Cyber Risk Registers, Risk Dashboards, and Risk Lifecycle Management for Improved Risk Reduction
Just one of the daunting tasks Chief Information Security Officers (CISOs) face is identifying, tracking, and mitigating cyber risks. One of the biggest obstacles they encounter with risk is the cumbersome process of manually gathering and analyzing data from disparate sources to gain a comprehensive understanding of their organization’s risk posture. Many still rely on spreadsheets and other manual tracking methods, which are time-consuming, error-prone, and don’t provide real-time insights into continuous changes.
The lack of a centralized, automated system for monitoring and quantifying cyber risk leaves CISOs struggling to effectively prioritize security measures and allocate resources. Plus, the inability to clearly articulate where risk has been reduced and demonstrate the Return on Investment (ROI) of cybersecurity investments to stakeholders, further intensifies the challenges security leaders face.
To overcome the challenges of demonstrating effective cyber risk management CISOs must adopt a more streamlined, data-driven approach. This requires implementing advanced tools and platforms that can automate the collection, analysis, and visualization of risk-related data from multiple sources. By leveraging these technologies, security leaders can gain real-time, actionable insights into their organization’s risk posture, enabling them to make informed decisions, prioritize initiatives, and clearly communicate the impact of their efforts to senior management and boards.
Ultimately the key to successful cyber risk management lies in a CISO’s ability to transition from manual, fragmented processes to a more integrated, technology-driven approach that empowers them to proactively identify, track, and mitigate risks.
One invaluable tool in this ongoing battle is the cyber risk register—a comprehensive tool that tracks identified risks, their potential impact, and the strategies in place to mitigate them.
But what exactly is a cyber risk register, and how does it fit into the broader spectrum of risk lifecycle management? Read on to find out.
Understanding Cyber Risk Registers
A cyber risk register is a tool used to document, assess, and manage an organization’s cybersecurity risks in a structured, systematic manner. It serves as a centralized repository for recording identified risks, along with their potential impact to the organization, mitigation strategies, and steps implemented.
The cyber risk register is an essential component of an effective cybersecurity risk management framework. It enables organizations to maintain a clear, up-to-date understanding of their risk landscape, facilitating informed decision-making and resource allocation.
More than just a static document, a well-maintained cyber risk register is a dynamic tool that evolves alongside an organization’s risk profile. It is regularly updated to reflect changes in the threat landscape, the emergence of new vulnerabilities, and the implementation of new risk mitigation measures.
By providing a structured approach to managing cybersecurity risks, the cyber risk register helps organizations prioritize security efforts, ensuring resources are directed towards the most critical risks. It also serves as a valuable communication tool, allowing stakeholders across the organization to gain a shared understanding of the company’s risk posture and the steps being taken to address potential threats. It enables organizations to proactively identify, assess, and manage digital risks in an increasingly complex and dynamic threat landscape.
Recommended Reading Shifting Paradigms: Redefining Cyber Risk Assessments for Tangible Outcomes [Download White Paper]
Components of a Cyber Risk Register
Typical components of a risk register include:
- Risk Description: A clear, concise description of each risk.
- Risk Owner: The individual or team responsible for managing that risk.
- Assessment Scores: Numerical or qualitative scores indicating the risk’s likelihood and potential impact.
- Mitigation Measures: Specific actions taken to reduce or eliminate the risk.
- Status: The current state of the risk and its mitigation efforts.
The Benefits of a Cyber Risk Register
Implementing a cyber risk register within an organization enhances security posture while also improving the strategic and operational effectiveness of managing cyber risks. Here are some of the key advantages:
Improved Risk Visibility and Understanding
- Comprehensive Risk Overview: A risk register provides a centralized view of all identified cyber risks, making it easier for management and security teams to understand the full spectrum of threats facing the organization.
- Enhanced Risk Awareness: By documenting risks systematically, organizations can foster a culture of risk awareness among employees, ensuring that cybersecurity considerations are integrated into daily operations.
Enhanced Decision-Making and Prioritization
- Informed Decision-Making: With a clear assessment of each risk’s likelihood and impact, decision-makers can allocate resources more effectively, focusing on areas of greatest vulnerability.
- Strategic Risk Prioritization: The risk register helps in prioritizing risks based on their potential impact to the organization, ensuring that mitigation efforts are directed where they are most needed.
Streamlined Compliance and Reporting
- Compliance Management: Many organizations are subject to regulatory requirements (e.g., PCI DSS, HIPAA) regarding information and data security. A risk register aids in demonstrating compliance with these regulations by documenting risk management activities.
- Effective Stakeholder Communication: It serves as a valuable tool for reporting to stakeholders, including executive teams, boards, and regulators, providing transparency into the organization’s risk management efforts and cybersecurity posture.
Proactive Risk Management
- Preventive Action Planning: By identifying potential risks before they materialize, organizations can implement preventive measures, reducing the likelihood of security incidents.
- Dynamic Risk Management: The ability to update and adjust the risk register in response to new threats or changes in the organizational landscape allows for a more adaptive and proactive approach to cybersecurity.
Financial and Operational Benefits
- Cost Savings: Proactive risk management enabled by a risk register can significantly reduce the costs associated with cyber incidents, including data breaches, ransomware attacks, and system downtime.
- Business Continuity: By ensuring that critical risks are identified and mitigated, a risk register supports business continuity planning, reducing the risk of operational disruptions.
Implementing a cyber risk register offers a structured, effective approach to managing cyber risks. It not only enhances your organization’s ability to respond to threats but also supports strategic decision-making, regulatory compliance, and overall organizational resilience. The benefits of a well-maintained cyber risk register extend beyond the confines of cybersecurity, contributing to the stability and success of your entire organization.
A Cyber Risk Register’s Role in Risk Lifecycle Management
Risk Management Lifecycle is the systematic process of identifying, analyzing, evaluating, treating, monitoring, and reviewing an organization’s risks. The goal of this continuous cycle is to proactively manage and mitigate risks, ensuring strategic decisions align with organizational objectives while minimizing potential negative impacts. The lifecycle facilitates ongoing improvements in risk handling and security posture, adapting to new threats and changes in the organization’s environment. The cyber risk register is a key component in risk lifecycle management, offering a structured approach to identifying, assessing, mitigating, and monitoring digital threats.
- Identification and Assessment: Provides a framework for the systematic identification of risks and risk analysis, ensuring that efforts focus on the most significant threats.
- Mitigation and Prevention: By detailing mitigation strategies and assigning responsibility, the register ensures that actionable plans are in place to address identified risks.
- Monitoring and Review: Regular review of the register allows for the adjustment of risk response plans for new threats and the effectiveness of current measures.
- Reporting and Communication: Serves as a vital tool for internal communication and reporting to stakeholders, ensuring transparency and informed decision-making.
Best Practices for Maintaining a Cyber Risk Register
To maximize its effectiveness, a cyber risk register should be:
- Regularly Updated: Threat landscapes and organizational vulnerabilities change; your register should reflect this.
- Engaging Stakeholders: Incorporate input from across the organization to ensure a comprehensive risk assessment.
In the past a Risk Register template and an Excel file might’ve been the best (or only) option for risk lifecycle management. Fortunately, there are modern options that are more accurate, include automated features, and scale with an organization’s needs.
Recommended Reading Learn about the Cyber Operations Risk & Response™ platform by CRITICALSTART®, a cloud-native platform that combines cyber risk monitoring, posture and event analytics, and response orchestration in one place. [Download Datasheet]
Coming to Critical Start’s Cyber Risk Dashboard—Cyber Risk Register
A pivotal part of the Critical Start Cyber Operations Risk & Response™ (CORR) platform, the Cyber Risk Dashboard provides a holistic perspective for continuously assessing, monitoring, and mitigating your cyber risk exposure.
By adding the Cyber Risk Register to the Critical Start Cyber Risk Dashboard, you gain:
| Comprehensive Risk Assessment Prioritization | Incident Impact Analysis and Reporting | Risk Lifecycle Management | Collaborative Risk Mitigation Planning |
|---|---|---|---|
| Identify, categorize, and prioritize cyber risks using industry standards and best practices for a clear view of the cybersecurity landscape. | Analyze potential cyber incident impacts and generate detailed reports for internal and external stakeholders to communicate risk exposure effectively. | Manage the cradle-to-grave lifecycle of each identified risk, from initial detection through to resolution, ensuring continuous monitoring and updating of risk statuses. | Coordinate risk mitigation efforts across security, IT, and business teams with a centralized platform for tracking and updating risk statuses in real-time. |
The Cyber Risk Dashboard provides in-depth insights into different dimensions of organizational cybersecurity by integrating four key components: Risk Register, Risk Assessments, Risk-Ranked Recommendations, and MITRE ATT&CK® Mitigations Recommendations.
The Risk Register offers a dynamic, customizable dashboard for a comprehensive view of an organization’s risk landscape. Risk Assessments deliver continuous, data-driven security improvement beyond traditional assessments. Risk-Ranked Recommendations provide prioritized, actionable insights for budget-aware resilience across the IT estate.
Together, these components empower organizations to effectively identify, assess, prioritize, and mitigate cybersecurity risks.
Real-time and Historical Risk Visibility: Leverage the Cyber Risk Register to gain real-time insights and historical data analysis, enhancing the visibility of your organization’s risk landscape. This enables long-term trend analysis and maturity assessment.
Data-Driven Risk Management Utilize unlimited risk assessments and data-rich Risk-Ranked Recommendations from the Cyber Operations Risk and Response™ (CORR) platform to proactively manage cyber risk. These tools offer prioritized mitigation strategies and detailed peer benchmarking, providing the necessary insights to focus on high-impact areas and streamline risk governance.
Enhanced Decision-Making Support With executive dashboards that integrate insights from risk assessments and Risk-Ranked Recommendations, stakeholders gain a clear understanding of security performance relative to industry peers and can make informed decisions to optimize security resources.
Strategic Risk Mitigation Access actionable insights and specific mitigation recommendations tailored to your IT estate’s needs, using data from asset visibility, and alert analysis. This strategic approach allows for the prioritization and tracking of risk management activities, enhancing accountability and effectiveness.
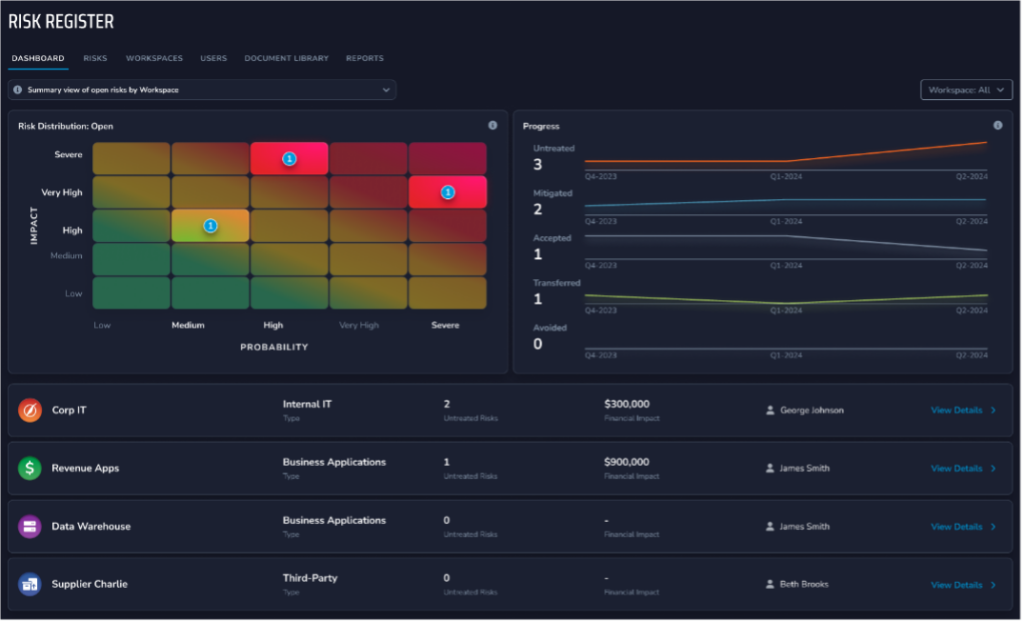
Comprehensive Risk Documentation and Reporting Simplify the documentation process and improve reporting capabilities with automated systems that track changes, monitor completion dates, and provide drill-down details for a deeper understanding of each risk.
Operational Efficiency and Strategic Conversations Save time and reduce operational complexities by consolidating risk data across the platform, using automated reminders and workflows to maintain up-to-date risk statuses. Shift from technical details to strategic risk conversations, ensuring that risk management aligns with broader business objectives.
Flexible Risk Management Framework The platform’s flexibility supports multiple cyber risk use cases and allows for the creation and management of customized workspaces tailored to specific organizational needs.
Recommended Reading Critical Start Cyber Risk Dashboard: Holistically Assess, Monitor, and Mitigate Cybersecurity Risk [Download Datasheet]
Cyber Risk Intelligence for Every Stakeholder
Proactive Cyber Risk Management | Security managers and CISOs gain from the Risk-Ranked Recommendations features which offer personalized, evidence-based insights. These tools help them proactively manage cyber risks by focusing on prioritized, actionable suggestions and benchmarking against industry peers, thereby enhancing their ability to safeguard the organization effectively.
Assessing Business Impact and Risk Focus | This feature is particularly beneficial for risk managers and business continuity planners who need to understand the monetary loss, probability, and impact of cyber risks. The Risk Overview and Risk-Ranked Recommendations provide them with crucial data to align security efforts with business operations and priorities, ensuring that resources are directed towards mitigating the most impactful risks.
Executive Decision Support and Peer Benchmarking | Executives and board members get a clear overview of the organization’s cybersecurity performance compared to industry peers. The Risk Overview and Risk-Ranked Recommendations equip them with the necessary data to support strategic decisions regarding cybersecurity investments and initiatives, enhancing their ability to oversee and guide the organization’s risk management strategy.
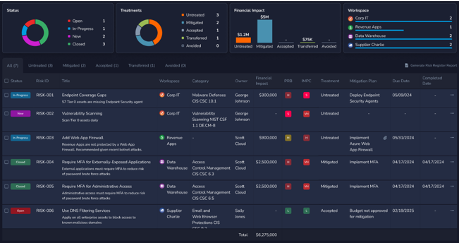
Proactive Risk Management | IT and security operational teams benefit greatly from the MITRE ATT&CK® Mitigations feature, which helps them implement recommended preventative controls. By focusing on proactive risk management, these teams can shift their efforts from reactive measures to preventing cyber attacks before they occur, optimizing their response strategies and enhancing the organization’s overall security posture.
Conclusion
A cyber risk register is more than just a list; it’s a strategic tool crucial for proactively managing digital threats. By systematically identifying, assessing, and mitigating cybersecurity risks, organizations can better protect their digital assets and ensure resilience in the face of evolving threats. To maximize its effectiveness, organizations must actively engage with this tool, keeping it updated to reflect the changing digital landscape.
By leveraging the cyber risk register as a strategic guide, organizations can proactively manage cybersecurity risks, allocate resources effectively, and ultimately foster a more secure future. Embracing the cyber risk register as a dynamic, vital component of your cybersecurity strategy is key to staying one step ahead of potential threats.
Want to Learn More?
If you’d like to learn more about Cyber Risk Register, and how Critical Start’s Cyber Risk Dashboard can give you in-depth insights into different dimensions of organizational cybersecurity, we can help. Click through below to get in touch with one of our experts.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
