Maximize the Value of Microsoft E5 Security with MDR Solutions and Services
Operationalize Microsoft Defender XDR for full threat detection and response outcomes
Cyberattacks are increasing across multiple vectors, including compromised credentials, email phishing and cloud misconfiguration. It’s no longer enough to just monitor endpoints – you need consolidated, comprehensive security coverage that protects your environment’s most vulnerable areas, including email, endpoints, user accounts and cloud-based applications. But where do you start?
Simplified and Effective Security that Stops Business Disruption

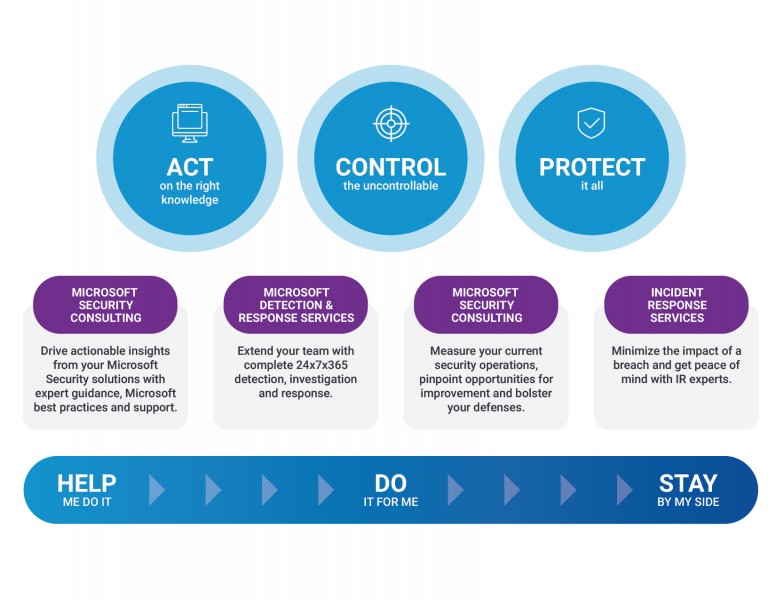
Improve security posture with Microsoft security experts who help you better understand your environment and map a strategy.

Get consolidated visibility and coverage across all attack vectors including email, users, identity, endpoints and hybrid, multi-cloud environments.

Detect and disrupt attacks during the attack chain with our expert-managed detection and response (MDR) guidance and support.

Speed up investigation and response across Microsoft Security environments with an extended team of security experts.

Security Manager
We have a small security team and were using disparate security controls that didn’t work well together – it was not an effective strategy. Our company was all-in on Microsoft E5 but we weren’t using the complete Defender security suite. It was a simple path forward to bring integrated threat protection from Microsoft and Critical Start MDR services together to drive simplified better security outcomes and improve our ability to meet global compliance requirements.”
Microsoft Sentinel, Microsoft Defender for Endpoint, Microsoft 365 Defender user
How Critical Start Helps You Realize Value from Microsoft Defender XDR
Protect everything, everywhere.
Given the volume and complexities of identities, data, applications, devices, and infrastructure, it’s essential to learn how secure your organization is now and how to mitigate and protect against threats moving forward.
- Develop a strategic plan customized to your organization’s priorities
- Implementation and onboarding focused on applying Microsoft security best practices and high-fidelity threat detection
- Continuous fine-tuning as new risks are identified
- Comprehensive coverage against attacks targeting your organization with the most effective MDR services powered by the industry’s only Cyber Operations Risk & Response™ platform
Extend your capabilities to quickly detect and respond to threats
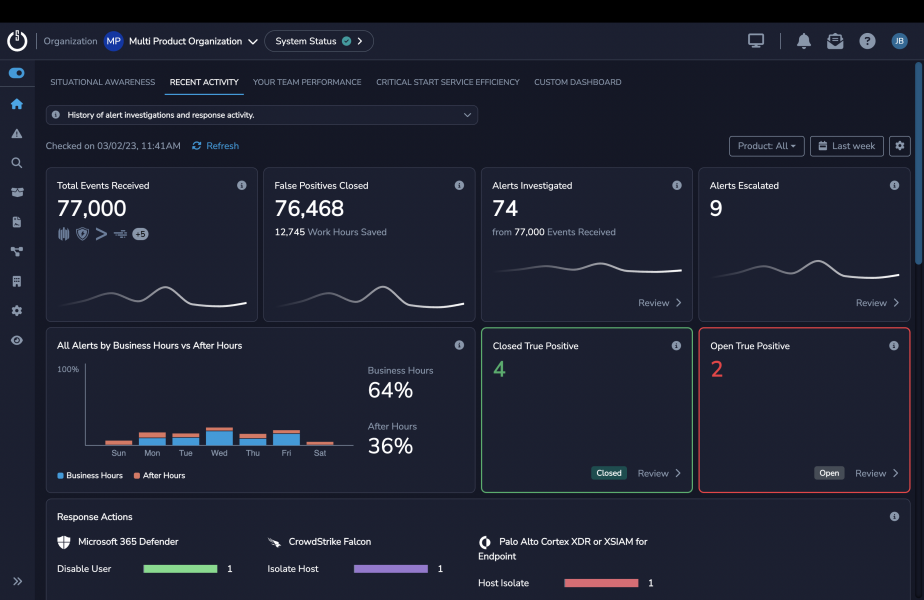
When minutes count, our Microsoft security experts can become and extension of your team and provide remediation and response actions to the threat as soon as it’s detected.
You’ll get:
- 24x7x365 monitoring, investigation, and resolution of all alerts and incidents
- Management of out-of-the-box Indicators of Compromise (IOCs)
- Freedom from intelligence overload
- Visibility across your Microsoft security controls in one portal

Advance security maturity with a focus on continuous improvement
With Critical Start, you have access to end-to-end solutions and services that move with you on your Defender journey, helping anticipate risk and strengthening security posture.
- Microsoft Security tools and our Cyber Operations Risk and Response™ platform are configured to eliminate false positives (>99% of alerts)
- Solutions for use cases like email phishing, brute force and stolen credential attacks, and attacks against cloud apps
- Indicators of Compromise (IOCs) mapped to the MITRE ATT&CK Framework
- Coverage of every alert and incident with a contractual 60-minute or less Time to Detection (TTD) and Median Time to Resolution (MTTR) SLAs
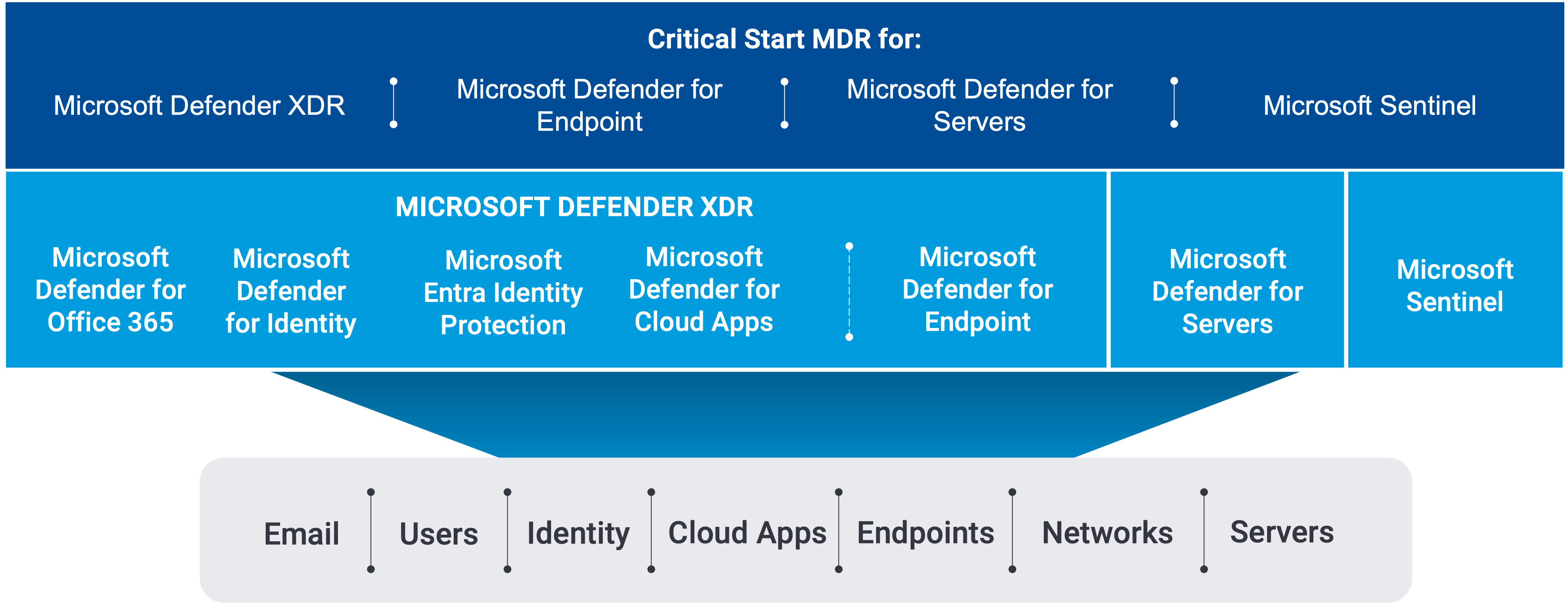
Protect it all with Microsoft Defender XDR
With your Microsoft E5 security license, you have access to the most robust, effective security control – Microsoft Defender XDR. With Microsoft Security Consulting workshops from Critical Start, we help you develop strategic plans customized for your organization to help you gain visibility and mitigate threats in your hybrid, multi-cloud environment.
Featured resources to learn how to maximize E5 licensing

eBook
Maximize the Value of Your Microsoft Security Investment and Unlock Your Security Potential
In this guide, learn how you can unlock your organization’s security potential with Microsoft E5

Blog
Support for Microsoft Defender XDR Extends Critical Start MDR Coverage Enterprise-wide
Learn how Critical Start MDR services for Microsoft Defender XDR bring you expertise, extend your team and help you stop breaches before they disrupt your business.

Guide
Guide to Managed Detection and Response and Microsoft Security
Learn Managed Detection and Response deployment Strategies to maximize protection and performance from Microsoft Security tools.

eBook
Three Step Guide to Materializing the Power of Microsoft Security
Within this guide, you’ll find step by step guidance to help you mature your Microsoft Security tools and approach breach prevention with simplified threat detection and response.