AI Accelerated.
Human Validated.
MDR Built for Confident Response.
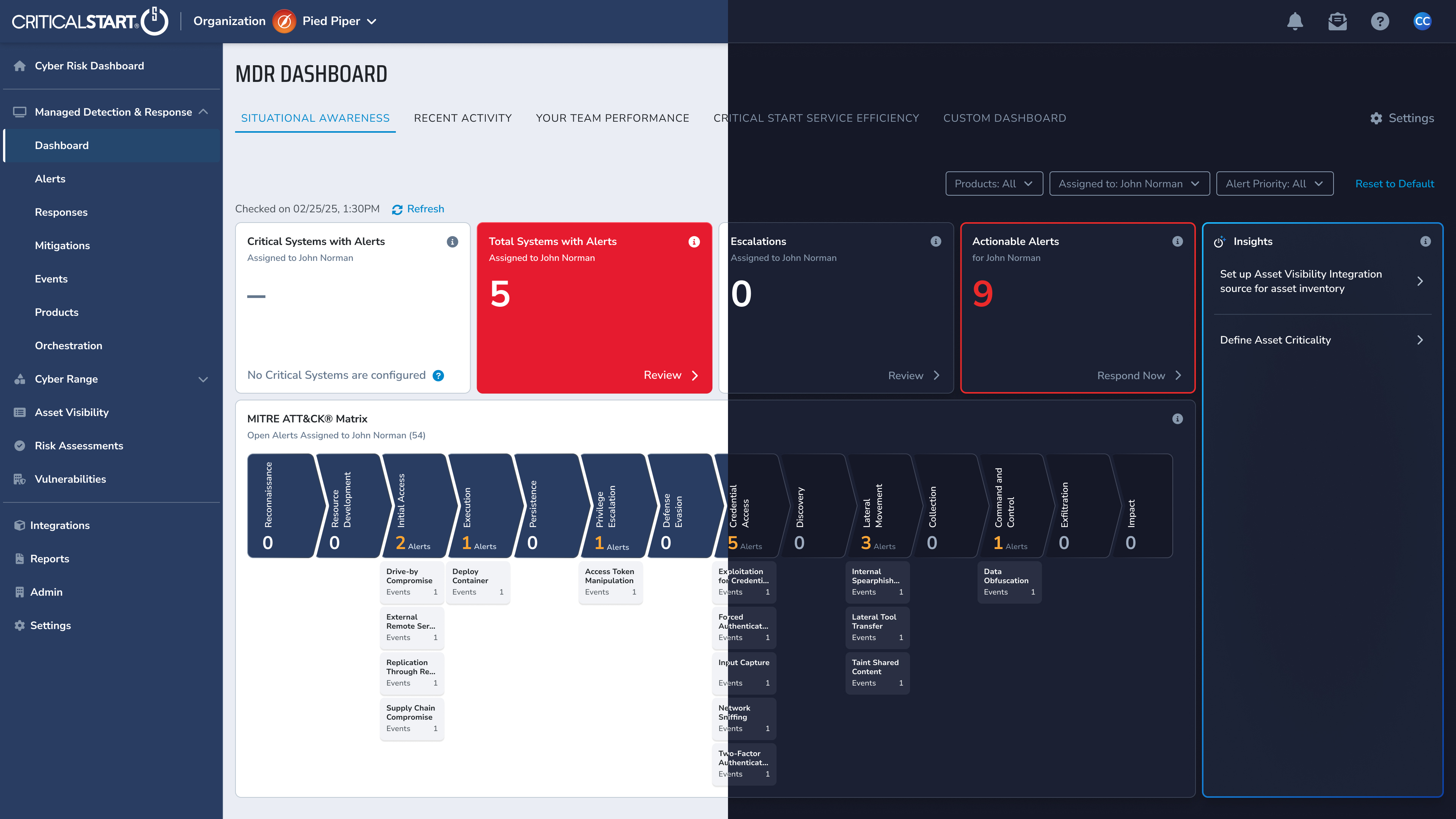





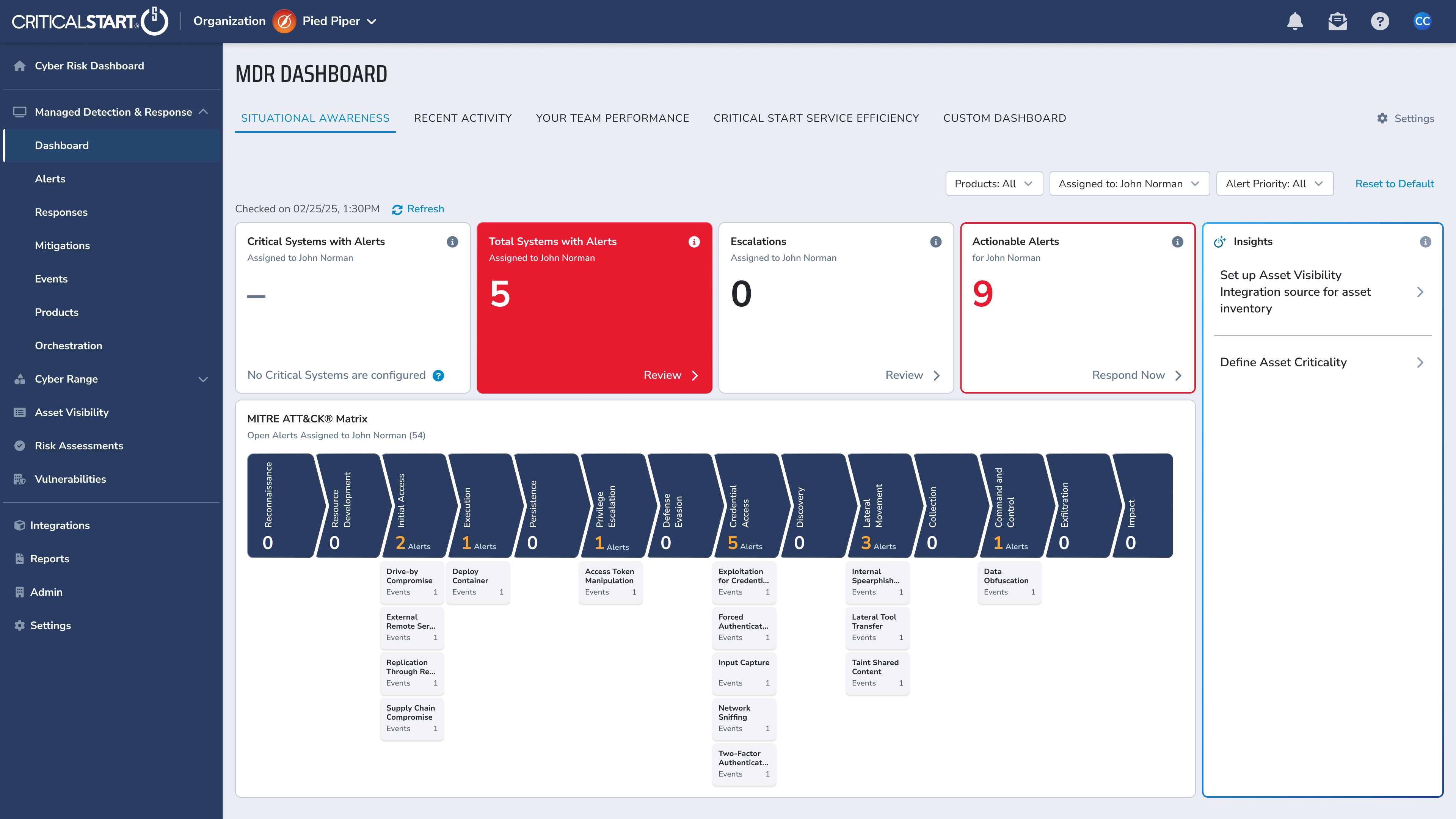
Intelligent Automation Where It Helps. Human Judgment Where It Matters.
Critical Start combines AI-assisted analysis with expert-led investigation to reduce noise, accelerate time to insight, and confirm real threats regardless of vendor alert severity.
Complete Signal Coverage
Human-Driven Investigation & Response
Flexible Deployment Models
Asset Visibility and Criticality Ratings
Ensure your Security Operations Center (SOC) receives all expected threat telemetry by addressing EDR and vulnerability coverage gaps and monitoring log ingestion.
Learn More88.5k
Potential attacks stopped in their tracks by our security experts
Swift, accurate threat resolution with two-person integrity verification, backed by contractual SLAs and delivered 24x7x365.
Learn More136K
Human-Driven / Nuanced Analysis
Reduce alert fatigue with tailored response strategies adaptable across multi-vendor solutions, IT and OT threat types, and log sources.
Learn More1.19B
Security events detected across hundreds of integrated technologies
Maintain an accurate inventory of critical assets and prioritize security efforts based on business impact.
Learn More99.83%
Of alerts identified as false positives
Built for Modern Security Operations
- AI-assisted detection across modern security product stacks
- Human-validated investigations by experienced analysts
- Defined response workflows aligned to severity and customizable ROEs tailored to your organization's needs
- Contractual per alert response SLAs that keep performance measurable
- Continuous performance reporting for full transparency
- A partner you can count on when it matters
Integrations
Get more value from your tools as Critical Start analyzes alerts and telemetry across multiple products to stop threats before impact.
Don’t Just Take Our Word for It.
Our customers say it best. The world’s most renowned global enterprises, across industries like finance, healthcare, and manufacturing, trust CRITICALSTART® to deliver unmatched Managed Detection and Response (MDR). See why their experiences set us apart and how our solutions consistently outperform the competition.
Trusted Behavior Registry®(TBR®)
The TBR is a deterministic automation engine that continuously establishes and verifies known-good behavior across your environment to resolve false positives and surface what deviates. With the noise removed, our analyst team investigates every threat alert, regardless of vendor severity, to identify and respond to threats in your environment with clear communication, consistent ownership, and a partnership your team can rely on.
Critical Start
MOBILESOC®
MobileSOC gives security teams rapid response on the go with native iOS and Android apps that support collaborative investigation and containment from your phone, helping you act fast and stop threats wherever you are.
Contractual Per Alert Response SLAs
Our contractual response SLAs bring confidence to daily operations with less than 60-minute per alert Time-To-Respond (TTR) and less than 10-minute notification for critical alerts, so response stays fast, visible, and measurable.

See What Confidence in Your MDR Looks Like
See how Critical Start delivers confident response through AI-accelerated detection, human-validated investigation, and clear, measurable execution.
- Clarity Into What Matters: Reduce noise and get clear action on the alerts that require response.
- Contractual Response Accountability: Less than 60-minute per alert Time-To-Respond (TTR), for critical alerts.
- Trusted Baseline, Faster Triage: The Trusted Behavior Registry (TBR) Agent verifies known-good behavior first so true risk stands out faster.
- Transparent Performance You Can Prove: Ongoing reporting and visibility into response performance so your SOC can track what is happening and improve with confidence.






