Achieve the full operating potential of your Singularity Core, Control, or Complete investments
The combination of SentinelOne Singularity with Critical Start Managed Detection and Response (MDR) services goes far beyond just monitoring alerts. It increases the visibility across hybrid device types and operating systems to stop the most advanced attacks, reduces risk exposure, eliminates alert fatigue, and optimizes the efficiency of security operations centers (SOC).
Key Benefits

A simplified view of everything
Consolidated and improved visibility of your environment all in a single interface.

Reduce the noise
Get fewer false positives over time which dramatically reduces alert fatigue and analyst burnout.

Improve your security posture
Our Cyber Research Unit (CRU) helps you stay ahead of the latest threats by building, enriching and adding threat intelligence to your security tools.

Increase your SOC’s efficiency and productivity
We do all the heavy lifting for you, so you don’t have to.
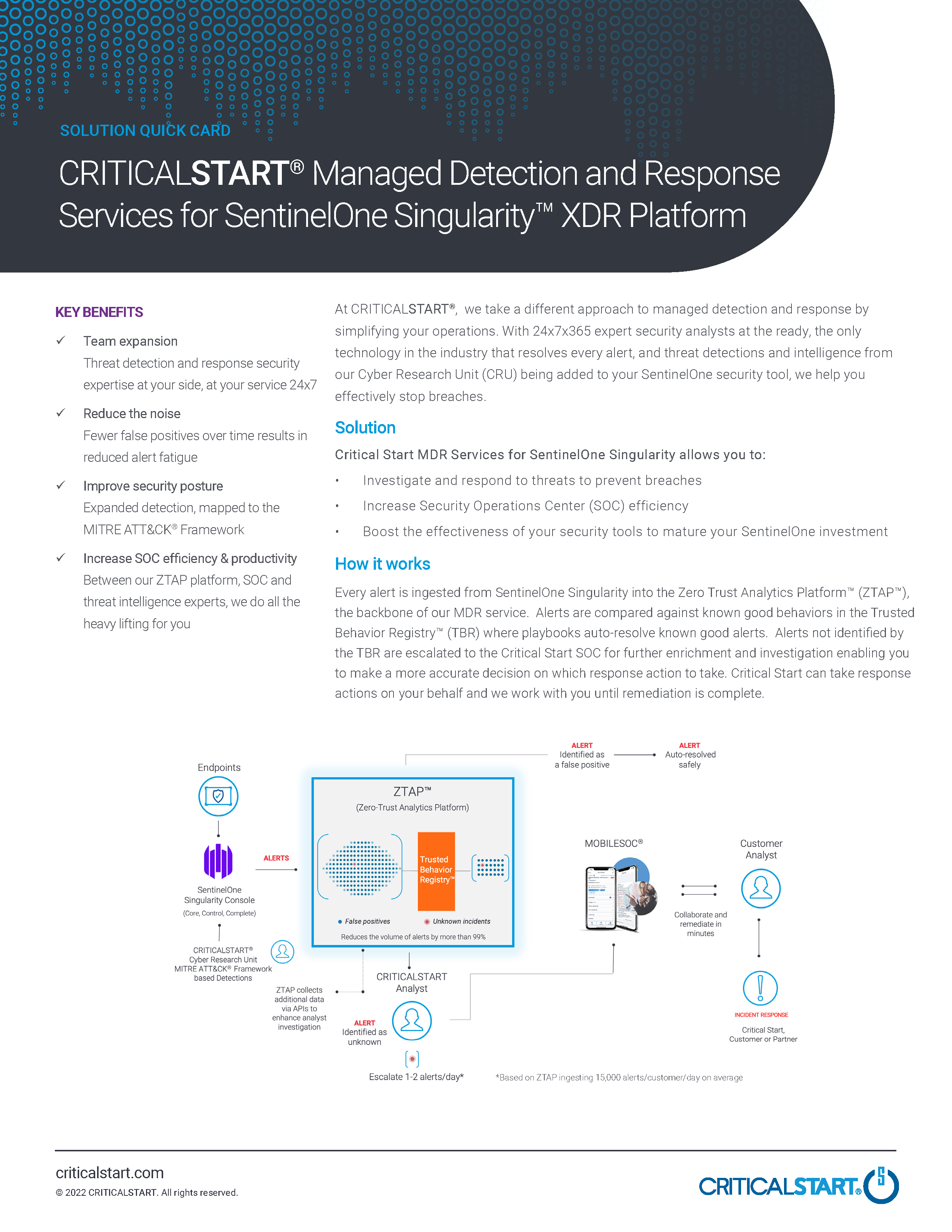
How Our MDR Service for SentinelOne Singularity Works
Critical Start MDR adapts to your environment to deliver the full power of SentinelOne Singularity Core, Control, and Complete.
Our bi-directional integration ingests every endpoint alert from SentinelOne Singularity into our Cyber Operations Risk and Response™ platform, where they’re compared against known good behaviors in the Trusted Behavior Registry® (TBR) and playbooks auto-resolve known good alerts at scale. Alerts not matching the TBR are escalated to our Risk and Security Operations Center (RSOC) analysts for further enrichment and investigation. Best of all, we can take response actions on your behalf, and we will work with you until remediation is complete.
Hear from Our Customers

Justin Hadley
The managed detection and response service has significantly increased our analysts’ efficiency to the point that they can focus on other areas of the business.
Sr Manager, Security Engineering, Alkami
How We Work with You
We’re with you every step of the way – from onboarding through maturity.

Onboard quickly:
We will get you up and running as fast as possible: 4-6 weeks on average with total time to first value of approximately 5-10 business days.
Personalize based in your unique requirements:
We continue to add value to your implementation by tailoring our MDR services to your unique needs through playbooks and procedures adapted to your environment to reduce false positives.


Investigate and resolve alerts:
Once you’re up and running, our platform and our security analysts will monitor your environment 24x7x365 for potential threats. You can expect to see an approximate reduction in false positives of 90% on the first day of production monitoring.
Mature your SentinelOne investment:
We want to help you get the most out of your SentinelOne Singularity tools so we’re with you every step of the way. Your Customer Success Manager will check in with you regularly to make sure we’re meeting your expectations and our MDR services are helping you achieve your security goals.

Why Critical Start MDR?
Resolve, not suppress
We resolve every alert and only forward those that truly warrant additional investigation by your security team.
- Resolve more than 99% of alerts
- Escalate less than 0.01% of alerts
Ready to respond 24/7/365
Our security analysts help you contain and extinguish threats as quickly as possible to stop them from spreading. They:
- Operate as an extension of your security team
- Triage and investigate alerts that are not auto-resolved by our platform and the TBR
- Use your tools and our platform to respond to alerts on your behalf — depending on mutually agreed-upon rules of engagement
- Function as an open book with 100% transparency and visibility into every action taken
Experts in threat detection
The Threat Detection Engineering (TDE) team develops and enriches new detections and IOCs. They also map detection to the industry-leading MITRE ATT&CK® Framework, ensuring you are protected against the latest attacker Techniques, Tactics, and Procedures (TTPs).
Fast resolution with MOBILESOC®
MobileSOC puts the power of our platform in your hands, giving you the ability to triage, escalate, and isolate attacks in-the-moment from your iOS or Android phone, regardless of your location or time of day.
quick card
MDR Services for SentinelOne Singularity
Using the power of SentinelOne, Critical Start enables customers to centralize, ingest, and correlate 100% of their logs to ensure their environment is secure. Critical Start’s MDR utilizes a Trusted Behavior Registry to investigate every alert generated. Customers see every action our security analysts take since our platform provides 100% transparency across the entire process.
¹ SentinelOne STARPro add-on required for custom IOCs
MDR for multiple EDR, SIEM, and XDR tools
We offer MDR services for multiple tools, all supported by a single platform and accessible on the go through our MobileSOC app, making these easy for our customers that work with multiple security tool vendors.