CRITICALSTART® Vulnerability Management Services
Relieve the burden of vulnerability management and set your security and operational teams up for success.
Relieve the burden of vulnerability management and set your security and operational teams up for success.
Effective Vulnerability Management at Scale
Critical Start turnkey Vulnerability Management service, built on top of Qualys VMDR, simplifies the process of finding and prioritizing vulnerabilities, no matter how complex your environment.
Then we go one step further: we give you precision patch lists so that you can make the greatest impact in the least amount of time.
Overwhelmed by volumes of vulnerability scanner data, CVSS scores that all read “critical”, and scanner profiles that don’t keep pace with your IT operational landscape? Do you feel like you can’t get ahead of cyber risks? You’re not alone.
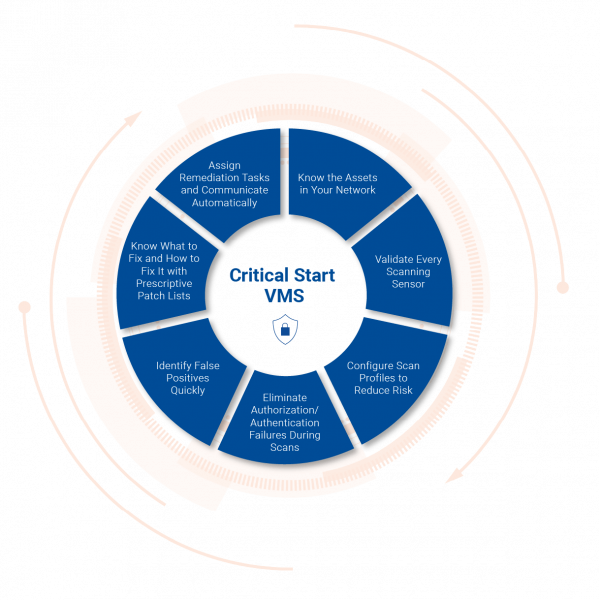
With the Critical Start Vulnerability Management Service, you don’t just find out what assets are vulnerable – you get:

![]()
Reduce your operational workload and improve security outcomes by leveraging the advanced tools, expert capabilities, and human-driven analysis provided by Critical Start VMS.
![]()
Set your schedule for vulnerability scans and deliver results directly to stakeholders through your workflows and ticketing tools.
![]()
Gain immediate access to subject matter experts who manage your vulnerability management program at a fraction of the cost of MSSPs or large, internal teams.
![]()
Support regulatory certification and compliance for PCI-DSS, SOC2, HIPAA, NIST CSF, and more.
![]()
Uncover risks and gain visibility into threats across network environments, end-users, and cloud assets with regular and ad-hoc vulnerability scans and 24x7x365 continuous monitoring.
![]()
Turn threat and vulnerability data into actionable intelligence that helps you eliminate attack vectors and accelerate remediation.
Enhance your security team’s productivity with continuous vulnerability monitoring, scans, fixes, and patch management.
Critical Start’s Vulnerability Management Service is more than just vulnerability scanner licensing, setup, and configuration. You gain continuous operational monitoring, scheduled vulnerability scanning and analysis, break/fix identification and remediation, and a comprehensive list of patches for effective remediation that reduces risk.
Simplify patch recommendations for IT teams and reducing risk through clear communication.
Your Critical Start team relies on best-in-class tools, multi-vector threat intelligence, and deep threat landscape expertise to make sound recommendations on vulnerability management and patch recommendations. Additionally, VMS can tie directly into organizational ticketing systems to automate communications for fast fixes and simplified remediation tracking.
Reduce risk and have the data to demonstrate the full value of your investment.
Once you’re up and running with Critical Start, we’ll ensure your vulnerability scans keep you ahead of threats, and that your dashboards and reports help you clearly measure and articulate your progress. You’ll see tangible risk reduction, with continuous operational monitoring, rich reporting and customizable dashboards, timely alerts to critical vulnerabilities and exploits, and expert analysis that leverages multi-vector intelligence feeds. Then, you can take risk reduction another step further, with peer-benchmarked Quick Start Risk Assessments.
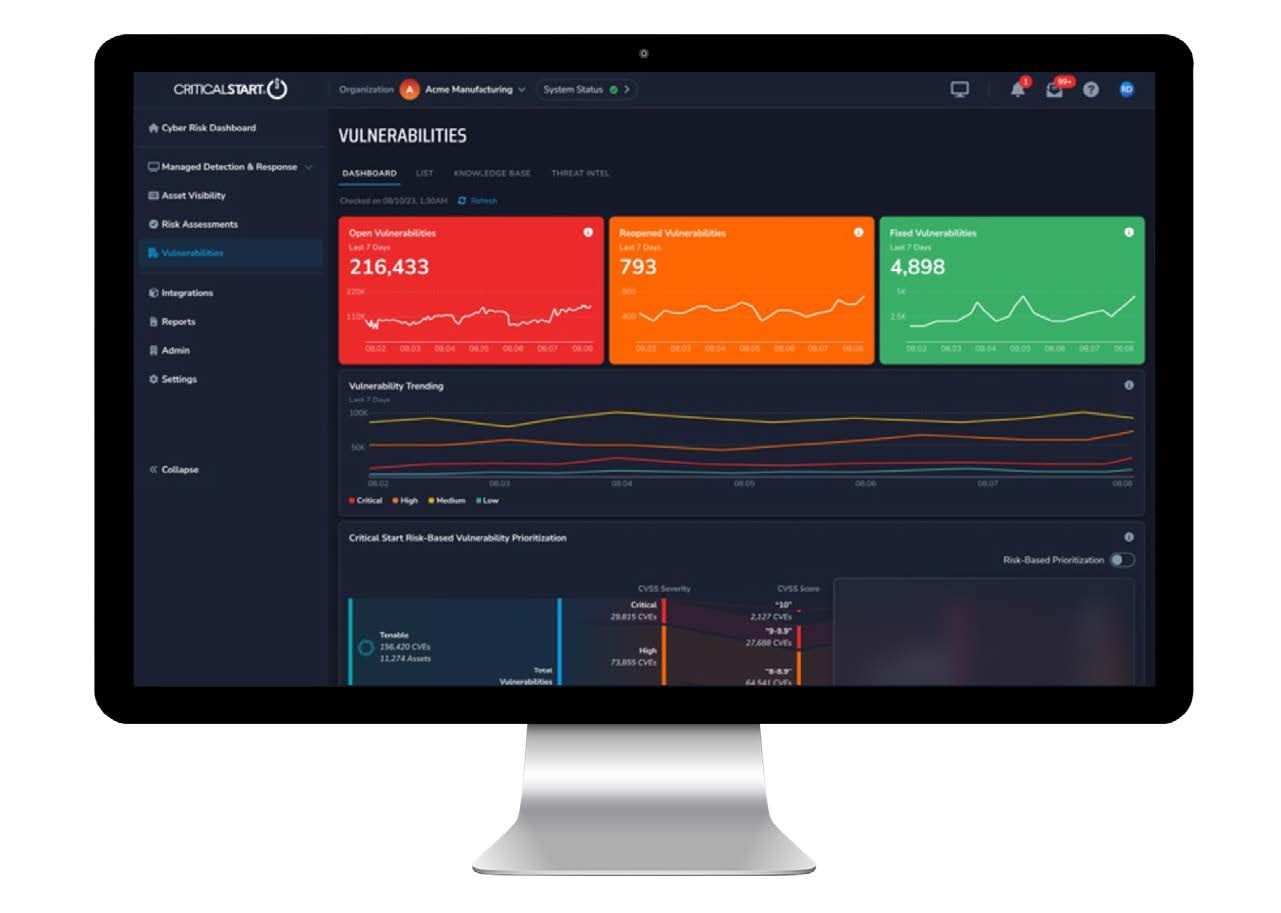
A Vulnerability Management program is only as good as the intelligence behind the analysis. And your response is only as good as the data you get out. Our expert analysts go well beyond CVSS scores to give you comprehensive, contextualized information that keeps the focus on risk reduction. Your analysis is contextualized based on your unique business needs and reviewed by our threat intelligence experts.
Understand your IT landscape through the lens of risk reduction. Your vulnerability assessment shows you:
Gain insight into the threat intelligence behind the vulnerabilities and understand potential vulnerability impact based on:
Quickly visualize not just the vulnerabilities affecting your organization but also the latest threats and major patching guidelines with dashboards for:
Reporting is a cornerstone of vulnerability management communications. Keep your stakeholders informed of your progress and give leadership the data to make informed decisions, with multi-level reporting that includes:
Start with a full asset discovery and assessment:
We’ll help you set up custom scan configurations and ensure full operational readiness:
We’ll conduct regular scans and provide the means for self-scanning:
Understand and articulate exactly how your remediations reduce risk:
Ensure the operational health of your vulnerability scans, catch zero-day vulnerabilities, and thwart active exploits:

Just knowing about and fixing vulnerabilities isn’t enough — you need to be ready to respond in the event of an incident.
As part of your Vulnerability Management Service, we proactively identify incidents and notify you within minutes of detection. You can take advantage of a wide array of additional professional services from our Cyber Incident Response Team, including incident response, threat hunting, forensic investigation, and much more.