CRITICALSTART® Security Services for SIEM:
Uncover hidden threats, maximize total value
If you are struggling to fully leverage your Security Information and Event Management (SIEM) system, you are not alone. In fact, many prospects tell us they feel that their SIEM solution is ineffective in detecting or responding to a security breach.
Organizations are struggling to:
- Manage and optimize their resource-intensive SIEM
- Identify and respond to real threats effectively and reduce alert fatigue
- Demonstrate the full value and ROI of their investment to stakeholders
- Get full visibility into their SIEM’s performance and ensure they’re catching critical security gaps or breaches

Imagine the benefits of seamless operations and stronger risk resilience

Maximize value
Ensure your SIEM is properly optimized, ingesting the right log sources, and delivering measurable security outcomes for maximum ROI.

Enhance security
Map your threat detection content and validate MITRE ATT&CK® Framework coverage for ongoing security relevance. Improve detection, investigation, and response capabilities by leveraging MITRE ATT&CK® Mitigations Recommendations.

Increase efficiency
Offload Tier 1 and Tier 2 SOC support and leverage features like the Unified Timeline and “Who’s on Call?” to streamline workflows and communication, enabling your team to focus on high-priority tasks and strategic initiatives.

Build risk resilience
Reduce the burden on your SOC team with our Trusted Behavior Registry® (TBR®), which filters out known good behaviors to reduce false positives at scale, and our two-person integrity review on every action to be taken.
Critical Start’s Managed SIEM + MDR service goes beyond generic SIEM management and one-size-fits-all MDR to deliver a holistic, adaptive approach to security.
With our Cyber Operations Risk & Response™ (CORR) platform, Cyber Risk Dashboard, SIEM Log Health Monitoring, and MITRE ATT&CK® Mitigations Recommendations, along with our enhanced investigation and communication capabilities, we have what it takes to solve your SIEM challenges, strengthen your overall security posture, and help you effectively reduce risk over time.
We help resolve your challenges
End-to-End Support
- From implementation and optimization to 24x7x365 monitoring, detection, and response, our holistic Managed SIEM + MDR service provides holistic support
- Our expert team leverages deep SIEM knowledge, threat intelligence, and proprietary features like our Trusted Behavior Registry® (TBR®) to maximize your SIEM’s performance and coverage

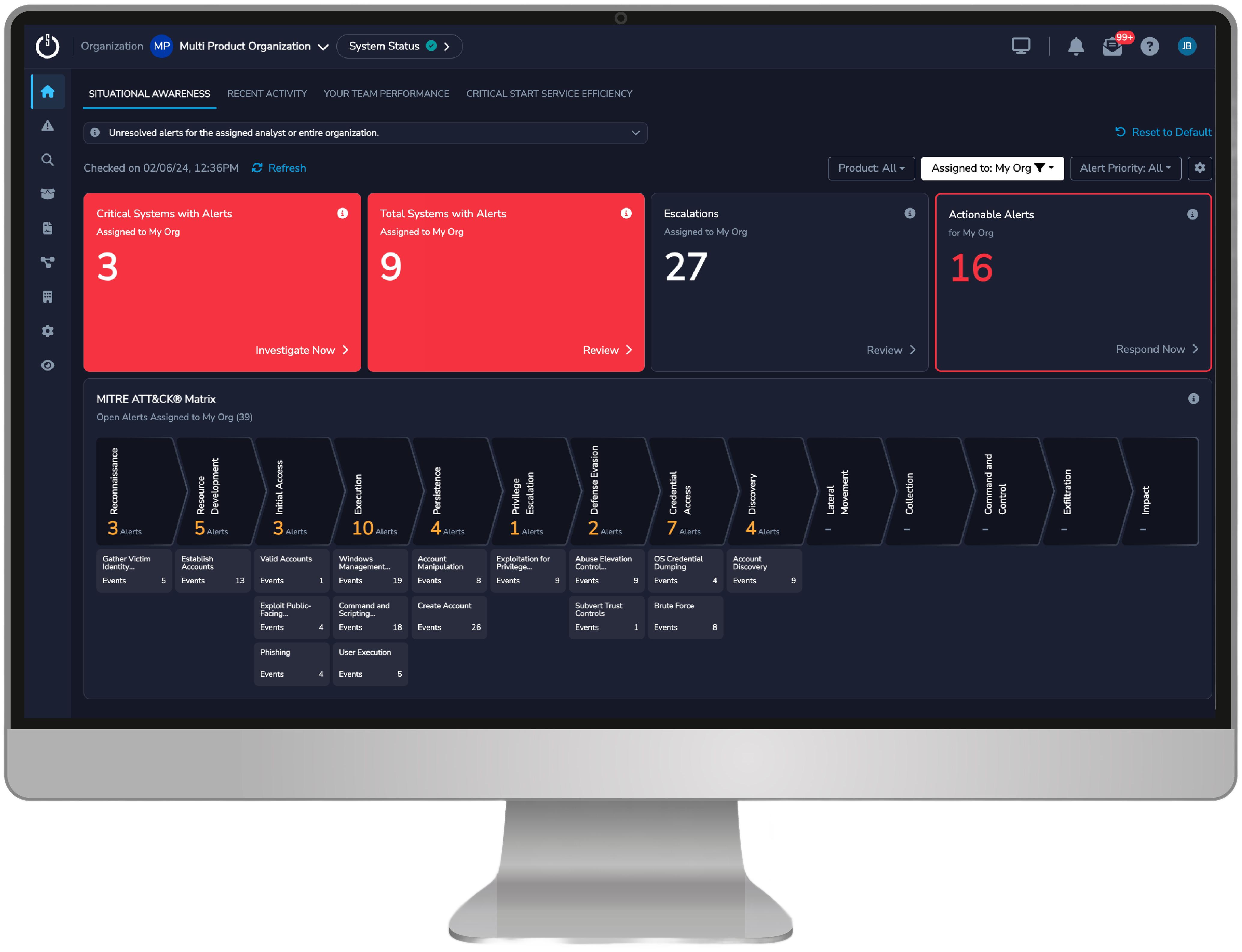
Actionable Risk Reduction
- Included features like SIEM Log Health Monitoring, the Cyber Risk Dashboard, and MITRE ATT&CK® Mitigations Recommendations deliver unmatched visibility and actionable risk reduction insights
- By integrating across your security stack, mapping to the MITRE ATT&CK® Framework, and delivering clear metrics and reporting, we help you close security gaps, reduce risk, and demonstrate measurable improvements to stakeholders
Tailored, Quick, and Reliable Service
- With contractual SLAs of 10-minutes for Critical alerts and 60-minutes or less for Median Time to Resolution (MTTR), our Unified Timeline for streamlined investigations, the “Who’s on Call?” feature for efficient communication, and our MOBILESOC® app for access on the go, we enable rapid response to minimize business disruption
- Our service is tailored to your specific needs and adapts as your environment changes, providing a level of customization and support that other providers can’t match

Want to learn more about…
How we take the stress out of managing your SIEM?
Alleviate the headaches of managing your own SIEM with the back-end services you need to reach the full operating potential of your SIEM investment.
Our comprehensive MDR for SIEM service?
Increase your security posture with simplified breach prevention and Tier 1 and Tier 2 support, allowing your team to focus on the business priorities that matter most.

Is your SIEM security solution no longer enough?
Cyberattacks continue to evolve, and you should expect the same from your MDR provider. Learn the 10 ways an effective MDR provider can help keep your business safe from cyberattacks

Datasheet
MDR for SIEM
Our Managed Detection and Response (MDR) services for SIEM simplify the complexity of Security Information and Event Management (SIEM) tools and help you get the most out of your SIEM investment.

Buyer’s Guide
Buyer’s Guide to Security Services for SIEM
Optimize your SIEM and leverage MDR elevated through proactive security intelligence, flexible deployment options, and human-driven expertise to enhance your organization’s security posture and maximize return on investment.


