The Need for Symbiotic Cybersecurity Strategies | Part I

Since the 1980s, Detect and Respond cybersecurity solutions have evolved in response to emerging cyber threats and technological innovation. These tools progressed from basic intrusion detection to sophisticated, integrated solutions capable of real-time threat detection and response, highlighting continuous cybersecurity innovation.
In our 2024 Cyber Risk Landscape Peer Report survey, 83% of cybersecurity professionals reported experiencing a cyber breach requiring attention despite having traditional threat-based detect and respond security measures in place. That’s a 21% increase over our inaugural survey in 2023 (67%). For organizations in heavily regulated industries such as healthcare and finance, which reported increased breaches in our 2024 survey, these costs can be significantly higher due to fines and compliance requirements.
Financial and Operational Implications of Cyber Breaches
The financial implications of data breaches are significant. The average cost of a data breach reached an all-time high of $4.45 million in 2023, representing a 15% increase over the past three years. Additionally, organizations with fewer than 500 employees reported an average breach impact increase from $2.92 million to $3.31 million, a 13.4% rise. These costs encompass various aspects, such as detection and escalation, which alone increased from $1.44 million in 2022 to $1.58 million in 2023.1
Beyond financial losses, cyber incidents can severely damage customer trust and corporate reputation and lead to substantial fines and regulatory penalties. Given the significant economic and reputational impacts, it’s crucial for organizations to understand and stay ahead of the evolving cyber risk landscape. Proactive risk management, strategic decision-making, and regulatory compliance are essential to a robust cybersecurity strategy. Understanding the current cyber risk landscape enables organizations to adopt measures that effectively mitigate risks, ensuring both operational resilience and regulatory adherence.
Threat detection and response mechanisms are crucial in identifying and mitigating cyber threats before they escalate into significant breaches. These capabilities are vital as the final layer of defense against sophisticated attacks that have bypassed initial preventative measures. When properly implemented, threat detection and response can prevent what might otherwise become a catastrophic compromise.
MDR: The Foundation of Modern Defense
No matter the industry, organizations are plagued with alert fatigue, a lack of visibility due to a complex and changing attack surface, and limited skilled resources. Managed detection and response services were designed to help solve these challenges, but despite investments in these security measures, hidden gaps in cybersecurity programs are hindering the success of overcoming these problems.
It’s not that traditional MDR wasn’t good—it plays a critical role in the modern cybersecurity landscape—it just wasn’t good enough. To have a solid base for high-quality service that provides essential capabilities, including expert analysis, 24x7x365 monitoring, and rapid response times that are both cost-effective and efficient, MDR is crucial but cannot operate in isolation.
The 2024 Cyber Risk Landscape Peer Report highlights the need for a symbiotic relationship between MDR and proactive security elements. This integrated approach involves:
- Regular evaluations to identify and prioritize potential threats.
- Maintaining a comprehensive inventory of all IT assets to detect vulnerabilities.
- Proactively identifying and mitigating vulnerabilities to prevent exploitation.
- Ensuring all endpoints are protected and monitored for suspicious activities.
- Event and threat analysis using cybersecurity frameworks for standardized threat identification and targeted mitigations.
For MDR to function optimally, all assets must be accounted for to close security coverage gaps. Traditional methods such as manual audits, periodic scans, and relying on customers to self-report are insufficient, as they do not provide the real-time, continuous visibility needed to secure today’s dynamic environments. Moreover, organizations often struggle with:
- Siloed Systems: Disconnected and fragmented security tools lead to incomplete data and missed correlations, making it difficult to maintain a unified, accurate view of the IT environment.
- Using Periodic Snapshots to Monitor Dynamic Environments: Relying on periodic assessments in environments where assets are constantly changing leaves blind spots that attackers can exploit.
- Shadow IT: Unapproved or unmanaged systems and applications, which often escape centralized monitoring, increase the risk of vulnerabilities going unnoticed.
To overcome these challenges, a comprehensive asset visibility strategy that provides continuous monitoring and integrates data across all relevant systems is essential. This approach ensures MDR has the complete and accurate information needed to deliver effective, proactive security coverage.
Integrating Proactive Security Intelligence into MDR
Utilizing an MDR platform to integrate proactive cybersecurity intelligence into the Security Operations Center (SOC) — such as comprehensive asset inventories, EDR coverage gaps, asset criticality, and MITRE ATT&CK® Mitigations — can significantly enhance effectiveness and provide a roadmap for organizational security maturity over time.
Asset Visibility is Essential to MDR Effectiveness
Asset visibility involves maintaining an up-to-date inventory of all IT assets, along with determining each asset’s criticality in terms of organization impact in the case of a breach. This level of intelligence is essential for identifying gaps in security orchestration and tooling coverage, and for prioritizing the efforts to harden and secure assets. Asset visibility also ensures that SOC teams or MDR providers are receiving all expected signals so that threat actors cannot slip through gaps in coverage.
In First Steps to Overcoming a Lack of Asset Visibility2, the Center for Internet Security (CIS) reports that “… lack of asset visibility is important to address, as it limits enterprises’ ability to meet their security and operational objectives and increases the likelihood of data breaches and other security incidents.”
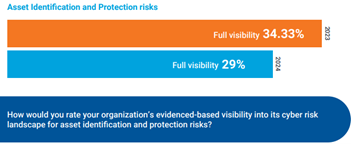
Without an effective asset visibility solution, the teams that work together to keep a business safe (Security, IT, etc.) may lack an understanding of which assets pose risks to the organization. Even with a full asset inventory as provided by CMDBs (configuration management databases), vulnerability scanners, and similar tools, they may not have visibility into critical security gaps, including misconfigurations, improper access controls, a lack of security scanners (tooling), and more. Having the full, accurate account of an organization’s assets provided by a dedicated asset visibility tool is the first critical step in finding and fixing security coverage gaps so that SOC teams and MDR providers reduce the chances of missed security signals. Even though the potential negative consequences of not having comprehensive asset visibility are straightforward, only 29% of our survey respondents report having full visibility.
| Asset Identification and Protection risks | 2023 | 2024 |
| Full visibility | 34.33% | 29.00% |
| Q5: How would you rate your organization’s evidenced-based visibility into its cyber risk landscape for asset identification and protection risks? | ||
The Cross-Functional Benefits of Asset Visibility
Without complete visibility into all assets across the IT estate, security teams can’t validate that all security controls are in place and working as expected. This disconnect between the criticality of endpoints and the lack of total confidence by CISOs and SecOps teams in their security coverage undermines even the best security programs.
However, asset visibility is just one challenge security leaders face as they struggle to align their organization’s risk appetite and cost constraints with comprehensive security protocols.
Overcoming the business and security challenges of the digital era requires a proven, cost-effective, guided, and measurable approach to cyber risk reduction that goes beyond traditional manual, non-evidenced-based, limited-scope assessments and risk management. That’s why Critical Start Critical Start offers an integrated approach beyond traditional MDR solutions to proactively reduce breach risk. Our human-driven MDR includes asset inventory, endpoint coverage gap analysis, and log source monitoring, supporting all IT and OT threat types. Combined with Vulnerability Management and Risk Assessments, this approach ensures enhanced threat and risk awareness and drives prioritized security efforts.
Here, we’ve focused on the importance of asset visibility. In the next installment of this two-part series, we’ll look at how utilizing an MDR platform to integrate proactive cybersecurity intelligence into SOC such as comprehensive asset inventories, EDR coverage gaps, asset criticality, and MITRE ATT&CK® Mitigations — can significantly enhance effectiveness and provide a roadmap for organizational security maturity over time.
Survey respondents have increasingly recognized the value of partnering with an expert vendor for vulnerability management services. Outsourcing not just detection and response but also the management, configuration, and continuous oversight of vulnerability management programs provides several advantages:
- Comprehensive Management: Providers offer end-to-end management of vulnerability programs, ensuring that all aspects, from detection to remediation, are handled efficiently.
- Advanced Configuration: Providers bring expertise in configuring security tools and systems to optimize vulnerability detection and response.
- Resource Allocation: Outsourcing allows organizations to allocate their internal resources more effectively, allowing them to focus on core business activities while leaving complex security tasks to specialists.
- Continuous Improvement: Providers stay updated with the latest threat intelligence and best practices, continuously refining their methods to protect against emerging threats.
Despite having internal vulnerability management programs, the growing complexity of cyber threats and the need for specialized expertise make these providers an invaluable partner. By outsourcing these critical functions, organizations can ensure a robust and proactive approach to cybersecurity, reducing the risk of breaches and enhancing their overall security posture.
Conclusion and Key Takeaways
In this two-part series, we have emphasized the importance of a symbiotic approach to cybersecurity, where Managed Detection and Response (MDR) is bolstered by proactive security measures. Part 1 focused on the significance of asset visibility and its role in ensuring that MDR systems receive accurate and comprehensive threat signals. Part 2 expanded on this foundation, addressing the need to close endpoint and SIEM coverage gaps, integrate event and threat analysis using the MITRE ATT&CK® Framework, and enhance MDR with proactive security intelligence.
Key Takeaways:
- Asset Visibility: A complete and up-to-date inventory of all IT assets is essential for effective threat detection and response.
- Endpoint Coverage: Comprehensive endpoint protection is critical to avoid blind spots in your cybersecurity defenses.
- Proactive Security Intelligence: Integrating proactive measures such as vulnerability management and threat analysis into your MDR strategy can significantly improve your organization’s security posture.
- Continuous Improvement: Regularly assess and refine your cybersecurity strategies to keep pace with evolving threats and ensure ongoing protection.
By adopting these strategies, organizations can build a robust and resilient cybersecurity framework that not only detects and responds to threats but also anticipates and mitigates risks before they can cause significant harm. If you’re ready to stop fearing risk, and start managing it, talk to our experts.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
