Security Snapshot: How Attackers Are Bypassing Your MFA (And How We Stop Them)
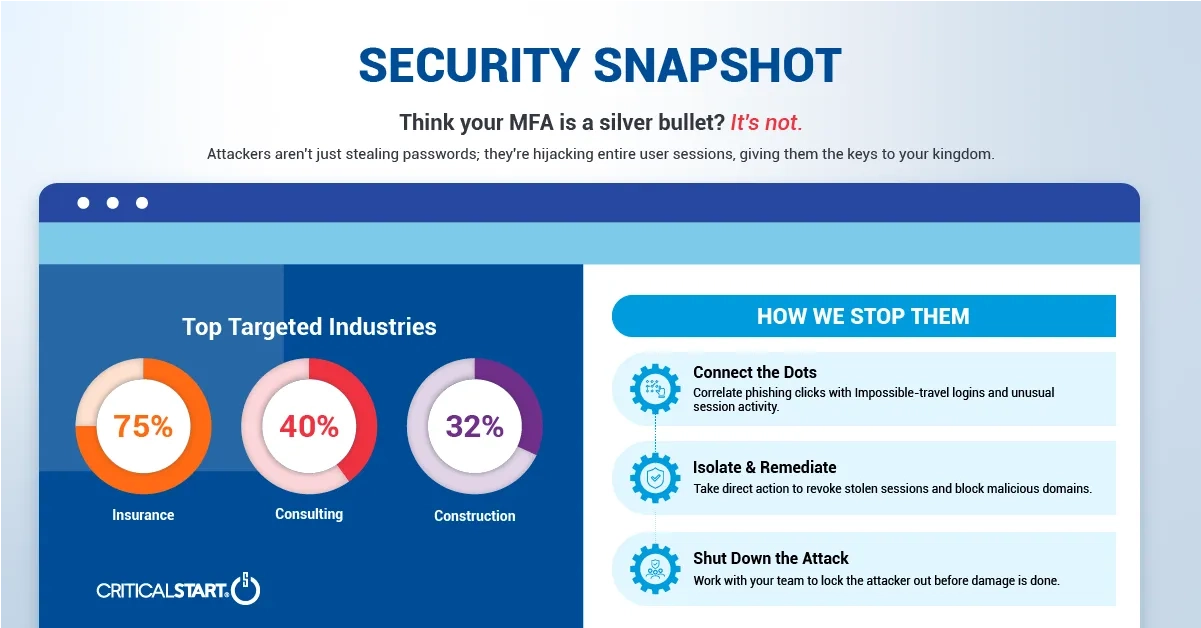
Think your MFA is a silver bullet? It’s not. Attackers are now sidestepping it entirely, and they’re targeting industries like Insurance (75% of orgs hit), Consulting (40%), and Construction (32%). They aren’t just stealing passwords; they’re hijacking entire user sessions, giving them the keys to your kingdom. It’s a silent, sophisticated threat that leaves your team in the dark.
Enter Critical Start MDR. Here’s the deal:
- The New Threat: Adversary-in-the-Middle (AitM) isn’t your average phishing scam. Attackers use reverse-proxy sites to intercept everything in real-time, including the one-time code you just entered. They grab the session cookie and walk right into your network as a legitimate user.
- Phishing on Steroids: Over 63% of these attacks start with a simple phishing email. The link looks legit, the login page is a pixel-perfect copy, but it’s all a front for the attacker to steal your session.
- Critical Start MDR: Our 24x7x365 SOC spots the subtle clues others miss. We see the phishing click, the impossible-travel login that follows, and the unusual session activity. We connect the dots when your other tools just see isolated events.
- Shutting It Down Fast: When an AitM attack is detected, our SOC analysts don’t just send an alert. They investigate, confirm the threat, and take immediate action — revoking the stolen session, blocking the malicious domain, and working with your team to lock the attacker out before they can exfiltrate data or move laterally.
The result? Instead of discovering a breach weeks later, the attack is stopped in its tracks. No widespread damage, no lengthy investigation, no drama.
Don’t let attackers turn your best defense into a backdoor. Learn how to stay ahead of the threat. Get the full report from your customer success manager or email [email protected].






