Offload Security Workloads
Learn the best practices for integrating your SOC team with MDR services
Learn the best practices for integrating your SOC team with MDR services
Augment and modernize your team’s capabilities with detection and response services that adapt with your organization.
Eliminate burnout and employee churn by partnering with our Risk & Security Operations Center (RSOC) to defend against cyber threats more effectively.
51% of cybersecurity professionals experience stress or burnout.1 Frustration with security tools and data, such as high alert volumes and false positives and the lack of correlation across multiple tools, is the second most influential factor in causing employee churn (77%). The top factor influencing security teams’ resignation rates is burnout.2
Given the shortage of cybersecurity professionals, you can’t afford to lose skilled employees.
Lack of visibility into your security team makes it difficult to identify where resources and training are most needed. Inadequate staffing may also widen an organization’s exposure to threats.
Our RSOC experts work around the clock to deliver unmatched scalability that effectively defends your operations against cyber threats. As a result, tedious tasks, such as Tier 1 and Tier 2 support, are offloaded so your team can focus on more strategic responsibilities, boosting retention rates and streamlining your security operations.
72% of security leaders say employee churn is heavily influenced by the amount of time their team spends on low-value administrative and manual tasks.3
Our RSOC augments your team by providing Tier 1 and Tier 2 support so your employees can focus on higher priority, more appealing responsibilities such as addressing real and emerging threats – not false positives. This minimizes burnout and reduces employee turnover.
Between our MDR platform and specialized security experts, we bring you innovation and enhanced coverage, visibility and insights to help your security operations evolve and combat threats.
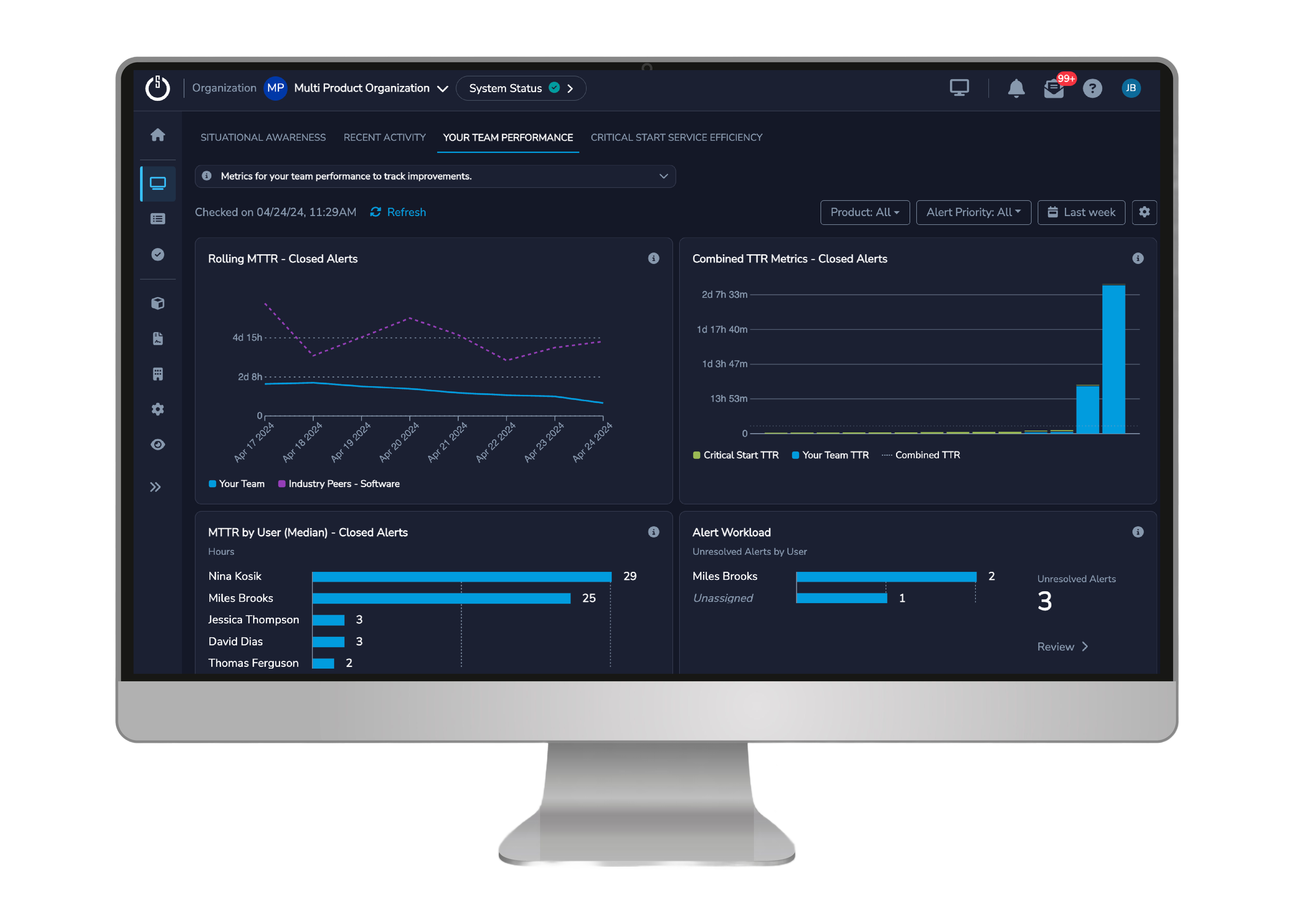
You’ll always have 100% visibility in our RSOC’s performance via dashboards that highlight important metrics such as their progress in detecting and investigating alerts.
Make well-informed, risk-based decisions tied to trends in threat activity and your team’s performance. With our dashboards, you can answer questions such as do you need to hire additional resources or do workloads need to be spread between more people?
This information helps you improve security analysts’ productivity and focuses their time on high priority activities.


This white paper explores how organizations that have decided to enlist the help of a third party to support their security professionals, future proof their cybersecurity infrastructure and increase the overall security posture of their company can most effectively integrate their SOC team with their chosen MDR service provider.

Our RSOC is ready to extend the detection and response capabilities of your ccriticalstart.com/socybersecurity operations 24x7x365.

SOC Senior Analyst Davis Kouk explains how Critical Start’s SOC delivers managed detection and response services 24x7x365 for EDR, SIEM & XDR tools.

Read how a manufacturer unified their security posture and dramatically increased alert visibility through Critical Start MDR and Palo Alto Cortex XDR.

Managed Detection and Response is reinventing information security. In this paper, you will learn how it provides far better visibility into threats and enables an active, real-time response to mitigate any impact. We’ll discuss what to look for in an MDR provider and—most importantly—why every alert matters.