HEADLINE HERE
Short intro text. 2 sentences max

Key Benefit
Description of benefit sentence….

Key Benefit
Description of benefit sentence….

Key Benefit
Description of benefit sentence….
Hear from Our Customers

Justin Hadley
The managed detection and response service has significantly increased our analysts’ efficiency to the point that they can focus on other areas of the business.
Sr Manager, Security Engineering, Alkami
How We Work Together
Text about our SOC and the different ways we communicate with them (email, phone, mobile app). Call out that we escalate only 1-2 alerts a day.
Applicable Video Content
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Tabletop Exercise
Moderated scenarios which test your organization’s ability to respond to simulated cyber attacks, disaster recovery and other crises to build resiliency.
Cybersecurity Readiness Assessment
Assess all aspects of your Cyber Defense Operations to evaluate opportunities for improving security architecture, tools and processes to enhance your cyber resilience.
Cyber Threat Hunting
Hypothesis-driven analysis across your network or specified hosts to proactively identify cyber threats based on investigative leads or indicators or Compromise (IoCs).
On-site Training
Experience instructor-led training in-memory analysis, host forensics, network forensics, threat monitoring and investigations/incident response.
Digital Forensics
For more sensitive investigations, we provide forensic services for legal, HR, compliance, and insider threat investigations.
Malware Reverse Engineering
Dynamic and static analysis of suspicious and/or malicious code to develop Indicators of Compromise (IoCs) and details to aid in identification of similar code and in threat hunting activities.
IR Monitoring
Deployment of EDR agents across your network or subset of endpoints to aid in the identification, containment, and remediation of threats and for targeted threat hunting operations.
Reports & Debriefs
Regularly scheduled client briefings as well as interim and final investigative findings reports.
See How BLANK Works with BLANK
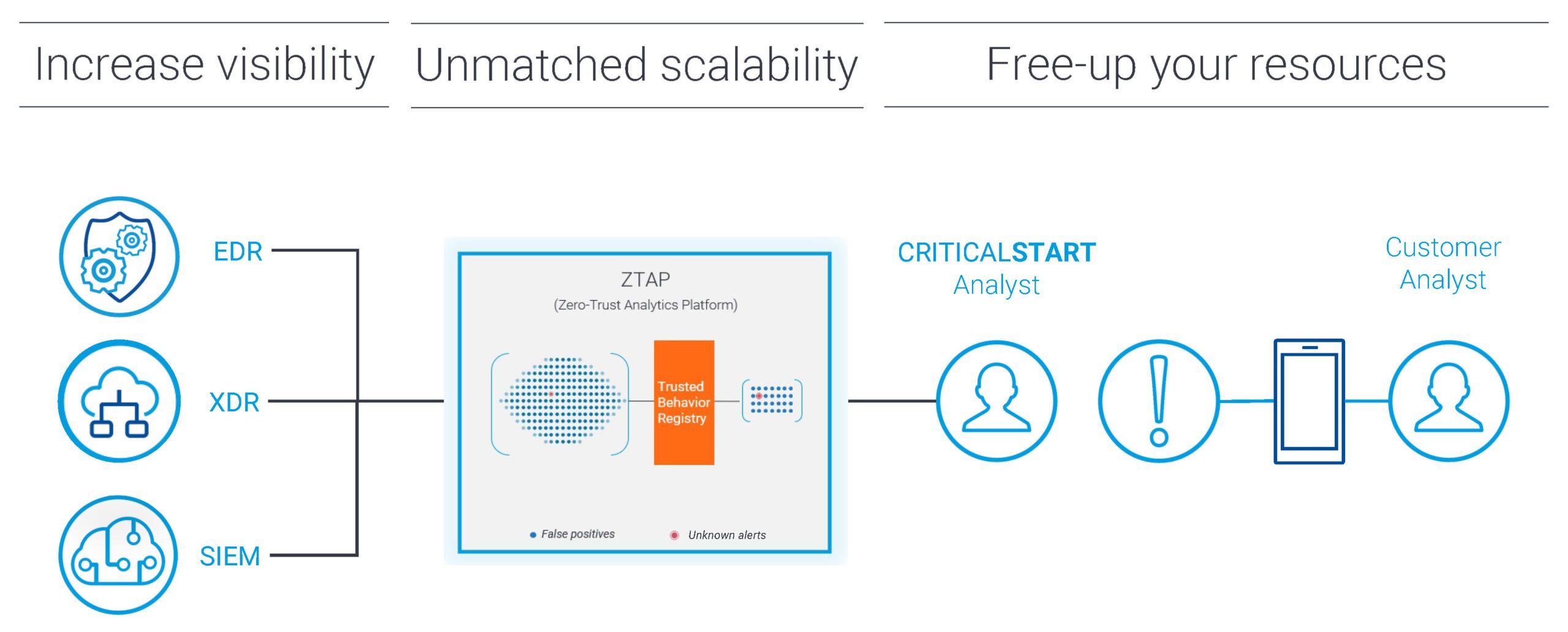
Resolve all alerts
- Trust oriented approach leverages the power of the Zero Trust Analytics Platform™ (ZTAP™) and Trusted Behavior Registry™ (TBR) to address all alerts
- We resolve more than 99% of alerts
- We escalate less than 0.1% of alerts – the alerts that really require the attention of your security team
Automated security + control to help you focus on what matters
Microsoft Defender for Endpoint is built on deep insights into operating system threats and shared signals across devices, identities, and information. Leveraging Microsoft automated alerts and actionable incidents, decide what to prioritize next on your Microsoft Roadmap and leave the research, false positives, and containment of infected devices to Microsoft and CRITICALSTART.
Integration, the better way
CRITICALSTART™ MDR services for Microsoft Defender for Endpoint leverage:
- Cross-operating system (Windows, Mac, Linux) Indicators of Compromise (IOC)
- Azure Active Directory as an identity provider, single sign-on, and user provisioning management
- Microsoft automated alerts and actionable incidents
- Cross-signal context in device timeline investigations
- Ability to pivot directly to the device timeline from any generated IOC
Goodbye portal fatigue
Comprehensive integration accelerates investigation and response with access to Microsoft Defender for Endpoint or Microsoft 365 Defender. Get Entities, Secure Score, Sign-In Details and related alerts—all in one portal. For each type of data source, such as email, identity and endpoint, we have built queries within this single portal so you can fetch other information for additional context.
Next-level expertise
- Security analysts have MS-500: Microsoft 365 Security Administration, SC200 and AZ-500: Microsoft Azure Security Technologies certifications
- Microsoft Security Best Practices are used to deploy Microsoft Defender for Endpoint to optimize Microsoft content for both Scheduled Query Rules and Indicators of Compromise (IOCs)
- We deliver 24x7x365 end-to-end monitoring, investigation, and response by highly skilled analysts
IOC Management? Hello optimized rules.
A key feature of the MDR service for Microsoft Defender for Endpoint is IOC management. Microsoft is the fastest-moving security company today. IOCs are published and updated hourly across different locations. Leveraging the CRITICALSTART™ Threat Navigator, we manage, maintain, and curate MDE out-of-box detections and IOCs. Detection content is also mapped to the industry leading, MITRE ATT&CK® framework.
How we do it
We take every alert from Microsoft Defender for Endpoint into ZTAP and match it against known good patterns in the TBR. If there is a match, the alert is automatically resolved and incorporated into the TBR. If not, our SOC investigates and proactively responds to stop the attack on your behalf, collaborating with you to remediate in minutes.
Never miss a threat. Or your desk.
Take threat detection and response on-the-go with our MOBILESOC® application. An industry-leading first, MOBILESOC puts the power of our ZTAP platform in your hands, allowing you to contain breaches right from your phone. Our iOS and Android app features 100% transparency, with full alert detail and a timeline of all actions taken.
add more details here and include words for SEO
Need MDR for other Microsoft security tools?
CRITICALSTART provides unified managed detection and response services for Microsoft 365 Defender, Microsoft Defender for Endpoint, and Microsoft Sentinel

DATA SHEET
Third-Annual CRITICALSTART Research Report reveals persistent challenges and some silver linings
It’s back! For the third year in a row, we have surveyed SOC professionals from across the industry to learn more about the issues and challenges facing the cybersecurity community and its workers.
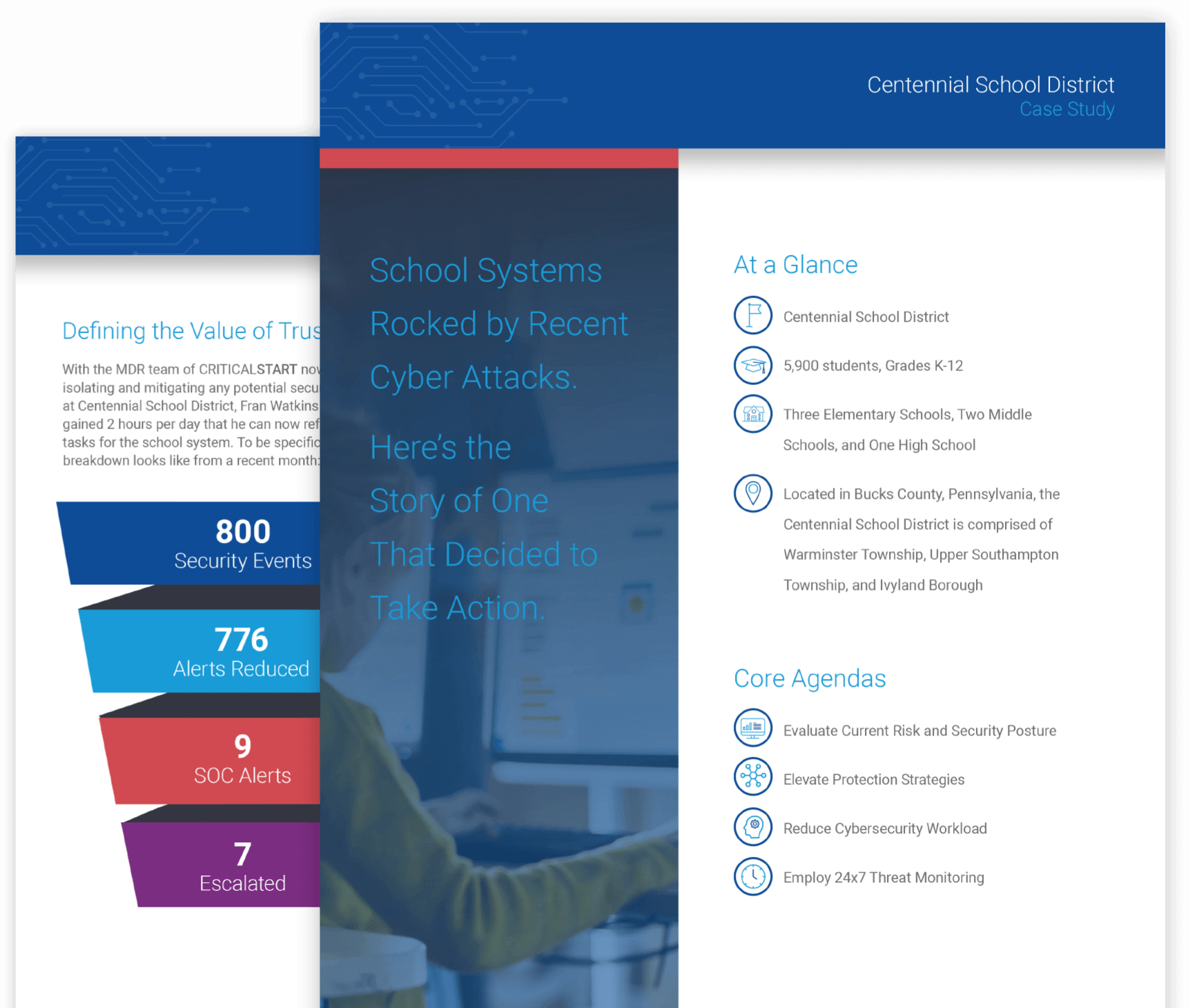
CUSTOMER STORY
Schools systems rocked by recent cyber attacks—but not this one
Learn how Centennial School District took action to prevent breaches by recognizing the critical importance of resolving every alert and working with an MDR vendor that provided trusted expertise through a technology-agnostic approach.
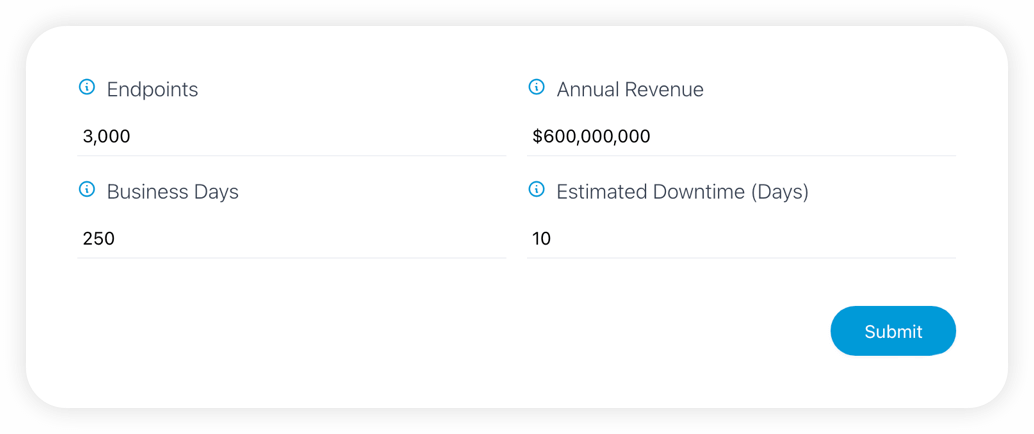
Calculator
Calculate your risk acceptance
Learn how CRITICALSTART Managed Detection and Response services can reduce your risk. Input values specific to your organization to calculate your risk acceptance.