- What is Managed Detection and Response (MDR)?
- Key Components of MDR
- Why is Managed Detection and Response Essential?
- What Sets Critical Start Apart
- The Critical Start Difference
- How MDR Compares to Other Security Solutions
- Frequently Asked Questions (FAQ)
- Conclusion: Elevate Your Cybersecurity with Critical Start MDR
Managed Detection Response: The Ultimate Guide for 2024
Cyber threats are becoming increasingly sophisticated. Organizations must adapt their defenses to stay ahead. Managed Detection and Response (MDR) is a key solution to these challenges. Read on to explore what MDR is, its benefits, and why Critical Start’s MDR services stand out among MDR providers.
What is Managed Detection and Response (MDR)?
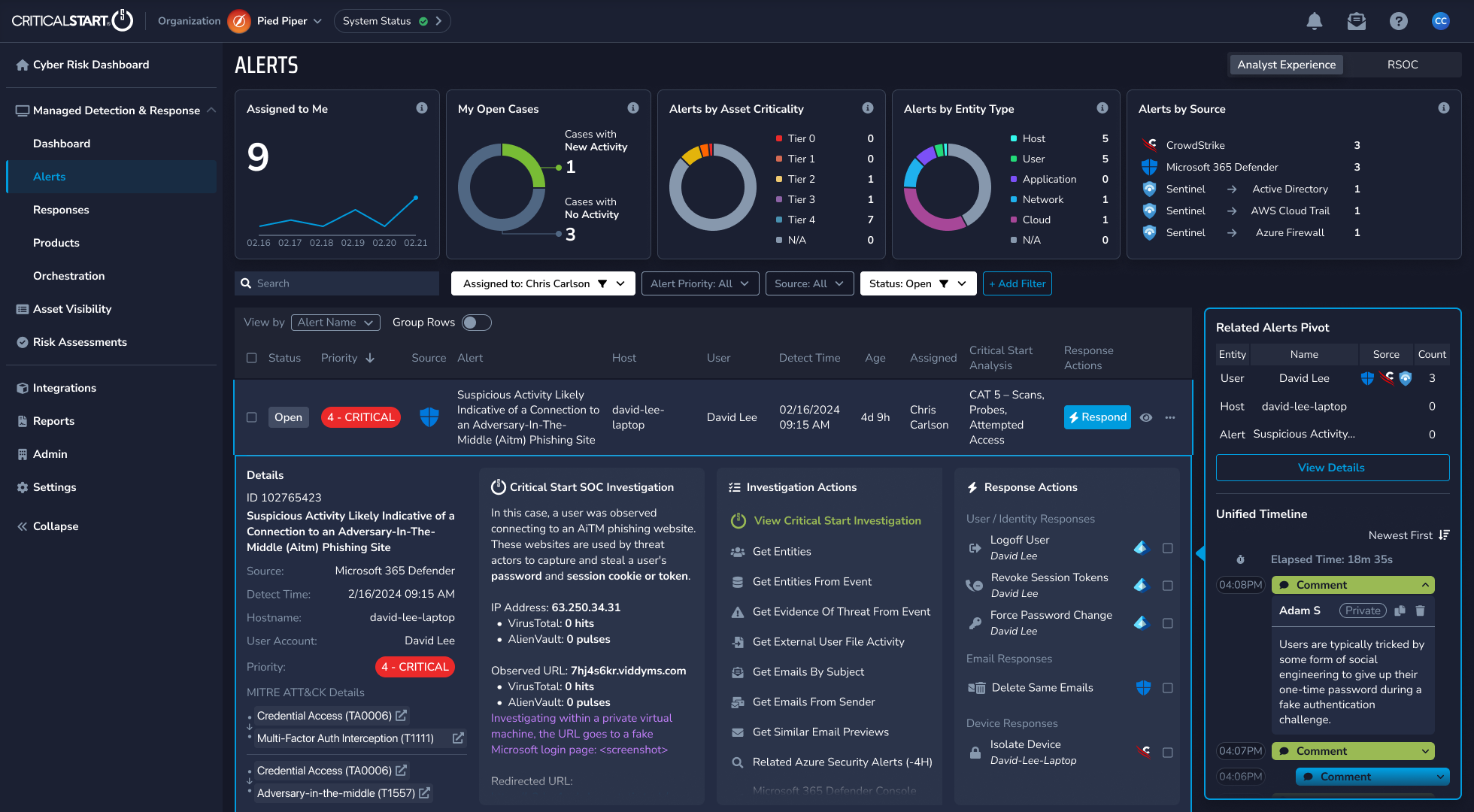
Managed Detection and Response (MDR) is a cybersecurity service. It uses advanced technology and human expertise. It monitors, detects, and responds to cyber threats in real-time. An MDR provider is vital for improving an organization’s threat detection and response. MDR services provide 24/7 threat hunting and incident response. They also provide security operations center (SOC) capabilities to organizations of all sizes.
Key Components of Managed Detection and Response
- Continuous Monitoring: Round-the-clock surveillance of your entire IT infrastructure to identify potential threats.
- Advanced Threat Detection: Leveraging AI and machine learning to uncover sophisticated cyber attacks.
- Proactive Threat Hunting: Humans with security expertise actively searching for hidden threats before they can cause harm.
- Rapid Incident Response: Swift action to contain and neutralize identified threats.
- Comprehensive Threat Intelligence: Gathering and analyzing data to inform and improve security strategies.
Why is Managed Detection and Response Essential?
As cyber threats evolve, traditional security measures are no longer sufficient. MDR addresses gaps by offering:
- Real-time Threat Detection and Response: Immediate action to mitigate risks.
- Access to Expert Security Analysts: Leverage specialized skills without the cost of in-house staffing.
- Proactive Threat Hunting: Humans with security expertise actively searching for hidden threats before they can cause harm.
- Reduced Alert Fatigue: Reduce the burden on IT teams by filtering out false positives.
- Improved Compliance: Meet regulatory requirements through comprehensive monitoring and reporting.
- Cost-Effectiveness: A more affordable alternative to building an in-house SOC, while reducing the risks and costs associated with security incidents.
Critical Start — Industry-Leading MDR Service Provider
Critical Start’s Managed Detection and Response (MDR) is not just another cybersecurity solution; it’s the cornerstone of a comprehensive Managed Cyber Risk Reduction (MCRR) strategy designed to deliver unparalleled risk mitigation and operational efficiency to mitigate business disruption. This strategy combines proactive security measures with comprehensive risk management, utilizing our Cyber Operations Risk & Response™ (CORR) platform.
What Sets Critical Start Apart
We integrate industry-leading cybersecurity tools, and proactive cybersecurity threat intelligence into the Critical Start SOC to provide comprehensive asset inventories, EDR/SIEM coverage gap analysis, asset criticality ratings, MITRE ATT&CK® Mitigations, and vulnerability management. This integrated approach ensures that we address threats proactively and manage vulnerabilities effectively, thereby minimizing business disruption and maximizing operational efficiency.
Unlike conventional security solutions that only detect and respond to threats, Critical Start’s MDR integrates proactive security measures with comprehensive risk management capabilities. This holistic approach ensures:
- Security Operations Signal Assurance: EDR gap and log source monitoring guarantee that your Security Operations Center (SOC) receives all necessary threat signals, leaving no blind spots in your defense.
- Asset Visibility: Determine and maintain an accurate and persistent asset inventory of critical assets across your organization. Categorize risk impact based on business function, we help you prioritize security efforts where they matter most.
- Human-Driven Investigation and True Response Mitigations: Our experts provide true response mitigations backed by contractual SLAs, ensuring swift and accurate threat resolution.
- Flexible Deployment Models: Supporting all IT and OT threat types and log sources, our solutions are adaptable to your unique operational environment.
- Maximizing Efficiency and Minimizing Disruption: Critical Start’s MDR service is designed to minimize business disruption and maximize operational efficiency. Our human-driven approach, combined with advanced technology, ensures that every threat is addressed promptly and effectively by security experts. This integration of proactive measures with responsive action allows your organization to stay ahead of the curve, reducing the risk of breaches and enhancing overall security posture.
The Critical Start Difference — Not All MDR Providers are Created Equally
Industry Recognition
-
- A major player in the IDC MarketScape: Worldwide Emerging Managed Detection and Response (MDR) Services 2024 Vendor Assessment.
- Acknowledged in the 2024 Gartner® Market Guide for Managed Detection and Response Services.
Specialized Services
-
- MDR for OT: Tailored protection for operational technology (OT) environments.
- Managed XDR: Threat-centric visibility without the need for a SIEM.
- Incident Response: Rapid action to minimize the impact of breaches.
MOBILESOC®: MDR on the Go
Our unique MOBILESOC® app allows you to:
-
- Receive real-time alerts.
- Communicate directly with our SOC analysts.
- Act now to contain threats from your mobile device. This will reduce the risk of them spreading through the system.
How MDR Compares to Other Security Solutions
MDRs vs. MSSPs (Managed Security Service Providers)
MSSPs focus on monitoring and alerting. Managed Detection and Response goes further. It hunts for threats and responds to incidents with fixes advanced analytics and security tech.
MDR vs. EDR (Endpoint Detection and Response)
EDR focuses only on endpoints. MDR covers your entire network and IT infrastructure, including your cloud computing environments.
Implementing MDR in Your Organization
-
- Assessment: We begin with a thorough evaluation of your current security posture. Security teams are vital. They manage and respond to alerts. They must ensure the implementation meets the organization’s needs.
- Integration: We seamlessly integrate our MDR services with your existing security tools.
- Onboarding: Our experts provide training and support to ensure a smooth transition.
- Continuous Improvement: We regularly optimize our MDR services to counter new threats.
Key Benefits of Critical Start MDR
-
- Security Operations Signal Assurance: It comes from the asset visibility module (asset inventory & criticality ratings), endpoint coverage gaps, and log source monitoring.
- Flexible Deployment: The most flexible options that support all IT and OT threat types and log sources.
- Proactive Risk Reduction: Identify and address threat exposures before they become active threats.
- Enhanced SOC Productivity: Offload Tier 1 and Tier 2 SOC support, enabling your security team to focus on strategic initiatives.
Frequently Asked Questions (FAQ)
What is the difference between MDR and MSSP?
MDR provides proactive threat hunting, extended detection, and incident response. MSSPs typically focus on monitoring and alerting, without active threat response.
How does MDR enhance my existing security tools?
MDR integrates with your tools. It adds threat intelligence, expert behavioral analysis, and fast response.
What industries benefit most from MDR services?
MDR solutions and services help many industries, including finance, healthcare, and manufacturing. They are vital for any sector facing advanced threats
Can MDR help with regulatory compliance?
Yes, MDR services can help. They provide monitoring, log management, reporting, and threat response. These are aligned with industry standards.
Conclusion: Elevate Your Cybersecurity with Critical Start MDR
In a time of evolving cyber threats, Critical Start’s Managed Detection and Response services provide the protection your organization needs. They are proactive and comprehensive. We use threat research. We combine cutting-edge technology with human expertise. This gives us unmatched threat detection and response capabilities.
Our approach stops threats from slipping through the cracks. It reduces breach risks and business disruptions. With Critical Start MDR, internal security teams get:
-
- Comprehensive and proactive threat management with complete signal coverage.
- Effective real-time investigation and response to emerging threats unique to your organization.
- Enhanced risk reduction that improves SOC productivity.
Don’t just react to cyber threats – stay ahead of them with Critical Start Managed Detection and Response. Contact our experts today to get the MDR service you need to enhance your security operations and reduce risk.
