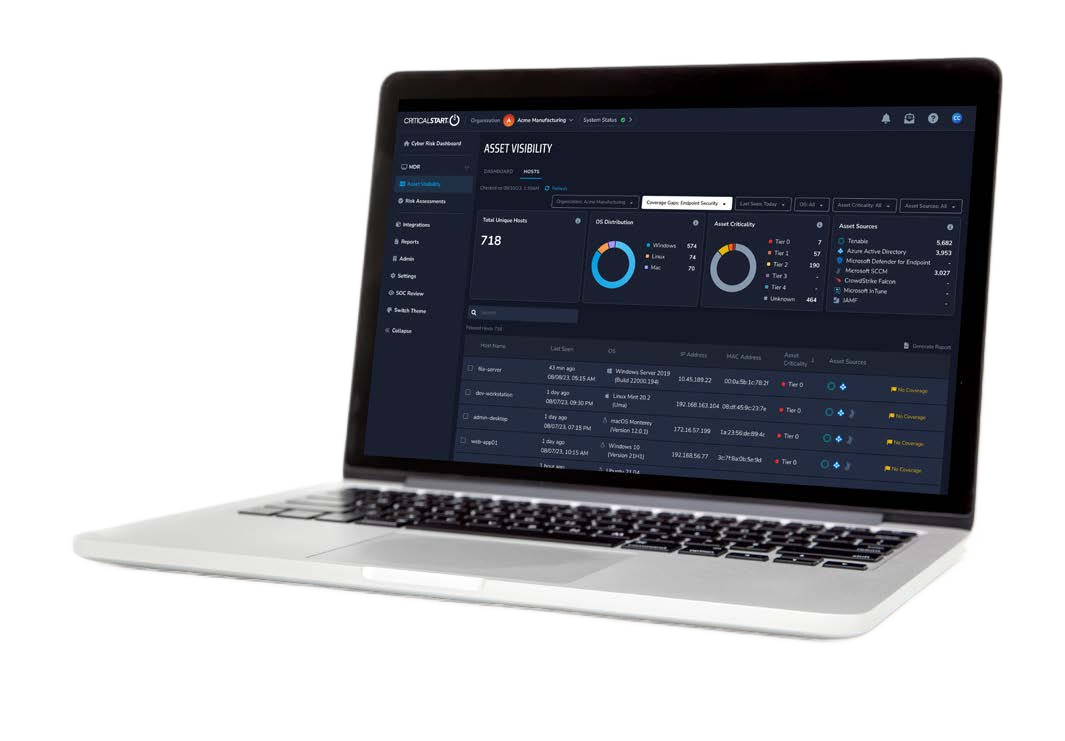
CRITICALSTART® Asset Visibility
Improve security posture and reduce risk by proactively identifying security coverage gaps and ensuring the right controls are in place.
Improve security posture and reduce risk by proactively identifying security coverage gaps and ensuring the right controls are in place.
Asset visibility is a critical component of risk reduction. CISOs and SecOps leaders must ensure they are effectively measuring their true level of risk exposure and fixing security gaps before they become entry points for adversaries.

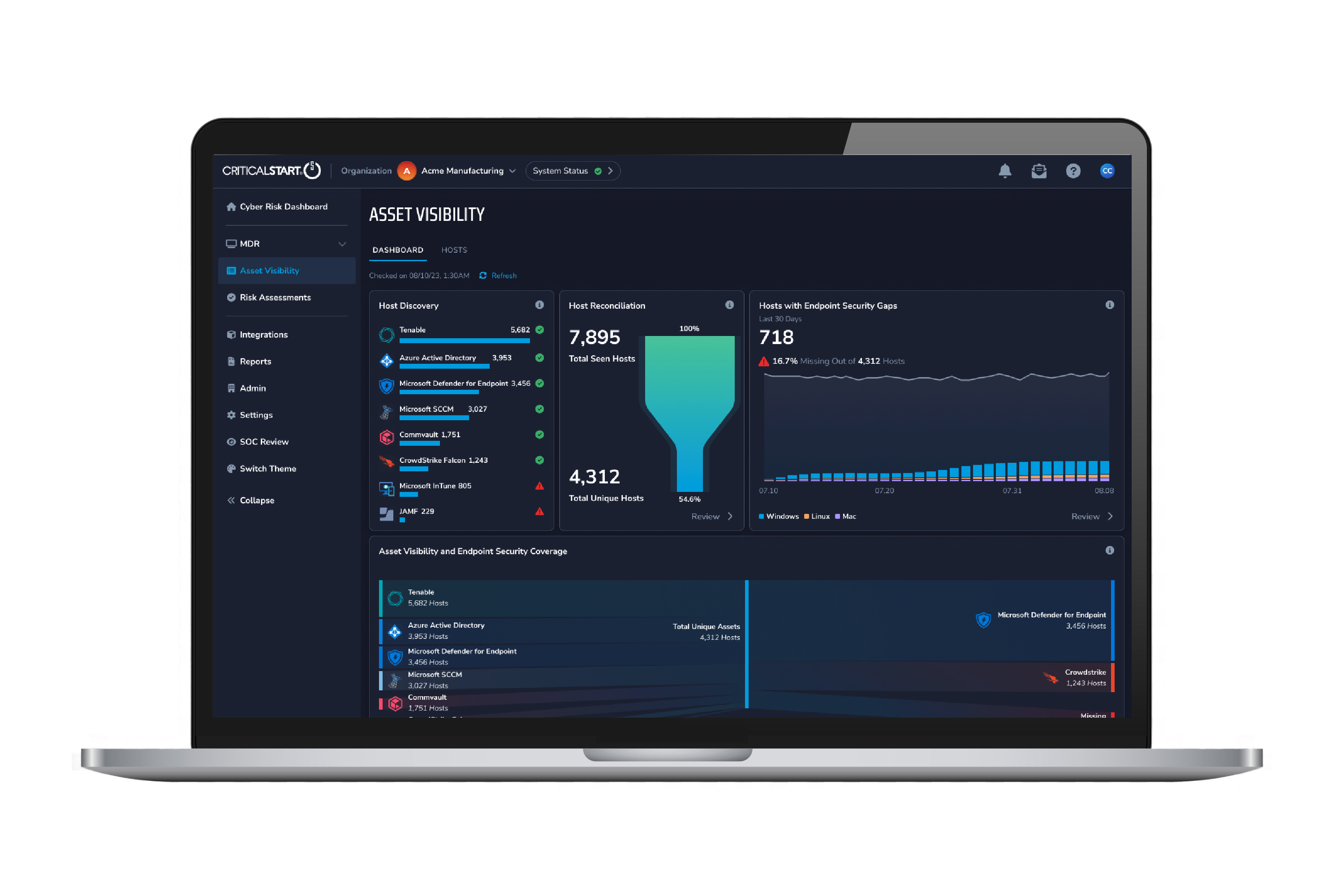
Find unsecured assets and close security gaps before attackers can exploit them with Critical Start Asset Visibility. Strengthen threat monitoring, speed response, and reduce risk with unified data from your existing security tools for enhanced visibility and control.
Combined with RSOC investigations, risk and compliance tracking, mitigation recommendations, and vulnerability data, teams use insights from Asset Visibility to get a holistic view of their organization’s risk posture and take action on risk remediation recommendations.

Risk-Based, Strategic Insights
CISOs gain the strategic insights needed to make data-driven decisions that reduce risk & optimize security investments

Improved Monitoring & Detection
Increased visibility and integration provide an enriched, real-time overview of critical systems and empower SecOps teams to thwart attackers by proactively closing security gaps

Enhanced Cyber Resilience
Collaboration between Security, DevOps, & IT teams refines response strategies & ensures proper controls are in place across endpoints, helping secure complex environments for increased cyber resilience from threats

Prioritize Optimization & Justify Spend
A unified Cyber Risk Dashboard provides metrics validating solution optimization & security efficacy, plus information on asset security status & risk reduction trends
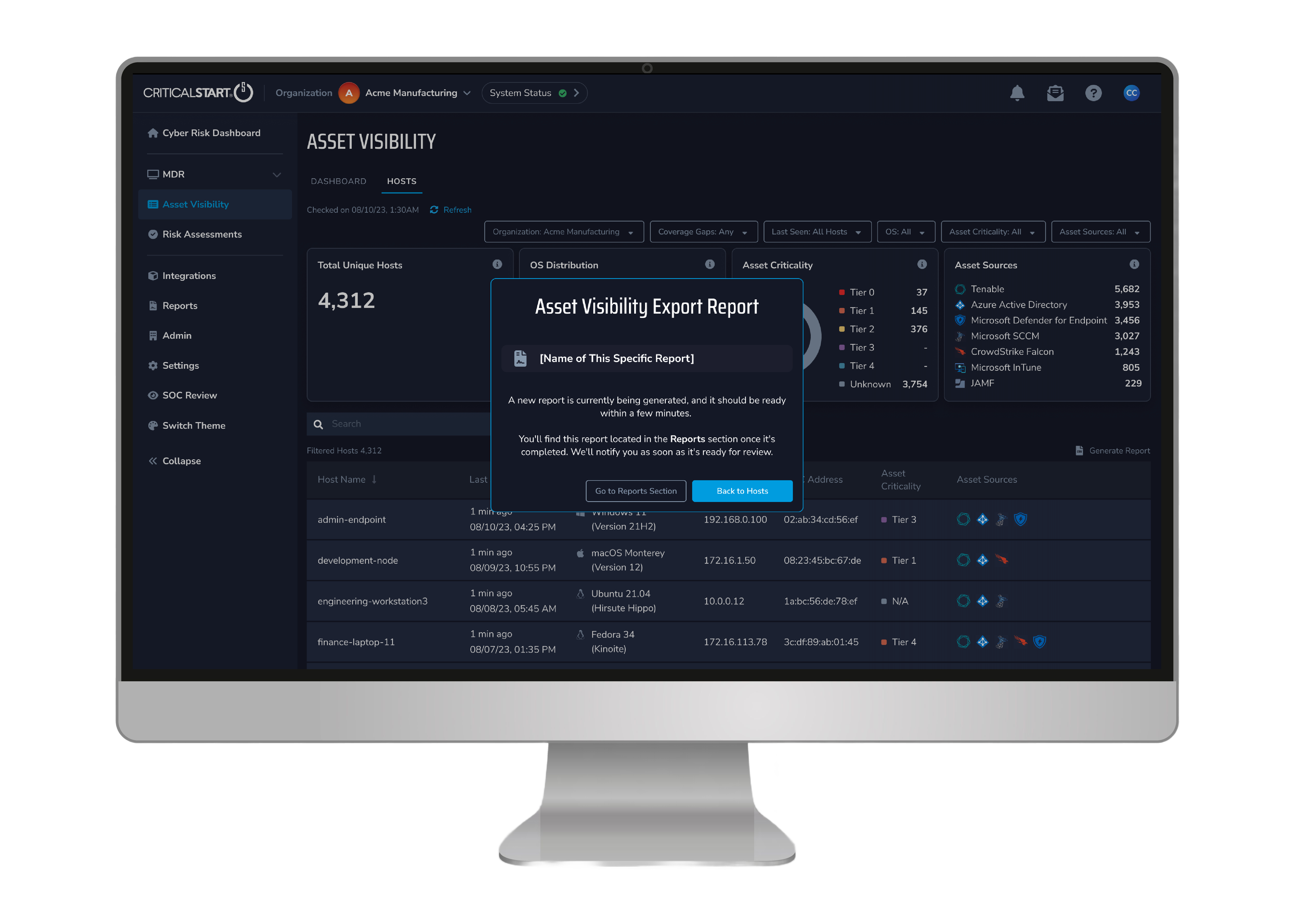
Gain visibility into all your assets across the entire IT ecosystem for a better understanding of the level of risk exposure your organization faces.
Rely on a single-source-of-truth asset inventory that stays updated even as assets change.
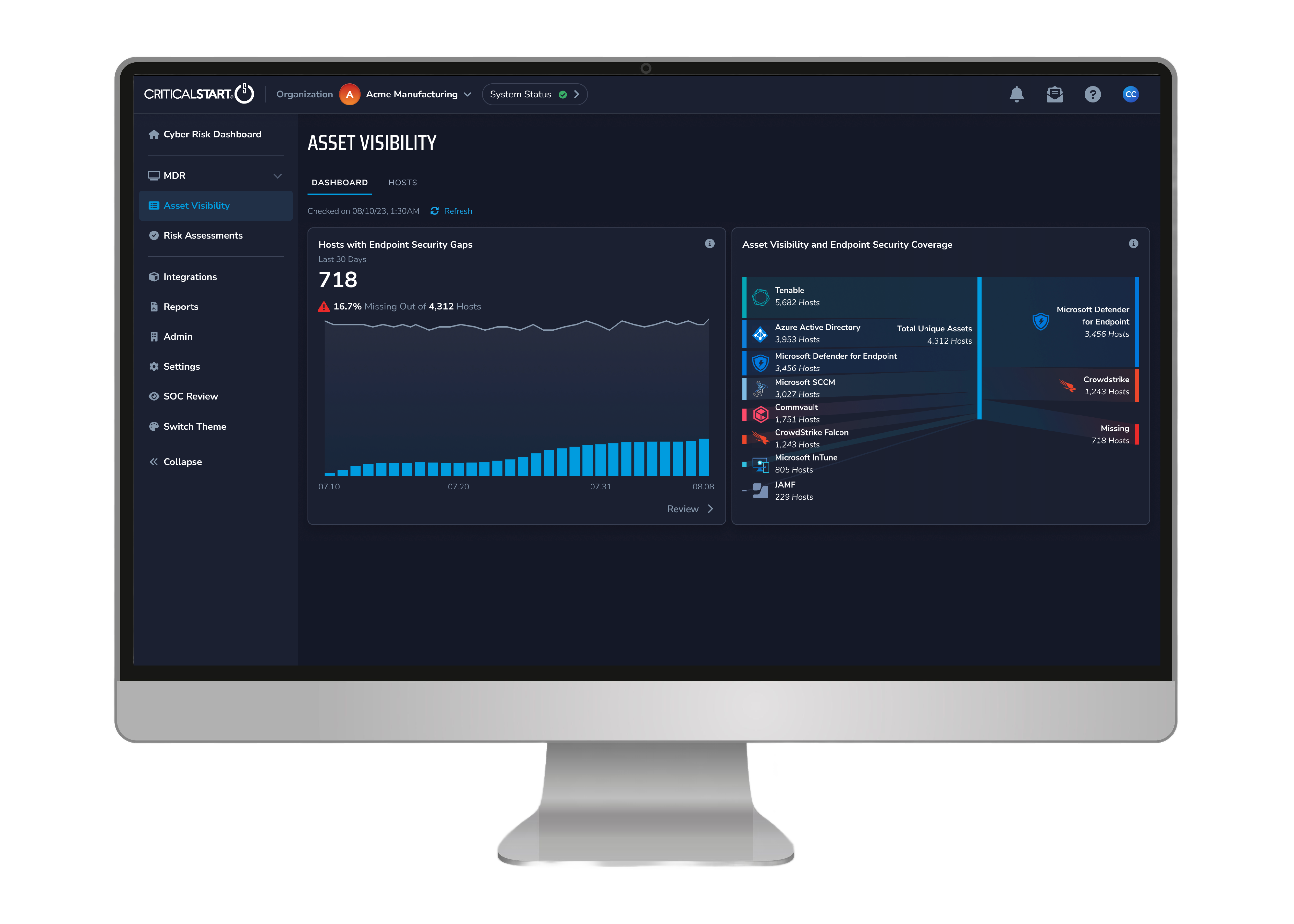
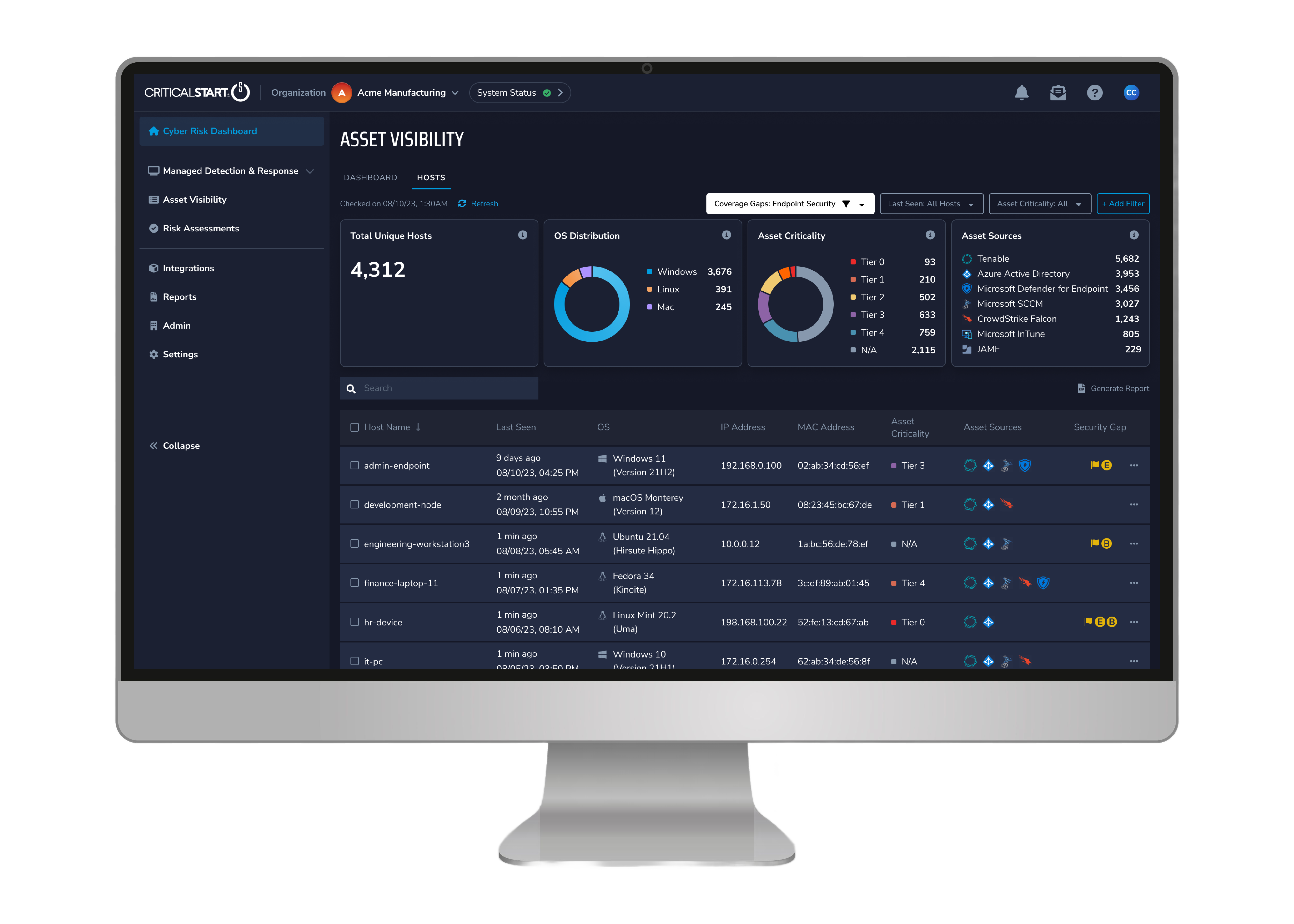
Pinpoint where you lack coverage using risk-aware gap analysis and create intelligent remediation plans that reduce the most risk and ensure the right controls are always in place.
Security teams can manage and control the dynamic nature of cyber risk exposure by staying up to date with changes across the business using the data administration and management features within Asset Visibility, including:
In addition to improving your NIST CSF maturity levels with continuous asset visibility across hosts, criticality ratings, and endpoint coverage gaps, Asset Visibility helps optimize your security programs and provides you with the most value from your cybersecurity investments.
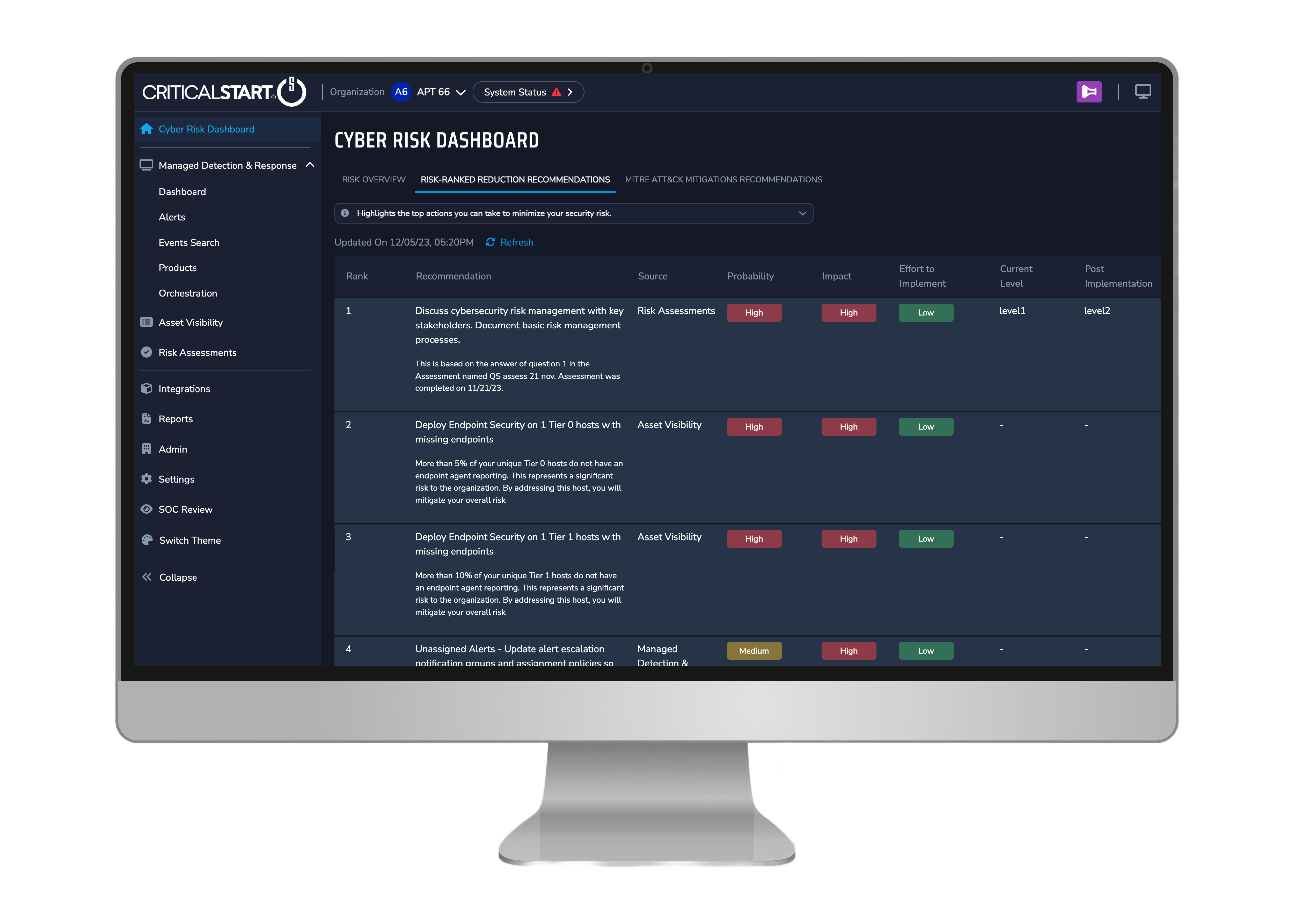
Asset Visibility is one of several data sources that feed into Critical Start’s Risk-Ranked Recommendations. With this data as part of the Cyber Risk Dashboard, you can analyze your organization’s security posture and risk exposure against best practices and peer benchmarks. You’ll gain the data-driven insights you need to continually take the next best actions that reduce the most risk.
Part of our Cyber Operations Risk & Response™ platform, Asset Visibility is available in two tiers to fit your unique cyber risk management needs:
Based on your unique cyber risk management needs, you can choose which offer gives your organization the expanded visibility and tighter control of endpoint security coverage it needs to fortify its defenses and keep ahead of risk.