Detect and Disrupt Attacks Beyond the Endpoint
Critical Start Managed Detection and Response (MDR) extends your security defenses across your Microsoft SIEM and XDR solutions. From endpoint to email, from user credentials to cloud apps and more, we go beyond response recommendations and can act on your behalf.
Respond to every alert regardless of criticality
If you want us to recommend response actions, we can do that. But when minutes count, our Microsoft security experts can actually become an extension of your team and provide remediation and response actions to the threat as soon as it’s detected.
Our team of Microsoft security experts leverages our integration with Microsoft Sentinel and Defender XDR to detect, investigate, and respond with the right actions before threats can disrupt your business.
Here’s a quick view of what you get:
Key Benefits:
Full optimization of Microsoft Defender XDR
Our Microsoft experts configure Microsoft Defender XDR (formerly Microsoft 365 Defender) to your environment, help to define detection and prevention policies, and continuously work with you to fine-tune your deployment as new risks are identified.
24x7x365 increased response coverage
Analysts in our Security Operations Centers (SOCs) detect, investigate, and respond to threats with the right actions so your team can focus on what matters.
Expanded situational awareness
Consolidate and improve visibility of your environment all in one portal delivers actionable views of attacks in progress with clear, step-by-step response guidance for situational awareness your security teams can use.
Threat awareness for risk-based decision-making
Critical Start MDR maps detection content to the MITRE ATT&CK® Framework for detailed insights into specific threat tactics and techniques, enabling risk-based decision-making and improved attack coverage effectiveness.
Increased team efficiency
Contractual Service Level Agreements (SLAs) for analysts and teams drive continuous improvement, productivity, and team efficiency.
Every alert resolved
We stop attacks before they can disrupt your business with 60-minute or less Time to Detection (TTD) and Median Time to Resolution (MTTR) SLAs on every alert.
Microsoft Security Expertise
Certified Microsoft expertise
Our security experts are Microsoft Certified Security Operations Analyst Associates
And we use Microsoft Security Best Practices
IOC management on us
Microsoft is the fastest-moving security company today. IOCs are published and updated hourly across different locations. Leveraging the Critical Start Threat Navigator, we manage and maintain out-of-box detections and IOCs. Detection content is also mapped to the industry-leading MITRE ATT&CK® Framework.
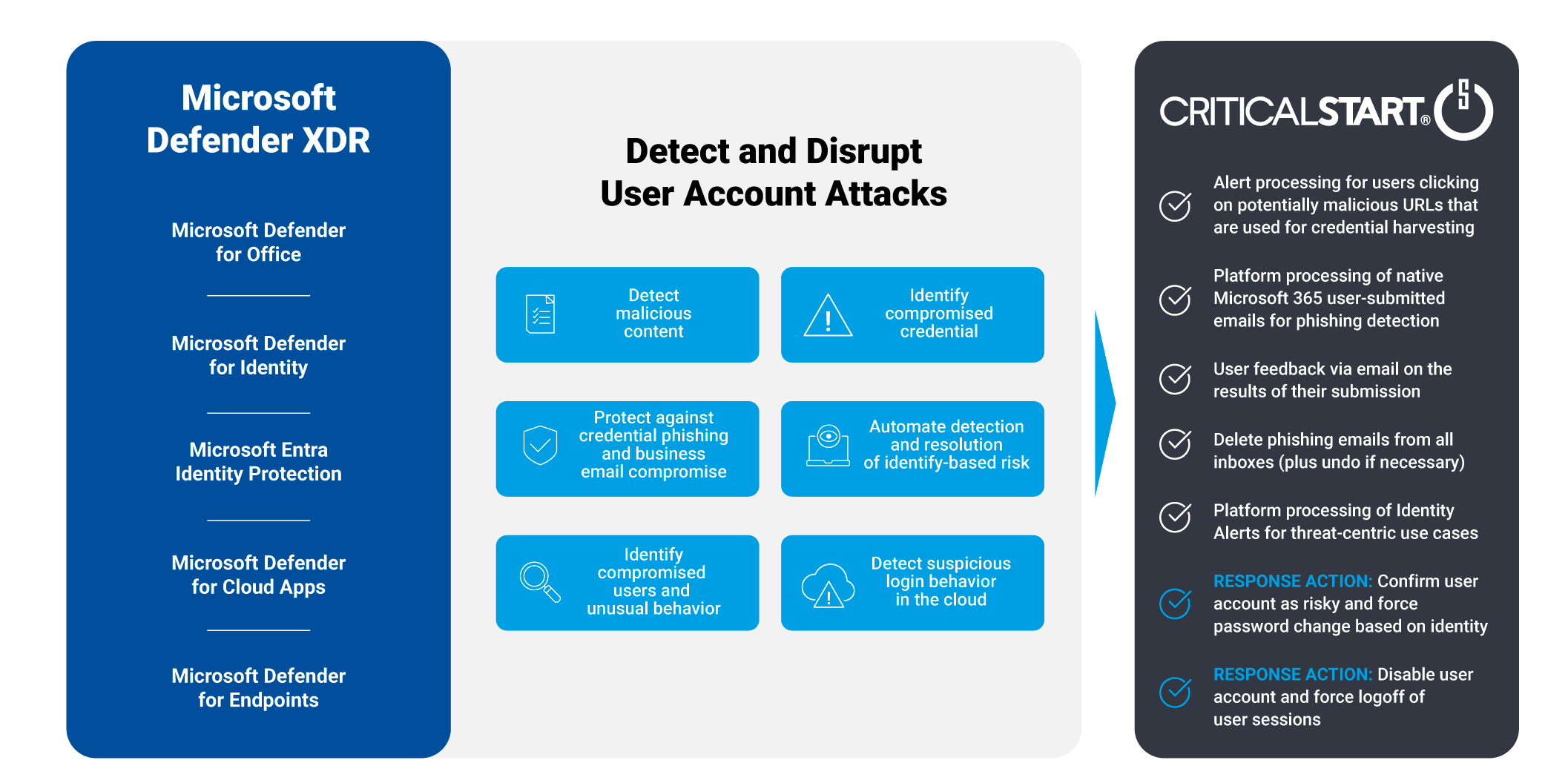
Protection against user account attacks
Our MDR services not only detect but can also take response actions for you to disrupt user account attacks. And an integration with Microsoft Outlook “Report Message” allows us to further support you with investigation and response actions for your employee submitted emails that are suspected phishing attacks.



USE CASE
Stopping credential email phishing attacks
Successful attacks expose your organization to data breaches through standard user account access methods. Our MDR services will detect and disrupt suspicious email threats 24x7x365 through detection, investigation, and remediation of platform and user-reported phishing attacks.

USE CASE
Disrupting brute force and stolen credential attacks
Preying on weak user passwords is still a highly effective way to gain access to your organization. Protect the identities of your users, prevent takeovers of their credentials, and stop brute force attacks with MDR services for Microsoft 365 Defender.

USE CASE
Stopping attacks on data in cloud apps
Adversaries know that by using legitimate credentials, they have insider access to your organization and that makes it harder for you to detect them. Prevent takeovers of user credentials, obstruct lateral movement to other apps, and disrupt attacks against Cloud apps.