The Next Evolution in Cybersecurity — Combining Proactive and Reactive Controls for Superior Risk Management
Evolve Your Cybersecurity Program to a balanced approach that prioritizes both Reactive and Proactive tools.
Back in 1987, when 5 1/4-inch floppy disks were the go-to for transferring data, the first antivirus software program was released. Since then both the threat landscape and security solutions have evolved, the latter cycling between detection (reactive) and prevention (proactive).
The primary reasons for these technological shifts are:
- Under-resourced Cyber Security Teams: With a workforce gap of 3.4 million at the end of 2022 in both headcount and expertise, exacerbating a security function that lags innovation in networking and infrastructure, security teams often shift focus based on the priorities of the business and the allocated resources. Adding further insult, 60% of organizations have trouble holding on to qualified cybersecurity professionals.
- Technology Advancements and Vendor Competition: According to Mimecast, 92% of companies plan to use AI and machine learning to bolster their cybersecurity. Market demands for improved ROI on security investments, coupled with rising regulatory requirements, have driven vendors to continuously innovate and compete to maintain their market share. The integration of technology advancements, machine learning, and AI has empowered cybersecurity vendors to develop more sophisticated detection and protection solutions.
- Cyber Criminal Innovation: Cybercriminals continuously evolve their Tactics, Techniques, and Procedures (TTPs). According to Cybersecurity Ventures the cost of cybercrime is predicted to hit $8 trillion in 2023 and will grow to $10.5 trillion by 2025. Cybercrime has become a lucrative industry that incentivizes malicious actors to constantly find ways to circumvent prevention measures and avoid detection. These cybercriminals employ various tactics to steal, destroy, or extort from their victims, posing a significant threat to individuals, organizations, and economies worldwide.
The result is a potentially costly — financial losses, loss of customer trust — game of whack-a-mole detecting new TTPs, then putting preventative controls in place while the attacker develops newer TTPs less likely to be detected. From the business’ perspective, this lag, providing a window of opportunity to attackers, represents risk.
What’s the difference between proactive and reactive security controls?
Reactive Cybersecurity
Reactive cybersecurity refers to an approach where organizations primarily respond to cybersecurity threats and incidents after they occur rather than taking proactive measures to prevent them. In a reactive cybersecurity posture, organizations are often caught off guard by cyber attacks and must scramble to contain the damage and mitigate the impact on their systems, data, and operations. Reducing dwell time, the period between the initial compromise and the eventual detection and mitigation of the threat, is essential. Fortunately, organizations are finding ways to do this: in 2023 the mean number of days to identify data breaches was 204 days, slightly less than 2022’s 277 days.
Here are some key characteristics of reactive cybersecurity:
- Incident Response: Reactive cybersecurity focuses heavily on incident response activities, such as identifying security breaches, containing the damage, and restoring systems and data to a secure state after an attack has occurred.
- Neglecting Patch Management: In reactive cybersecurity, organizations may struggle to keep their systems and software up to date with the latest security patches and updates. As a result, vulnerabilities may remain unpatched for extended periods, increasing the risk of exploitation by cyber attackers.
- Limited Monitoring: Reactive organizations may lack comprehensive monitoring capabilities to detect and respond to security threats in real-time. They may rely on basic security controls and periodic security assessments rather than continuous monitoring solutions.
- Ad Hoc Security Measures: In reactive cybersecurity, security measures are often implemented on an ad hoc basis in response to specific threats or incidents. Organizations may deploy point solutions to address immediate security concerns without considering the broader cybersecurity landscape.
- Lack of Proactive Planning: Reactive organizations may lack formalized cybersecurity policies, procedures, and incident response plans. They may not have dedicated resources or expertise to proactively assess and address cybersecurity risks.
- Limited Awareness and Training: In reactive cybersecurity environments, employees may have limited awareness of cybersecurity best practices and may not receive adequate training on how to recognize and respond to security threats. As a result, they may inadvertently contribute to security incidents through actions such as clicking on phishing emails or using weak passwords.
- Regulatory Compliance Focus: Reactive cybersecurity may be driven primarily by regulatory compliance requirements rather than a strategic approach to cybersecurity risk management. Organizations may focus on meeting minimum compliance standards instead of implementing comprehensive security measures to protect against cyber threats.
Overall, reactive cybersecurity can leave organizations vulnerable to cyber attacks and data breaches, resulting in financial losses, reputational damage, and legal and regulatory consequences. To improve cybersecurity resilience, organizations need to adopt a more proactive approach that focuses on prevention, detection, and response to cyber threats before they can cause significant harm.
Proactive Cybersecurity
Proactive cybersecurity maturity refers to the highest level of capability within an organization’s cybersecurity practices. It involves a forward-thinking approach aimed at anticipating, preventing, and mitigating cybersecurity threats before they can cause harm or damage to the organization’s assets, data, and reputation.
Key characteristics of proactive cybersecurity maturity are:
- Predictive Threat Intelligence: Proactive organizations invest in advanced threat intelligence capabilities to gather information about emerging cyber threats, attack techniques, and vulnerabilities. They use this intelligence to predict potential future threats and take preemptive actions to defend against them.
- Vulnerability Intelligence and Management: Identifying, evaluating, prioritizing, and mitigating security vulnerabilities in software, hardware, networks, and systems is essential for proactively addressing IT infrastructure weaknesses that can lead to security breaches and compromised data.
- Timely Patching: Promptly identifying and applying security patches to software, systems, and devices before vulnerabilities are exploited by attackers keeps you ahead of potential threats.
- Threat Hunting: Proactive organizations engage in proactive threat hunting activities to actively search for signs of malicious activity within their networks and systems. They use advanced analytics and security tools to identify and mitigate threats that may have gone undetected by traditional security measures.
- Continuous Monitoring: Proactive organizations implement continuous monitoring solutions to detect and respond to security incidents in real-time. They leverage technologies such as maturity assessments, posture and event analytics, and response capabilities to monitor for anomalous behavior and indicators of compromise.
- Response Orchestration: Proactive organizations automate routine security tasks and orchestrate response actions to improve efficiency and reduce response times. They use automation to handle tasks such as threat detection, incident triage, and vulnerability remediation, allowing security teams to focus on more strategic activities.
- Security by Design: Proactive organizations integrate security principles and controls into the design and development of their systems and applications from the outset. They follow secure coding practices, conduct security reviews throughout the software development lifecycle, and implement strong access controls and encryption mechanisms to protect sensitive data.
- Penetration Testing: Conducting periodic penetration testing to simulate cyber-attacks and identify vulnerabilities that malicious attackers could exploit and to assess the effectiveness of existing security measures.
- Collaboration and Information Sharing: Proactive organizations collaborate with industry peers, government agencies, and cybersecurity communities to share threat intelligence, best practices, and lessons learned. They participate in information sharing programs and forums to stay informed about emerging threats and leverage collective knowledge to enhance their cybersecurity defenses.
- Streamlined Collaboration and Tech Stacks: More isn’t necessarily better when it comes to cybersecurity. In fact, the EY 2023 Global Cybersecurity Leadership Insights Study shows reducing tech complexity and emphasizing automation and effective communication across an organization is common among the most effective CISOs.
- Security Awareness Training: According to the 2023 Data Breach Investigations Report (DBIR), “74% of all breaches include the human element, with people being involved either via error, Privilege Misuse, use of stolen credentials or Social Engineering.” Cyber threats are continually evolving, so ongoing training employees on security basics as well as emerging issues is critical. To err is human, but the fallout from an error doesn’t have to be catastrophic.
Overall, a proactive approach to cybersecurity requires a strategic mindset, continuous investment in people, processes, and technology, and a commitment to staying ahead of evolving cyber threats. It involves a culture of vigilance, resilience, and collaboration across the organization to effectively protect against cyber threats and safeguard critical assets and information.
Proactive v. Reactive – Which do you need?
As the title of this article states, you need both proactive and reactive measures to reduce your security risk. Finding the right mix of the two may seem overwhelming, but Critical Start Managed Cyber Risk Reduction (MCRR) significantly reduces the complexity.
How Critical Start MCRR Delivers the Right Blend of Reactive and Proactive Cybersecurity Capabilities
Consistently reducing cyber risk requires a unified, coordinated approach. Critical Start MCRR gives security leaders a solution that quickly, consistently identifies risk and ties risk analysis to actions that demonstrate measurable improvement. In addition to continuous risk monitoring, MCRR delivers it along with a human-led risk mitigation team that boasts over eight years of award-winning MDR services.
To help organizations achieve the highest level of risk reduction for every dollar invested, Critical Start MCRR is the only platform that includes:
Cyber Operations Risk & Response™ platform: Single platform that offers cyber risk monitoring with posture and event analytics, response orchestration, and threat intelligence.
Managed Detection & Response: 24x7x365 monitoring, investigation, and response backed by a contractual 10-minute response for Critical alerts and a 60-minute or less Median Time to Resolution (MTTR) Service Level Agreement (SLA) across every threat-centric alert type and every priority.
Controls & Signals Coverage Gaps: Address security controls gaps, including missing endpoint protection, additional log sources for Security Information and Event Management (SIEM) ingestion, and log source health monitoring to ensure the Security Operations Center (SOC) is receiving all expected threat signals.
MITRE ATT&CK® Mitigations: Receive prescribed actions to prevent an adversary from successfully executing techniques against your organization.
Peer Benchmarked Risk Assessments: Manage your cyber risk assessments conducted by third-party and self-assessments, compare to industry peer benchmarking, identify risk reduction priorities, and measure improvements over time.
Asset Inventory: Determine and maintain an accurate and persistent asset inventory of critical assets across your organization.
Vulnerability Prioritization: Identify and prioritize vulnerabilities to patch based on active targeting and exploitation by adversaries, level of effort to exploit, remote exploitation, availability of exploit kits, and dark web threat intelligence.
Incident Response: Incident Response (IR) retainer and readiness services with full incident and compromise scoping, triage, investigation, containment, eradication, remediation, and recovery.
| Recommended Reading Download How to Achieve Measurable Risk Reduction for a dive deep into what MCRR is and how it helps security and risk leaders measurably improve security posture and achieve the greatest risk reduction for the dollars spent. |
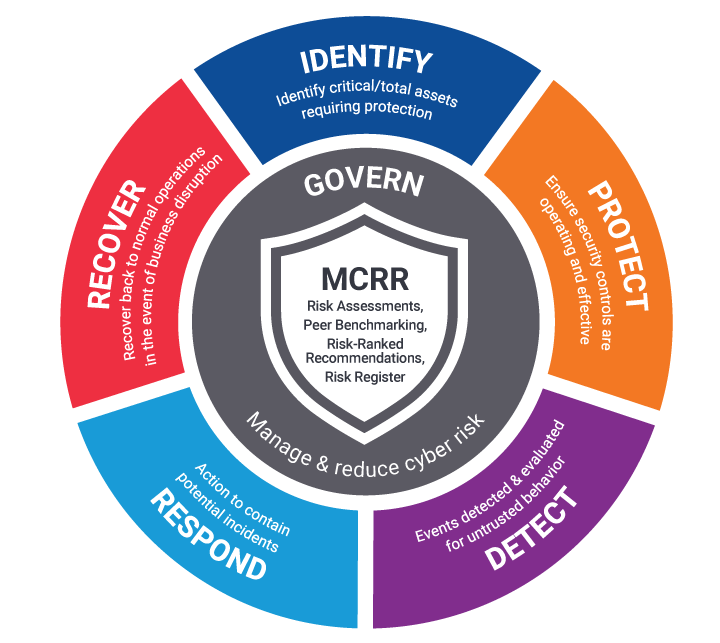
Critical Start MCRR and the NIST Cybersecurity Framework
A cybersecurity framework is a set of guidelines, best practices, and standards designed to help organizations protect their information systems and data from cyberthreats. It provides a structured approach to managing cybersecurity risks and ensures organizations have the necessary tools and processes in place to protect their critical assets. Choosing the right cybersecurity framework depends on several factors, including the size of your organization, your industry, and your specific needs. One of the most popular cybersecurity frameworks, the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), is widely adopted by both public and private sector organizations.
Critical Start MCRR provides a robust set of tools to address all six—Govern, Identify, Protect, Detect, Respond, Recover—aspects of the NIST CSF:
The Next Evolution in Cybersecurity
In 1987 5 ¼-inch floppy disks and an antivirus program might’ve been sufficient protection for your digital assets, infrastructure, and data. Technology, as well as the volume and sophistication of cyber threats, continues to evolve at a rapid pace. That means it’s critical for security leaders to have a proven, cost-effective, guided, and measurable approach to cyber risk reduction that goes beyond traditional manual, non-evidenced-based, limited-scope assessments and management of risks.
Evolving your security approach to include the right mix of proactive and reactive measures doesn’t have to be complicated or costly. With Critical Start MCRR your organization can have continuous security cyber risk monitoring and mitigation, enabling strong protection against threats. Combined with a team of expert risk mitigators, our platform provides maturity assessments, posture and event analytics, response capabilities, comprehensive threat intelligence, and security workload management capabilities. We help you achieve the highest level of cyber risk reduction for every dollar invested, leading to increased confidence in reaching your desired level of security posture. Speak with one of our experts, or request a demo, to get started today.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
