CRITICALSTART® MDR Services for Endpoint Tools
Achieve the full operating potential of your investments
Critical Start Managed Detection and Response (MDR) services protect your environment via our bi-directional integration with market-leading Endpoint Detection and Response (EDR) and Endpoint Protection Platform (EPP) tools.
Our MDR services are all about simplifying your operations, period. By leveraging the Trusted Behavior Registry® (TBR), our proprietary technology within the Cyber Operations Risk and Response™ platform, and Security Operations Center (SOC), we’re the only MDR provider in the industry that resolves all alerts.
Benefits of Critical Start MDR Services for Endpoint

A simplified view of everything
Consolidated and improved visibility of your environment all in a single interface.

Reduce the noise
Get fewer false positives over time which dramatically reduces alert fatigue and analyst burnout.

Improve your security posture
Our Cyber Research Unit (CRU) helps you stay ahead of the latest threats by adding MITRE ATT&CK® Framework-based proprietary detections and IOCs and third-party threat intelligence to your security tools.

Increase your SOC’s efficiency and productivity
We do all the heavy lifting for you, so you don’t have to.
How we work with you
We’re with you every step of the way – from onboarding through maturity.
-
Onboard: We will get you up and running as fast as possible: 4-6 weeks on average with total time to first value of approximately 5-10 business days.
-
Personalize: We continue to add value to your implementation by tailoring our MDR service to your unique needs through playbooks and procedures adapted to your environment to reduce false positives.
-
Investigate and Resolve: Once you’re up and running, our platform and our security analysts will monitor your environment 24x7x365 for potential threats. You can expect to see an approximate reduction in false positives of 90% on the first day of production monitoring.
-
Mature: We want to help you get the most out of your Endpoint tools, so we’re with you every step of the way. Your Customer Success Manager will check in with you regularly to ensure we’re meeting your expectations and our MDR services are helping you achieve your security goals.
Ready to respond 24x7x365
As the firefighters of cybersecurity, our certified security analysts help you contain and extinguish threats as quickly as possible to stop them from spreading. They:
- Operate as an extension of your security team
- Triage and investigate alerts that are not auto-resolved by our platform and the TBR
- Use your tools and our platform to respond to alerts on your behalf — depending on mutually agreed-upon rules of engagement
- Function as an open book with 100% transparency and visibility into every action taken

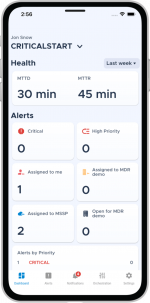
Fast resolution with MOBILESOC®
MobileSOC puts the power of our platform in your hands, giving you the ability to triage, escalate, and isolate attacks in-the-moment from your iOS or Android phone, regardless of your location or time of day.






