Simplify breach prevention
and keep your business thriving.
Say goodbye to complex managed detection and response and hello to simplicity.
Say goodbye to complex managed detection and response and hello to simplicity.


WHAT WE DO
We dive in deep to understand your security operations and requirements.

We’re with you every step of the way to improve your security posture—even as your environment changes.

With our seasoned security analysts and one-of-kind technology at your side, we’ll help you make accurate decisions on the right response to protect your security operations.


OUR SERVICES ARE DIFFERENT
Our Trusted Behavior Registry resolves all alerts. If a known false positive surfaces, we’ll resolve it rather than forwarding it on to your team.
You’ll get full details on every alert, investigation and response action we take. We don’t hide anything.
We give you our word to satisfy service level agreements for Time to Detection (TTD) and Median Time to Resolution (MTTR) for every single alert.
With MOBILESOC®, a mobile app that gives you full access to alerts, tickets, reports and investigation details.



Our Zero Trust Analytics Platform™ (ZTAP™) is the backbone of our managed detection and response solutions. With the industry’s only Trusted Behavior Registry™ (TBR), ZTAP is purpose-built to resolve all alerts.
Drive down attacker dwell time with Critical Start MobileSOC. Through this iOS and Android app, we go beyond ticketing and instant notifications, giving you the ability to action incidents immediately with information gathered in our platform.
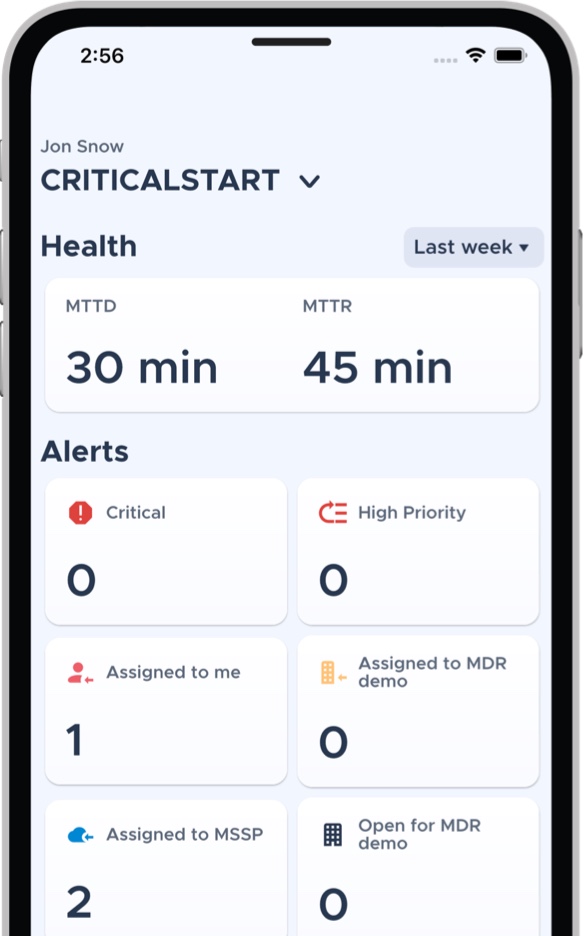
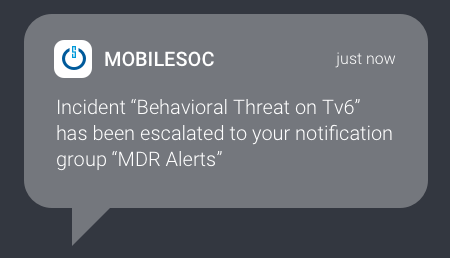

Communicate directly from anywhere with CRITICALSTART SOC analysts for remote collaboration, workflow and response.

The value of this far outweighs any cost. And you really can’t put a price on the peace of mind you get from knowing you can rely on this level of expertise.
Having a team that considers the potential threat of a low-priority alert in the same way they treat a critical- or high- alert is a big deal.
If something is wrong in my environment, I need to know, and these guys are exactly what I need to ensure I have that visibility.

We have now been able to identify the risk and address it through a workforce that alleviates the burden from my team. I have peace of mind knowing that these alerts are examined and escalated as needed, and that visibility is something I can take back to management as we determine how to allocate our resources in the future.




