Navigating the Convergence of IT and OT Security to Monitor and Prevent Cyberattacks in Industrial Environments
The blog Mitigating Industry 4.0 Cyber Risks discussed how the continual digitization of the manufacturing sector has made cyberattacks a constant threat to organizations across all industries. When these attacks target critical infrastructure, the consequences can be far-reaching and devastating, as we saw in the Colonial Pipeline ransomware attack. What started as an attack on Information Technology (IT) systems ended up directly impacting Operational Technology (OT), leading to widespread public concern, fuel shortages, flight disruptions, and panic buying. This event serves as a stark reminder of the vulnerabilities created by the convergence of IT and OT systems and the urgent need for a holistic approach to cybersecurity in industrial environments by increasing risk resilience through the use of OT-specific data sources, custom OT threat detection, and the use of specialized workflows (existing child organizations, rules of engagements, and custom “Who’s on Call” scheduling).
The Colonial Pipeline Attack: A Closer Look
In May 2021, DarkSide, the self-styled “Robin Hood” of cybercriminal hacking groups (because they claimed to donate a percentage of the ransom they collected to charity), publicly stated that bringing down Colonial Pipeline, one of the most significant pipeline companies in the U.S., was never their intention.
However, as the saying goes, impact outweighs intent. When the consequences of the ransomware attack are viewed through the lens of the Effects-Based Classification System developed at the University of Maryland School of Public Policy by The Center for International Security Studies at Maryland (CISSM), we see the inevitability of OT system impact. Once the Colonial Pipeline breach had occurred, the need to shut down those public-facing systems was predictable and unavoidable due to convergence between IT and OT systems.
Understanding the CISSM Framework
To further illustrate the vulnerabilities created by the convergence of IT and OT systems, let’s take a closer look at the attack using the CISSM Framework (Fig 1) as our guide and explore the Primary, Secondary, and Second-Order Effects of the Colonial Pipeline cyber event. The CISSM Framework categorizes the effects of a cyber event into three levels: “the IT assets that work together to support particular organizational functions, the organization as a whole, and the interconnected system or systems of which that organization is a part.” This framework is particularly relevant in understanding the far-reaching consequences of cyberattacks in industrial and critical infrastructure environments.
The importance of OT organizations investing proportionally in cybersecurity solutions cannot be understated. These investments must align with the potential societal, financial, and business impacts and risks of their OT environments.
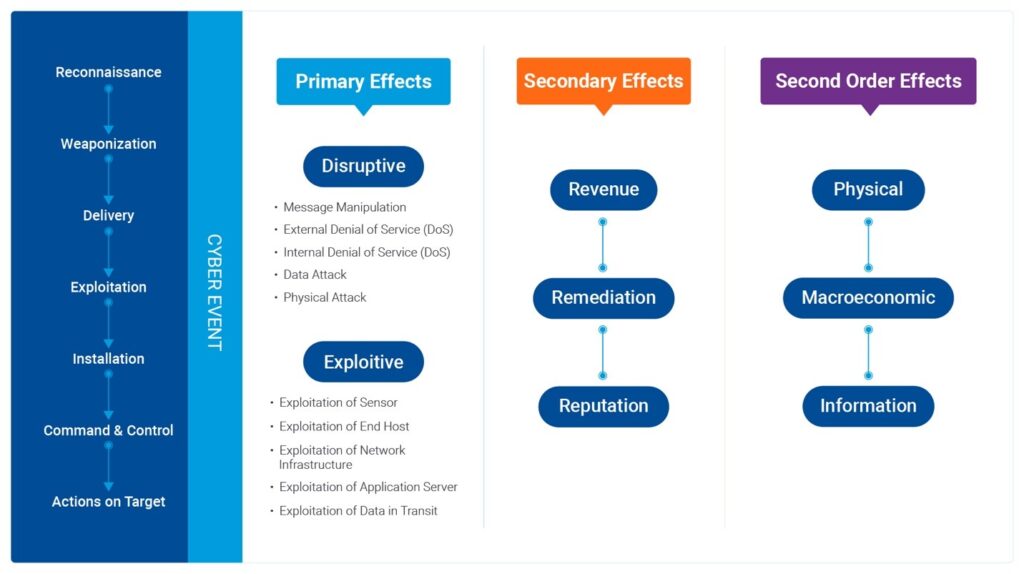
Fig 1. CISSM Framework showing Primary, Secondary, and Second-Order effects
Internet Technology (IT) and Operational Technology (OT) in Modern Industrial Environments: A Double-Edged Sword
As we’ve stated, the visceral effects felt across the southeastern United States, such as fuel shortages, flight disruptions, and panic buying, resulted from the attack on the company’s IT systems, not their OT or Industrial Control Systems (ICS) systems directly. However, these physical and macroeconomic Second-Order Effects were part of the fallout of the disruptive attack on Colonial Pipeline’s IT systems.
It is believed the Russian-affiliated Advanced Persistent Threat (APT) group FIN7 was behind the Ransomware as a Service (RaaS) software the DarkSide cartel used for the Colonial Pipeline attack. After the attack led to the business’ risk management decision to voluntarily shut down the pipeline, DarkSide issued a statement on their website saying, “Our goal is to make money and not creating [sic] problems for society.”
The ramifications of high-profile attacks such as this one often impact connected systems. Even if DarkSide’s intention was solely to use the Internal Denial of Service (DoS) and Data Attacks to exfiltrate nearly 100GB of data within a two-hour period before using ransomware to encrypt Colonial Pipeline’s IT systems for monetary gain, the repercussions of their actions didn’t stop at the Primary Effects of the cyber-attack itself.
Lessons Learned from the Colonial Pipeline Attack
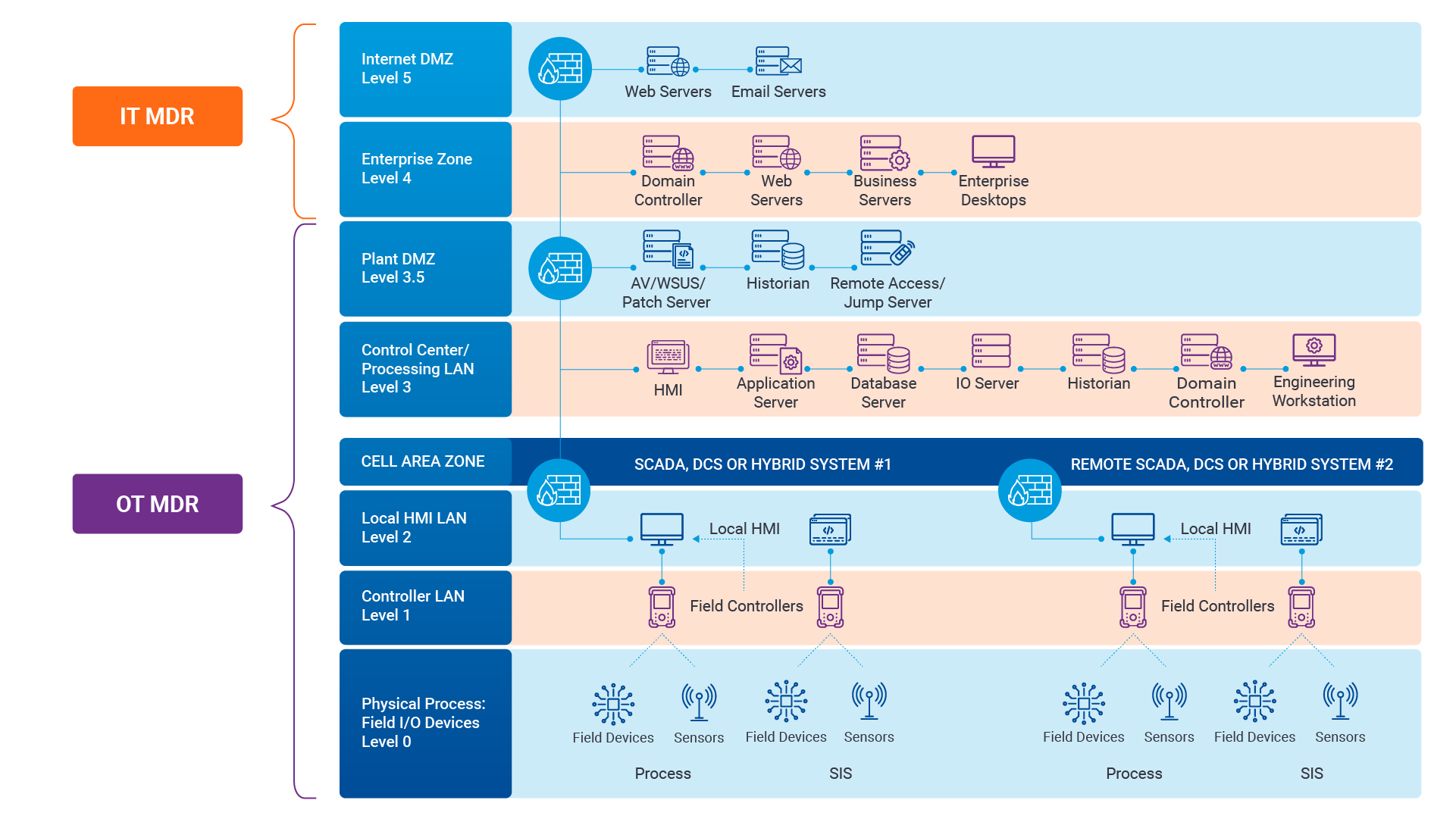
OT systems are designed and operated differently than IT systems. The Purdue Model is a widely adopted framework that segregates the logical (software) and physical (hardware) components of OT systems into distinct levels while also illustrating the interconnections and data flows between them. (Fig 2) The Colonial Pipeline attack targeted the company’s IT systems, primarily affecting Levels 4 and 5 of the Purdue Model.
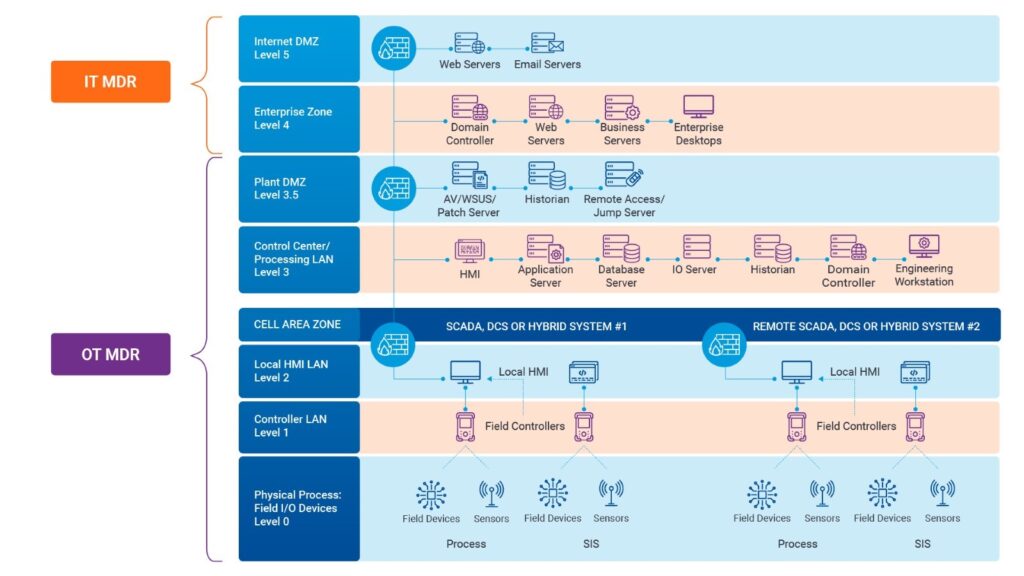
Fig 2. The Purdue Model for Industrial Control Systems (ICS)
First, the DarkSide threat actors exploited a compromised Virtual Private Network (VPN) password to gain initial access to Level 5, Colonial Pipeline’s enterprise network, allowing them to move laterally and target critical systems. From there, they gained access to Level 4, the business logistics systems, which enabled them to encrypt critical business data and demand a ransom payment.
While DarkSide didn’t directly target or compromise the OT systems represented in Levels 0-3 of the Purdue Model, the APT group associated with the attack, FIN7, has a history of targeting critical infrastructure, which suggests they may have had a vested interest in disrupting the pipeline’s operations and cleverly manipulated DarkSide for just such an outcome. This manipulation triggered Colonial Pipeline to shut down the physical pipeline infrastructure, directly impacting their Level 0 systems and, by extension, the community that depended upon those systems.
- Level 0, Physical Processes: Includes the actual equipment, machinery, and assets being controlled or monitored, such as the pipeline, valves, pumps, and other physical components in the case of the Colonial Pipeline
The involvement of FIN7 is important to note because it shows how State Actors’ capabilities can be targeted against any commercial ransomware target. According to a recent article in CPO Magazine, “Open attacks on critical infrastructure are a relatively new phenomenon, only becoming a major issue with 2021’s Colonial Pipeline and JBS incidents, and thus far have mostly been the work of private for-profit criminal actors.”
The presence of the APT group was another reason the operational impact of the DarkSide ransomware attack served as a wake-up call to organizations with OT and ICS environments everywhere. The lessons learned from the Colonial Pipeline attack showed organizational leaders how a breach in the IT environment could have significant repercussions in their OT and ICS environments, underscoring the critical importance of
- Regularly updating and patching IT and OT systems to minimize vulnerabilities
- Implementing network segmentation to reduce the risk of successful cyberattacks, and
- Developing and testing incident response plans to help quickly and effectively respond to cybersecurity incidents, mitigating the Secondary and Second-Order Effects of a cyber event
Colonial Pipeline’s Response to the Attack: Mitigating Secondary and Second-Order Effects
In response to the attack, Colonial Pipeline leadership took defensive measures to prevent potential risks to their OT systems. The Second-Order Effects of their decision to take their OT systems offline included physical and macroeconomic consequences, which caused significant downtime and resulted in millions in lost revenue, legal expenses, and technical debt. Shutting off those systems, however, gave them time to assess the extent of the damage, restore systems from backups, and ensure the safe resumption of operations without the potential risk of the hacker group moving laterally into the OT control systems.
This financial impact of sacrificing revenue to remediate a significant security breach and conduct reputational damage control was well above the $4.4M cost of the ransom, underscoring the potential costs of a cyberattack and the importance of investing in end-to-end cybersecurity solutions.
These are casebook examples of the Secondary and Second-Order Effects pillars of the CISSM Framework, highlighting the hidden costs and losses attributed to cyber events, including those caused by ransomware attacks.
The Importance of a Holistic Approach to IT/OT Security
The Colonial Pipeline attack shows the importance of a holistic IT/OT security approach. DarkSide began the initial attack and data theft on May 6th, but it wasn’t until May 7th, when the ransomware attack began, that Colonial Pipeline became aware of the breach. At that point, the leadership team decided to take all systems offline.
Would those Second-Order Effects decisions have been necessary, however, if they believed they had a trusted monitoring solution wrapped around their OT network to detect and prevent additional movement so they could keep their critical infrastructure systems online? It’s understandable why they wouldn’t want to take the chance.
According to Sophos’ State of Ransomware 2023 study, ransomware payouts and recovery costs increased significantly, from $812,380 in 2022 to $1,542,333 in 2023. Of those surveyed, 56% of manufacturing and production organizations reported being hit by a ransomware attack in the past year.
Attacks on critical infrastructure will only continue to escalate, especially as 2024 is considered a “Superbowl of an election year,” with 83 national elections held across 78 countries worldwide—something that we most likely won’t see again until 2048. The increase in geopolitical tensions and the appeal of causing real-world disruptions to create a climate of confusion and distrust to potentially influence election outcomes may result in a higher-than-usual number of threat actors tampering with or shutting down critical infrastructure by exploiting vulnerabilities in converged IT and OT systems.
The 2023 Gartner® IT/OT Alignment and Integration Survey, referenced in a recent Gartner report, shows we may already be trending in that direction. Quoting directly from the Gartner report, it found that:
- “Cybersecurity is high on the list of both benefits and challenges. This concern is well-founded because only 34% of respondents avoided security incidents.”
- 40% of respondents have experienced a security incident that disabled systems
- “8% experienced a security incident that disabled both enterprise IT and operational or mission-critical systems”
- “Security and process integrity risks are top concerns in IT/OT data integration. 13% experienced a security incident that disabled OT but did not impact the enterprise IT systems. This has increased from 9% in the 2021 survey.”
What’s unique about manufacturing, however, is that regardless of the system compromised, like an OT device in the 2015 Ukrainian Power Grid Attack (Level 3), or an attack spreading from IT systems (Levels 4-5) to OT systems (Levels 0-3), as they were in the
- 2024 Sandworm cyber-physical system attack “test” (not for ransom) that caused a water utilities tank overflow in Muleshoe, Texas, the
- 2023 Cyber Av3ngers ransomware attack that resulted in the Municipal Water Authority of Aliquippa, PA going into manual operations, or the
- 2021 REvil ransomware attack on JBS that led to the suspension of operations at several meat processing plants in the U.S., Canada, and Australia and disrupted meat supply chains,
these attacks are often detected and reported through the company’s IT network.
As these examples show, “air gapping” IT and OT systems isn’t sufficient to prevent a threat actor’s reach, and detection and reporting of cyberattacks in OT and ICS environments can’t rely on OT system monitoring alone.
Custom detections for high-priority use cases like IT/OT boundary traversal and network segmentation violations, robust endpoint protection and monitoring, and 24x7x365 end-to-end visibility across both domains are critical for detecting and responding to threats that may originate in the IT environment but ultimately target OT systems, as well as those that emerge directly within the OT landscape. Had these cybersecurity measures been in place, Colonial Pipeline may have been able, at the very least, to prevent the shutdown of their critical infrastructure.
The Way Forward: Implementing Comprehensive Cybersecurity Measures
The convergence of IT and OT systems continues to shape the future of industry, making it increasingly clear that organizations must implement robust security measures and monitoring capabilities that include a combination of IT network security controls and human vigilance to promptly detect and respond to cyber threats.
The Colonial Pipeline attack was the first major wake-up call for organizations with OT and ICS environments. The current global geopolitical situation and APT trends tracked by cybersecurity firms like Mandiant continue to demonstrate the critical importance of implementing comprehensive cybersecurity measures encompassing IT and OT systems.
As the convergence of these systems continues to shape the future of industry, organizations must remain vigilant and proactive in their approach to cybersecurity. One effective strategy for enhancing IT/OT security is adopting a risk-based approach to cybersecurity and prioritizing the protection of critical assets and systems that can help organizations effectively allocate resources. By adopting a holistic strategy that includes robust monitoring, detection, and response capabilities, organizations can effectively navigate the challenges of IT/OT convergence and safeguard their industrial environments and operations against the continual onset of cyberattacks.
To learn more about protecting your OT and ICS environments, read our datasheet.

Director, Product Management | SIEM MDR
Steven Rosenthal, a cybersecurity expert, has spent his career assisting organizations in navigating technology threats. His experience includes a 12-year stint at IBM, managing complex data center projects, and leading IT program development at Dell EMC. As QTS Data Centers’ Head of Product Solutions, he guided product strategy and elevated the company’s market position. Steven is currently the Director of Product for Critical Start, where he shapes the company’s SIEM strategy and bolsters its cybersecurity posture. As a respected thought leader, Steven frequently shares his insights at industry events to help drive innovation and guide companies in building resilient and secure infrastructures.
You may also be interested in…
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)