Reduce risk by optimizing your ability to detect and respond to cyberattacks
If your MDR service is only as good as the security signals it receives, you need a solution that provides premier MDR defense and maximizes the operational security potential of your Security Information and Event Management (SIEM) investment.
Let Critical Start free up your resources so you can focus on the priorities that matter most to your business.

Rapidly detect and respond
Leverage continuously updated threat intel from our Cyber Research Unit and 24x7x365 real-time monitoring and support from our Security Operations Center (SOC) analysts to stay ahead of new and emerging threats.

Proactively reduce risk
Take a holistic approach to risk mitigation by closing SIEM coverage gaps and leveraging MITRE ATT&CK® Mitigations Recommendations to prevent the same attacks from happening again.

Boost SOC efficiency
Offload Tier 1 and Tier 2 SOC support and stay ahead of threats with contractual SLAs of a 10-minute notification for Critical alerts and 60-minutes or less for Median Time to Resolution (MTTR), our Unified Timeline for streamlined investigations, and the “Who is on Call?” feature for efficient communication.

Accelerate the ROI of your SIEM
Get the highest combined value between log sources and threat detections. Our experts help you prioritize your ingest data and tune log sources to drive threat detection and enrich content needed for investigations.
Our MDR Services for SIEM are considered “comprehensive” for a reason
Meet your security goals with a risk-based approach to ensure optimal threat identification and containment. Take advantage of essential capabilities such as platform health and configuration, security and monitoring, investigation and escalations, custom dashboards, reports, log sources, and alerts.
A proactive approach matters
-
Proactively ensure you are receiving all alerts
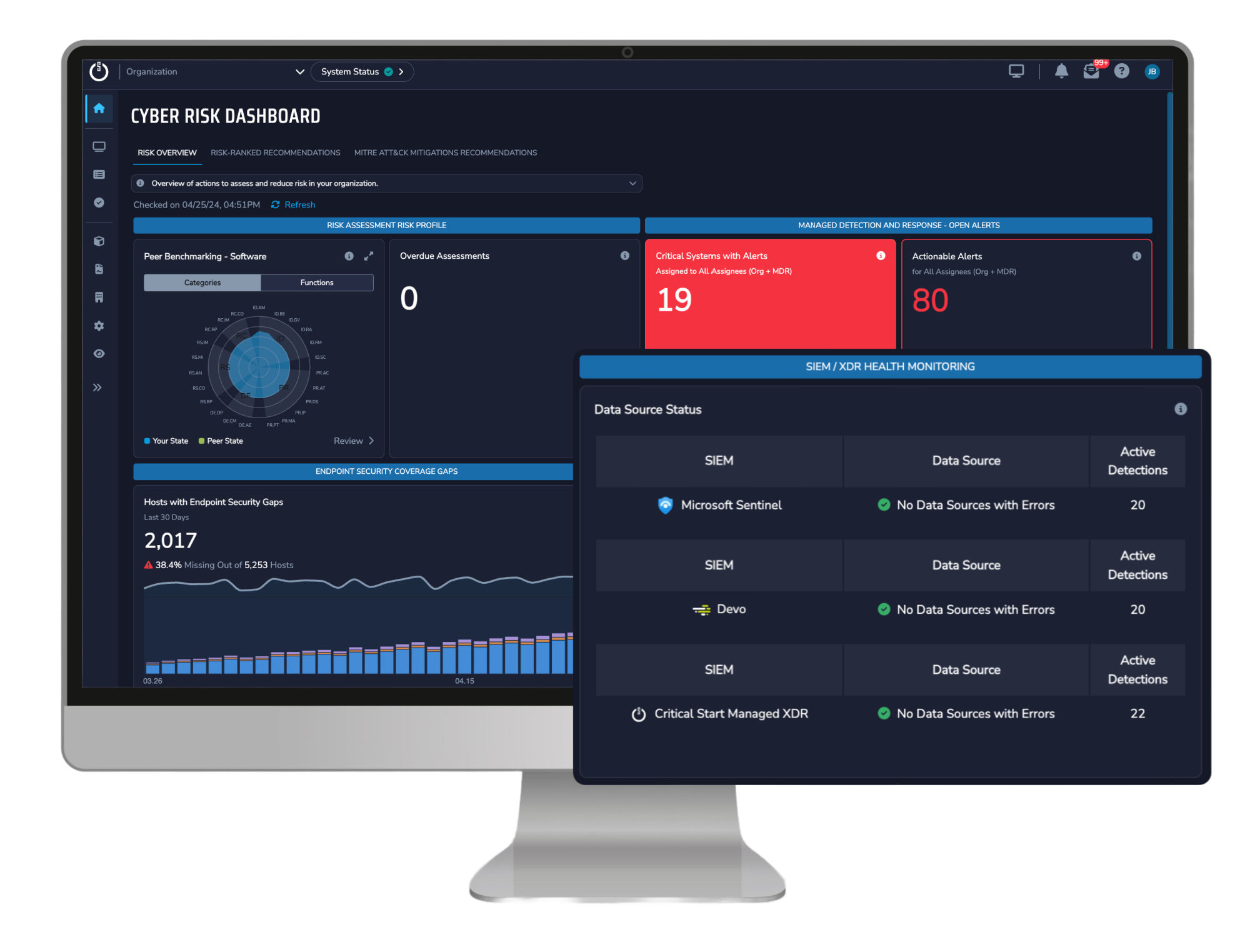
Would you know if suddenly one of your log sources had a feed issue? What would that mean when it came to monitoring for potential threats? Our Cyber Risk Dashboard shows you information on:- SIEM Coverage Gaps to show you are ingesting the most security-relevant SIEM log sources and that they are working correctly
- SIEM log and health monitoring and MITRE ATT&CK® Mitigations Recommendations help you identify and address potential security risks before they lead to incidents
Every alert matters
-
Resolve every alert regardless of criticality
Big attacks start small, which is why even “low-level” alerts are important to monitor. With help from our continuously trained SOC, and innovative, transparent technologies like our- Proprietary Trusted Behavior Registry® (TBR®) (the only purpose-built registry of known good behaviors) and our
- Cyber Operations Risk & Response™ (CORR) platform, which takes all the alerts generated—regardless of source—and quickly identifies and resolves known-good alerts
We escalate only 0.01% of alerts—the true positives—to your team for remediation
-
Better accuracy with a two-person integrity review on every action that could disrupt your organization
Every minute matters
-
Contractual SLAs of 10-minute notification for Critical alerts and Median Time to Resolution (MTTR) guarantees prompt attention and resolution
-
Streamlined investigations and efficient communications through our Unified Timeline and “Who’s on Call?” features minimize business disruption and increase SOC productivity
-
Triage and contain alerts at any time and in any place with our MOBILESOC® app to shrink dwell time and stop an attack before it becomes a breach, and get direct communication to the Critical Start SOC
-
Offload Tier 1 and Tier 2 support for 24x7x365 continuous monitoring to intercept malicious actors before the incident escalates

Every penny matters
-
Reduce Total Cost of Ownership (TCO) and holistically improve your security posture by allowing us to manage the back-end components and maintenance of your SIEM application, including version updates and application performance, improving team productivity and facilitating better resource allocation
-
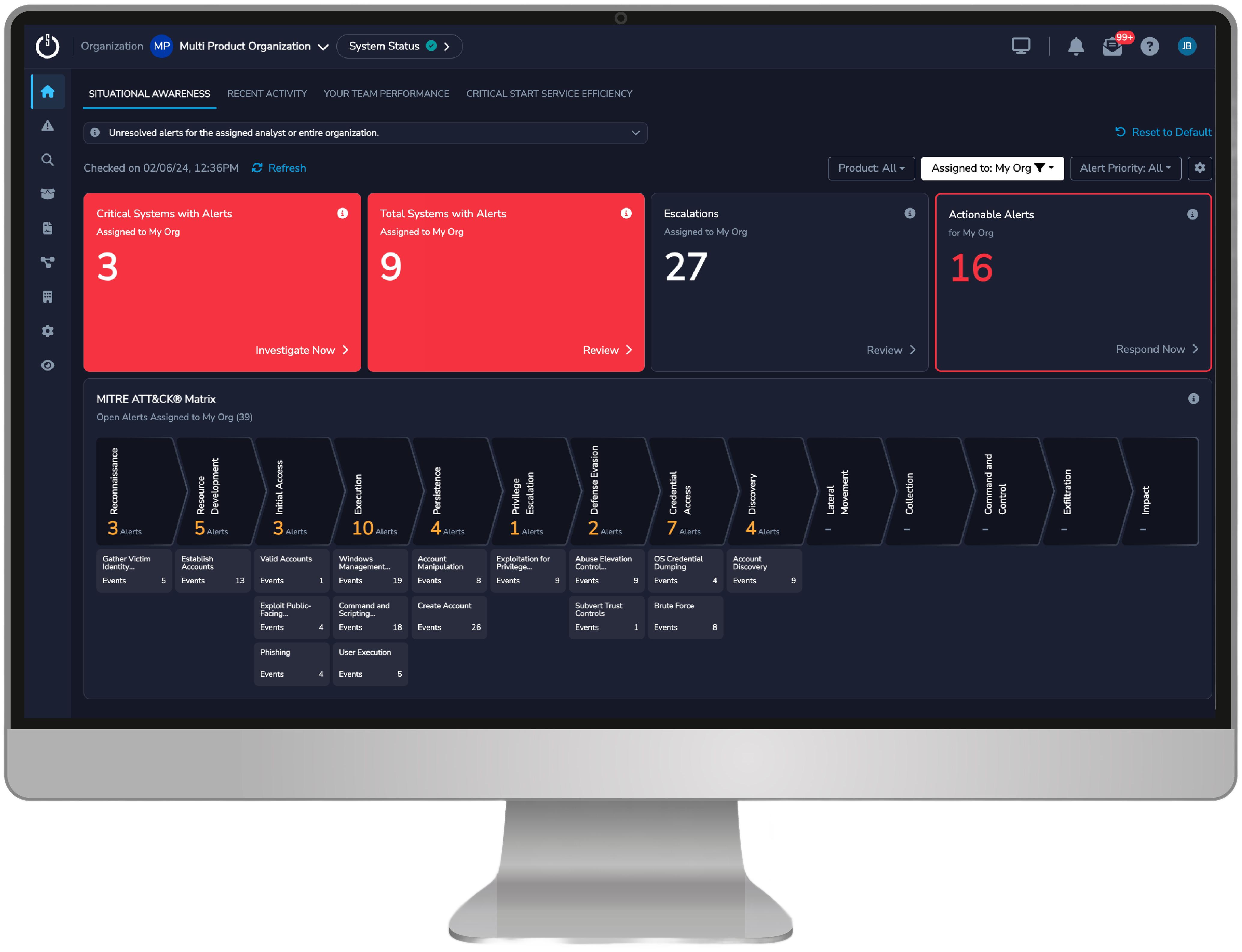
Provable ROI to ensure you are maximizing the operational and security potential of your MDR for SIEM service and getting full visibility into the performance, effectiveness, and efficiency of your security program thanks to detailed dashboards and reports, including Situational Awareness, Recent Activity, Team Performance, Critical Start Service Efficiency, and more
Context matters
-
Real-time visibility into your security posture with customizable dashboards and reports
-
Track Key Performance Indicators (KPIs), incident response metrics, and threat trends to gain valuable insights into your security operations
-
Map threat and detection content and open/closed alerts to the MITRE ATT&CK® Framework for alignment with industry standards
-
Advanced threat intelligence by our Cyber Research Unit (CRU) utilizes data from multiple sources to enrich the detection capabilities of your SIEM for comprehensive coverage of known threats and emerging attack vectors

The right logs matter
-
Identify potential threats by organizing and prioritizing logs for better log management and event correlation, closing security gaps and providing a holistic view of your organization’s security posture
-
Optimize breach protection with regular risk reduction reviews by experts who continuously monitor for high-fidelity data and analyze the potential impact of adding log sources and detection content
-
Advanced compliance monitoring and log management enhances your detection coverage and cybersecurity posture with managed capabilities that meet and exceed all the requirements outlined in the 2022 Gartner Market Guide for Managed SIEM Services
Want to learn more about how we take the stress out of managing your SIEM?
We help you alleviate the headaches of managing your own SIEM by providing the back–end services you need to reach the full operating potential of your SIEM and attain security maturity.

Is your SIEM security solution no longer enough?
Cyberattacks continue to evolve, and you should expect the same from your MDR provider. Learn the 10 ways an effective MDR provider can help keep your business safe from cyberattacks

Datasheet
MDR for SIEM
Our Managed Detection and Response (MDR) services for SIEM simplify the complexity of Security Information and Event Management (SIEM) tools and help you get the most out of your SIEM investment.

Buyer’s Guide
Guide to Security Services for SIEM
Optimize your SIEM and leverage MDR elevated through proactive security intelligence, flexible deployment options, and human-driven expertise to enhance your organization’s security posture and maximize return on investment.


