Become a breach-stopping machine.
Resolving alerts is good. Resolving all alerts is better.
Resolving alerts is good. Resolving all alerts is better.
Every alert is important because every alert tells a story. And that story can stop a threat. So, stop settling for so-called good security that just prioritizes alerts and allows real intruders to fall through the cracks.
Detect every threat. Resolve every alert. Stop breaches.
The only way to detect every threat is to resolve every alert. We’ve built a registry of all trusted behaviors so our clients can benefit from the experiences of everyone in the community.
When good enough isn’t good enough, work with a team of elite cybersecurity professionals who have the expertise in technology, adversarial engagements, risk and compliance, privacy, and more.
TEAMARES can evaluate your security posture including vulnerability management, adversarial simulation penetration testing and onsite training.
Drive down attacker dwell time with CRITICALSTART MOBILESOC™. Through this iOS and Android app, we go beyond ticketing and instant notifications, giving you the ability to action incidents immediately with information gathered in our platform.
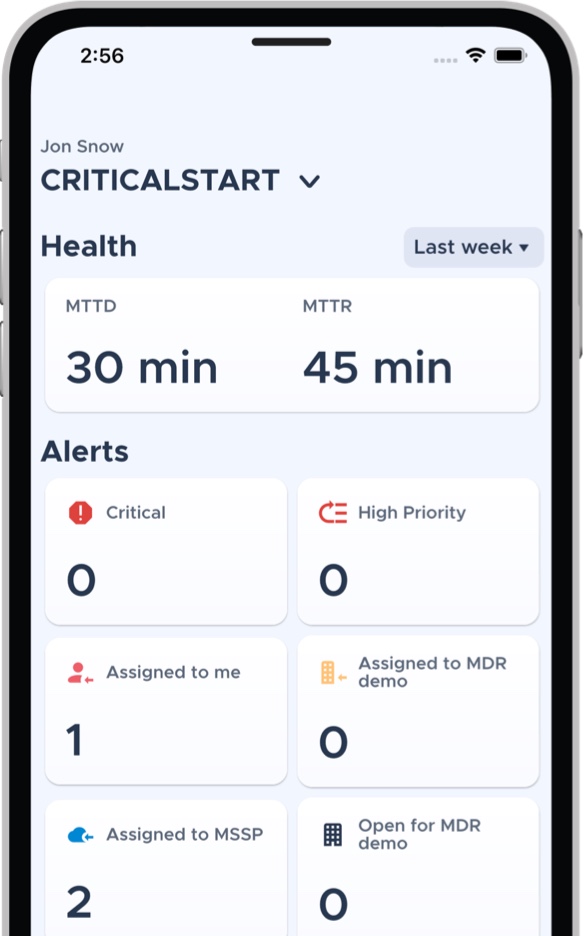
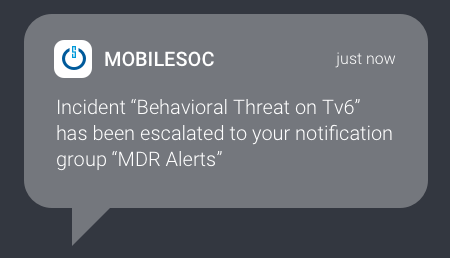


Let us show you how our MDR service resolves every alert so we can accept the risk you shouldn’t.
[gravityform id=”7″ title=”false” description=”false” ajax=”true” tabindex=”49″ field_values=”check=First Choice,Second Choice”]

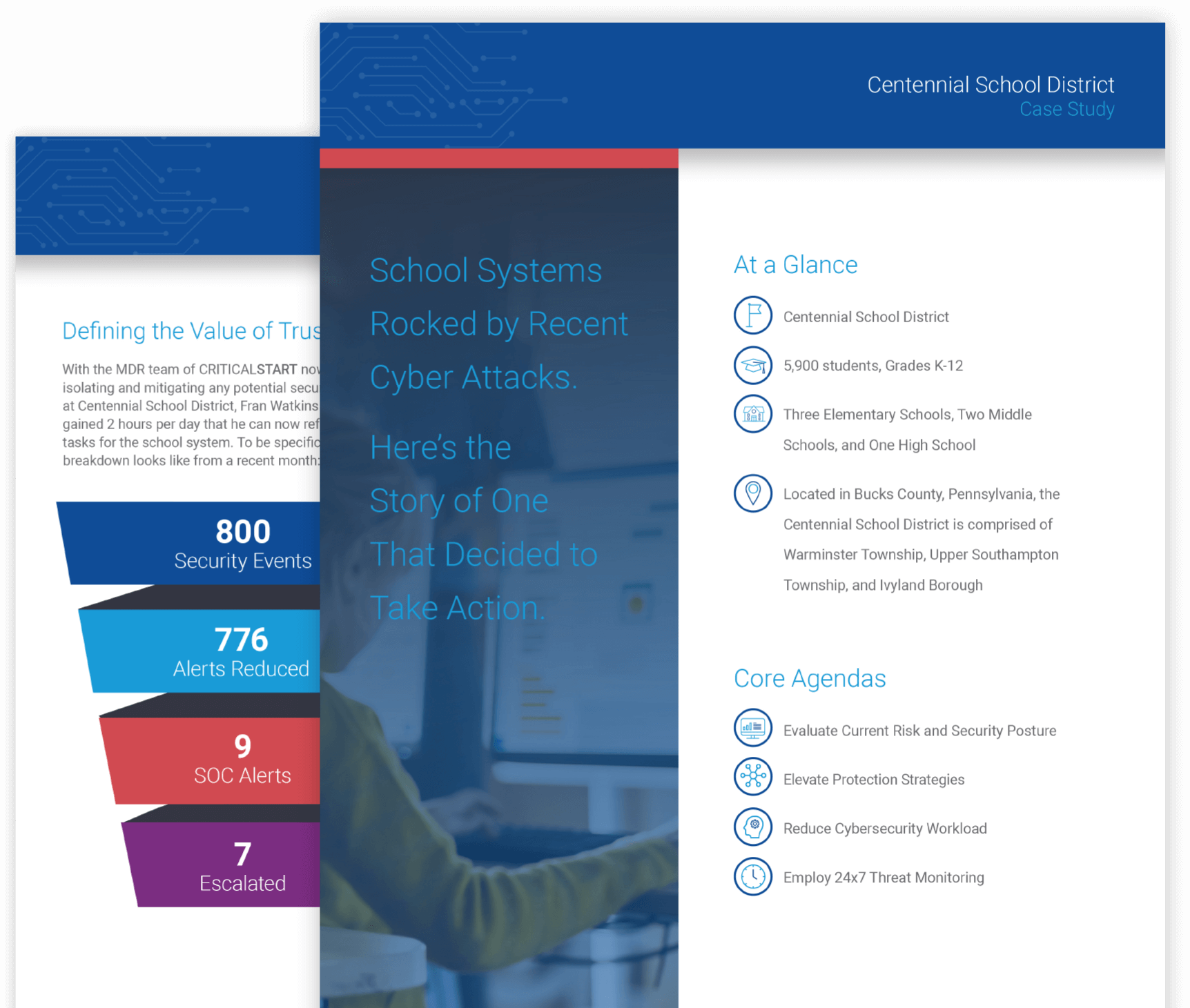
Learn how Centennial Schools System took action to prevent breaches by recognizing the critical importance of resolving every alert and working with an MDR vendor that provided trusted expertise through a technology-agnostic approach.

I would say that prior to the relationship with CRITICALSTART, my SOC analysts were experiencing what we all call alert fatigue. CRITICALSTART has really been able to reduce those alerts… I’ve been able to take our level three and four analysts and put them back to work at what they were hired to do.

Reactive emergency response and proactive incident readiness services to help you prepare, respond and remediate.

We’ll analyze your security challenges and present a plan on how you can leverage our services and those of our product partners. Our recommendations include only best-in-class solutions.


