CISO Perspective with George Jones: The Top 10 Metrics for Evaluating Asset Visibility Programs
In today’s rapidly evolving cybersecurity landscape, the ability to effectively manage and secure digital assets is paramount. Organizations face a multitude of threats ranging from sophisticated cyberattacks to regulatory compliance challenges, making asset visibility a cornerstone of their defense strategies.
The Importance of Asset Visibility in Cybersecurity
Asset visibility, simply put, refers to the comprehensive understanding and monitoring of all digital assets within an organization’s network. These assets encompass a wide array of devices, applications, data repositories, and endpoints. In an era where digital transformation is accelerating and remote workforces are increasingly prevalent, maintaining a clear and up-to-date inventory of these assets is more critical than ever before.
The significance of asset visibility in cybersecurity cannot be overstated. It forms the foundation upon which robust security measures are built. Without a thorough understanding of the assets within their environment, organizations are left vulnerable to a plethora of risks, including unauthorized access, data breaches, and regulatory non-compliance. Asset visibility serves as the cornerstone for effective risk management, enabling organizations to identify, prioritize, and mitigate security risks and vulnerabilities in a proactive manner.
Measuring Success in Asset Visibility Programs
While the importance of asset visibility is widely acknowledged, the effectiveness of asset visibility programs is often measured by their ability to achieve predefined objectives and outcomes. This necessitates the establishment of clear metrics and key performance indicators (KPIs) to gauge the success of such programs.
Measuring success in asset visibility programs entails more than just identifying the presence of digital assets. It involves assessing the accuracy, timeliness, comprehensiveness, and impact of the visibility achieved. By quantifying these metrics, organizations can gain insights into the effectiveness of their asset visibility initiatives and make informed decisions to enhance their cybersecurity posture.
Key Metrics for Evaluating Asset Visibility Programs
Inventory Accuracy:
The importance of maintaining an accurate inventory of all digital assets in a dynamic environment cannot be overstated. This inventory serves as the foundation upon which effective security measures are built. Without a clear understanding of the devices, applications, and data repositories present in the network, organizations are left vulnerable to a myriad of risks, including unauthorized access, data breaches, and compliance violations. Accurate inventory enables organizations to identify and assess areas of potential exploitation, streamline incident response efforts, and ensure regulatory compliance.
Metrics to Measure Inventory Accuracy:
- Percentage of Discovered Assets vs. Total Expected Assets
- Asset Classification Accuracy
Real-time Visibility:
Real-time visibility into assets is imperative for maintaining a proactive cybersecurity posture; organizations need to continuously monitor their digital assets to detect and respond to emerging threats promptly. Real-time visibility enables security teams to identify unauthorized or anomalous activities, detect new devices or applications introduced into the network, and mitigate security risks before they escalate into major incidents.
Metrics to Evaluate Real-time Visibility:
- Frequency of Asset Scans
- Time to Detect New Assets
Coverage and Scope:
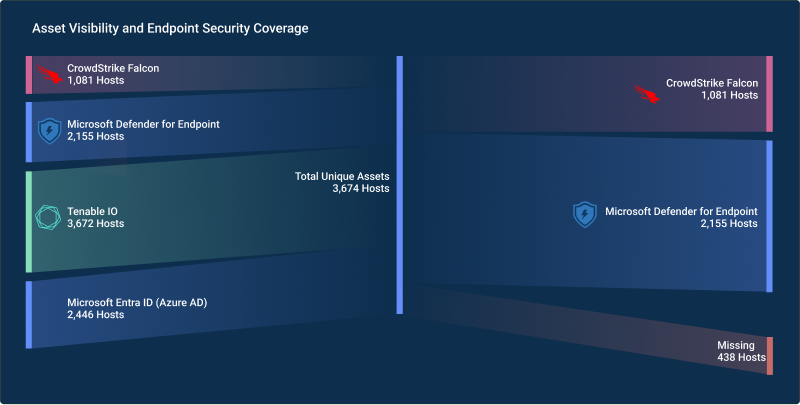
Coverage and scope refer to the extent and granularity of asset information collected within the organization’s network. Comprehensive coverage ensures that all digital assets, including endpoints, servers, cloud instances, and IoT devices, are accounted for and monitored effectively. Depth of coverage pertains to the level of detail captured for each asset, including attributes such as hardware specifications, software versions, and configurations.
Metrics to Assess Coverage and Scope:
- Percentage of Assets Covered
- Depth of Asset Information Collected
Risk Reduction:
Asset visibility plays a crucial role in reducing cybersecurity risks by enabling organizations to identify and prioritize security vulnerabilities, mitigate potential threats, and strengthen their overall security posture. By maintaining a clear and up-to-date inventory of digital assets, organizations can effectively prioritize security efforts, allocate resources more efficiently, and implement targeted security controls to address identified risks.
Metrics to Quantify Risk Reduction:
- Decrease in Vulnerability Exposure
- Mitigation of Critical Asset Risks
Compliance Alignment:
Asset visibility programs play a crucial role in supporting regulatory compliance efforts by providing organizations with the necessary visibility and control over their digital assets. Compliance requirements often mandate the accurate identification, monitoring, and protection of sensitive assets to ensure data privacy and security.
Metrics to Gauge Compliance Alignment:
- Adherence to Regulatory Requirements
- Completeness of Compliance-related Data
Conclusion
In today’s ever-evolving cybersecurity landscape, the importance of asset visibility cannot be overstated. It forms the cornerstone of effective cybersecurity strategies, enabling organizations to identify, assess, and mitigate security risks proactively. By leveraging key metrics for evaluating asset visibility programs, organizations can enhance their ability to detect and respond to emerging threats, protect critical assets, and safeguard sensitive data from cyberattacks. Effective asset visibility is not merely a goal but a continuous journey towards achieving robust cybersecurity defenses. By embracing a proactive approach to measuring success and continuously optimizing asset visibility programs, organizations can stay ahead of evolving threats and ensure the resilience of their cybersecurity posture in the face of growing challenges.

In his role as the CISO, George defines and drives the strategic direction of corporate IT, information security and compliance initiatives for the company, while ensuring adherence and delivery to our massive growth plans. George brings more than 20 years of experience with technology, infrastructure, compliance, and assessment in multiple roles across different business verticals.
You may also be interested in…
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)