How much risk
are you accepting?
Alert suppression opens you up to risk. Low and medium priority alerts introduce threats that can wreak havoc on your company.
Alert suppression opens you up to risk. Low and medium priority alerts introduce threats that can wreak havoc on your company.
Input values specific to your organization and get custom results.
Our MOBILESOC is an iOS and Android app that goes beyond a simple ticketing app. MOBILESOC makes it possible to detect, triage and remediate every alert no matter what time of day or where you are.
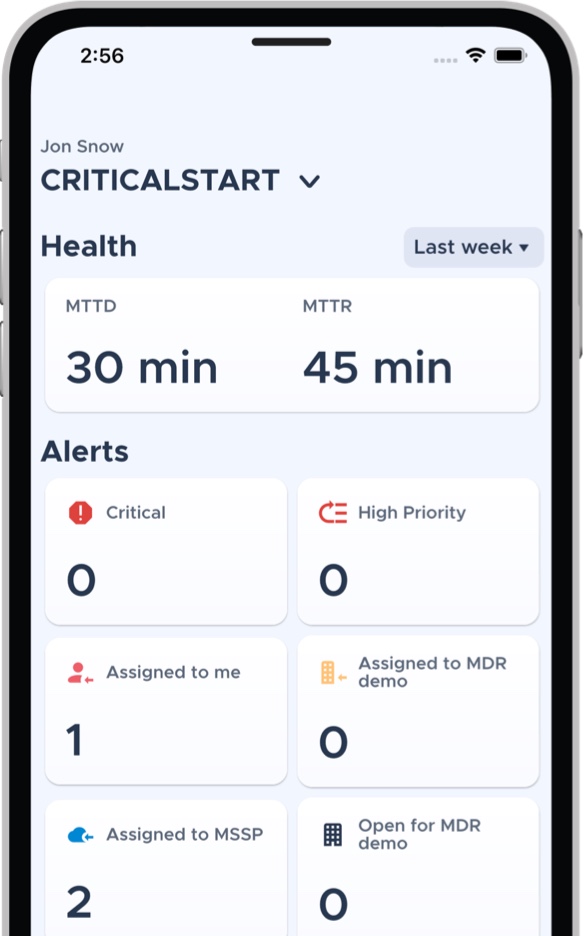


We deliver an MDR that resolves all alerts, stops breaches, saves analysts time and offers complete transparency and fleixibity.

The rise of eLearning and mobility has enabled education to happen across an ever-expanding environment. New MDR thinking delivers full-spectrum visibility for state educational networks.

In this paper, you will learn how it provides far better visibility into threats and enables an active, real-time response to mitigate any impact.

I would say that prior to the relationship with Critical Start, my SOC analysts were experiencing what we all call alert fatigue. Critical Start has really been able to reduce those alerts… I’ve been able to take our level three and four analysts and put them back to work at what they were hired to do.

Our team of highly trained cyber-security professionals provides expertise in technology, adversarial engagements, risk and compliance, privacy and more.

As a trusted advisor, we analyze our customers’ security problems and present a plan that leverages the solutions of our product partners and only recommend best-in-class solutions.


