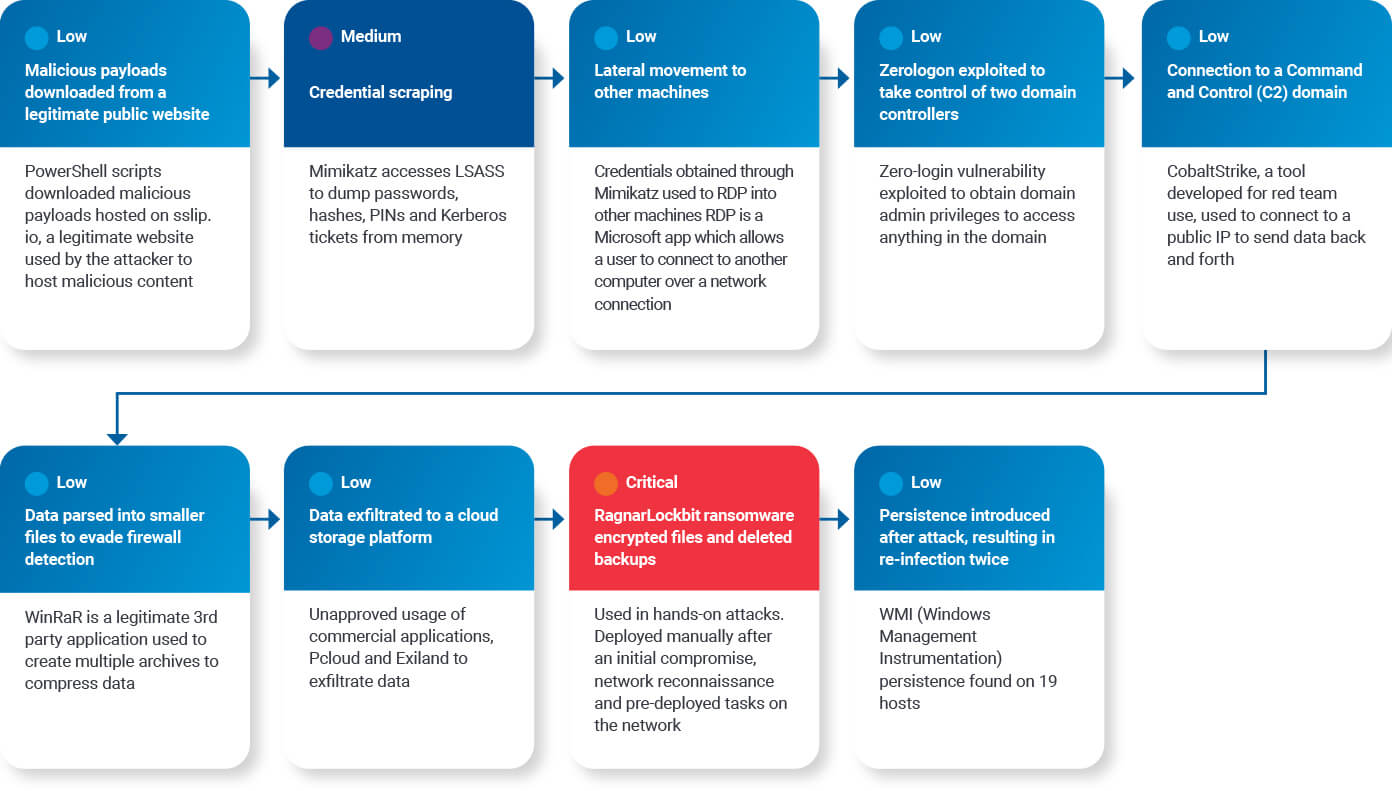
CRITICALSTART’s Incident Response (IR) team was recently engaged by a mid-size bank that was victimized by the RagnarLockbit ransomware. The client paid the ransom, only to be re-infected twice and making a second payment. That’s when CRITICALSTART came in.
The first evidence we observed was the use of PowerShell scripts to download malicious code from a legitimate content hosting website that was not blacklisted at the time. Threat actors take advantage of PowerShell’s unlimited access to Windows resources including Windows APIs, full access to Window Management Instrumentation (WMI), and the .NET framework.
The EDR solution reported this activity with a Low priority alert.
Many traditional MDRs claim they resolve all alerts. But what does that mean?
For CRITICALSTART, it begins with configuring security tools to collect all possible alerts, across all priorities – Critical, High, Medium, and Low. This will generate a tremendous volume of alerts.
Assuming an average of ten minutes to investigate and resolve each of these alerts, you are looking at over 2,400 hours.

This presents some questions:
What happens when another client suffers through an alert storm?
How will this impact risk exposure to your organization?
And how does an MDR provider support this alert volume across all their clients?
The answer is they don’t. Traditional MDRs control alert volumes through alert suppression.
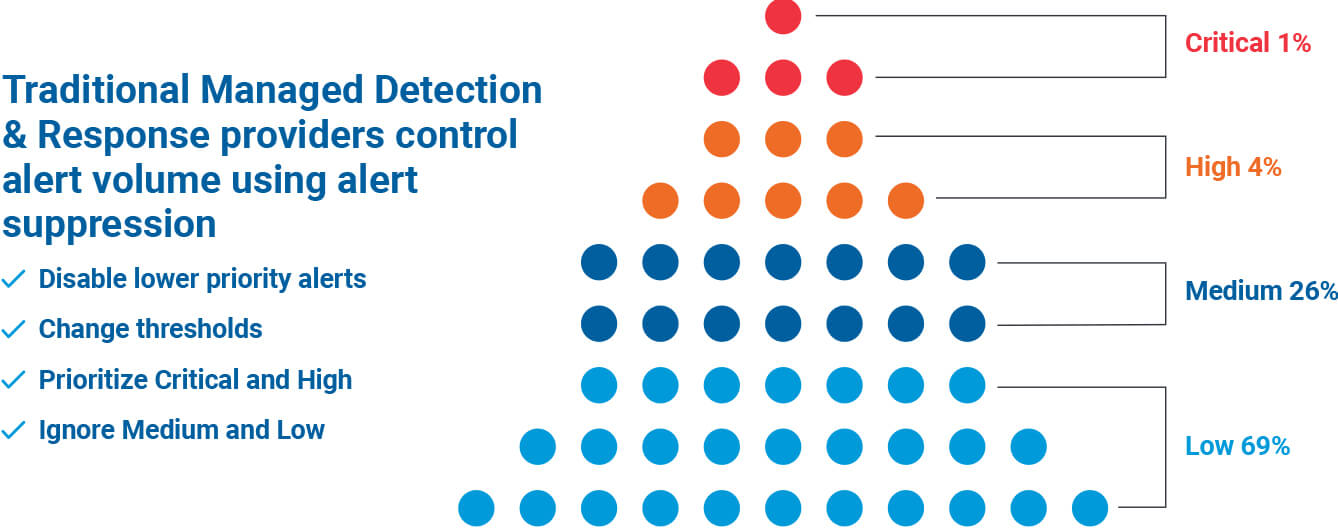
Practicing alert suppression comes at a price – Risk Acceptance. The cost of a ransomware attack comes from business disruption which leads to lost revenues, lost productivity and potential SLA fines from partners and customers.
Is it possible to resolve all alerts?
Yes. CRITICALSTART’s MDR service is based on this. We combine the industries most advanced analytics and automation platform with elite security expertise to resolve every alert, stop breaches and reduce risk acceptance. This reduced the alerts requiring CRITICALSTART SOC investigation from 14,400 alerts per client per day down to 9 alerts per client per day. This provides the means for CRITICALSTART to resolve all alerts at scale.

Download the full whitepaper to learn more about the specifics of the attack and the importance of resolving every alert.

Resolving all alerts starts off with configuring security tools to collect all alerts. This creates an alert volume that overwhelms the capacity of most MDRs.
Traditional MDRs solve their scalability problem by suppressing alerts, requiring their clients to accept risk, often without their knowledge.
[gravityform id=”24″ title=”false” description=”false” ajax=”true” tabindex=”49″ field_values=”check=First Choice,Second Choice”]