEM) was to aggregate log data collected from a variety of sources across an organization. With the data centralized, the next generation of the SIEM leveraged detection logic, or rules, to generate alerts under given conditions.

Earning Your Business is Good. Earning Your Trust is Better.
The impact a company culture has on delivering value
Company culture might feel like a touchy-feely, softer side of a business. Not necessarily something that business leaders would prioritize with regards to competitive advantage or gross margin. However, as a CEO, I have come to find that the most important decisions I make are around the type of culture we have in the company, how we compete, and how we win.

Formidable Style

Navigate Aftermath of SolarWinds Attack With On-Demand Resources
The SolarWinds cybersecurity breach, also known as Sunburst, has made global headlines for its duration, impact, and high-profile targets. After going undetected for months, the news in December 2020 of the nation–state attack was the holiday surprise no one wanted.
CRITICALSTART takes a closer look at the SolarWinds breach through two January information sessions, both available on demand:

Data Privacy Program from Zero to Hero
As I promised last week, here’s a short article on Developing and Implementing a Data Privacy Program. I hope you will like it and share it with your teams and colleagues.

Balancing Act: How MOBILESOC can Ensure Cybersecurity while Protecting Time with Family
By Tommy Scott, Senior Security Consultant | CRITICALSTART

Windows Security Event Logs – What to Monitor?
The following is a table of event codes that I’ve found to be extremely valuable to log and monitor in an environment. Some trend more towards general environment health and activity monitoring, however they all have a foothold in security value as well. As always, your environment’s needs and requirements will be different depending on a multitude of other factors such as compliance and log retention, and these should be taken into consideration when choosing what to log – and for how long.

How To Reverse Engineer the SolarWinds Hack
Author: Quentin Rhoads-Herrera, Director of Professional Services





