Cybercriminals Attack Vectors within the Education Sector

Introduction
As a follow-up to, “The Escalating Threat of Ransomware Attacks in the Education Sector”, this article will dive into the different attack vectors that cybercriminals have used in the education sector. Additionally, mitigation recommendations for the institution, staff, and students will be discussed.
The education sector continues to be one of the most targeted industries as cyber threat actors continue to adapt to new security measures and use more sophisticated targeting practices. In the first six months of 2023, the education industry saw a 179% increase in attack volume in comparison to the same time period in 2022. Many of these cyber-attacks shifted to targeting K-12 organizations where previously threat actors primarily targeted higher education institutions. Often educational institutions do not have the best IT or infrastructure to protect large amounts of proprietary information pertaining to their students, faculty, and staff. Therefore, threat actors have found that targeting the educational sector is a low risk/high reward scheme making it an attractive industry to target.
Education Industry Attack Vectors:
Cyber threat actors have developed a wide range of attack vectors to deploy against educational institutions. These vectors include vulnerability exploitation, phishing campaigns, cryptojacking, malware, and ransomware. Vulnerability exploitation accounted for 29% while phishing campaigns accounted for 30% of cyber-attacks on K-12 schools in 2023. Cryptojacking operations increased by 320 instances year-to-date with the average percentage of customers targeted each month increased from .19% to .55%. While malware delivered to target educational institution increased to 9.4% compared to 8.9% last year. Since February 2023, malware has primarily been received in the form of Microsoft OneNote malicious files. Additionally, ransomware attacks increased by 84% within the first six months of 2023 in comparison to last year.
Common Vulnerabilities and Exposures (CVE)
A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack can run malicious code, install malware, and even steal sensitive data. A known vulnerability exploited within the education industry was PrintNightmare (Windows Print Spooler Remote Code Execution). Vice Society and Mustang Panda, two known threat actors, exploited this vulnerability as part of their efforts of espionage, financial gain, and research theft.
Phishing Campaigns
Phishing is a form of social engineering, including attempts to get sensitive information. Cyber criminals pretend to be an official representative sending you an email or message with a warning related to your account information. The message will often ask for a response by following a link to a fake website or email address where you will provide confidential information. The format of the message will typically appear legitimate using proper logos and names. Any information entered into the fake link goes to the cybercriminal.
Cryptojacking
Cybercriminals gain unauthorized access to educational institutions devices (computers, smartphones, tablets, or even servers) and use these resources to perform crypto mining for cryptocurrency. The use of these devices by cybercriminals increases the resource costs to the schools through electricity and wear and tear of the device for replacements.
Malware
Malware can be hidden behind HTTPs as the secure gateway cannot inspect the encrypted data that is let through. These types of attacks have jumped 2,580% over the same time period in 2022. Additionally malicious files are commonly used to pass malware to unsuspecting victims. OneNote files are the most common type of malicious files that have been observed delivering a wide variety of malware, including AgentTesla, AsyncRat and QakBot. There are vendors that have added detections tools for malware payloads within OneNote files. Additionally, cyber threat actors became aware of the increased security measures when scanning a OneNote file and changed their tactics again to include URLs that trick the victim to download malware payloads.
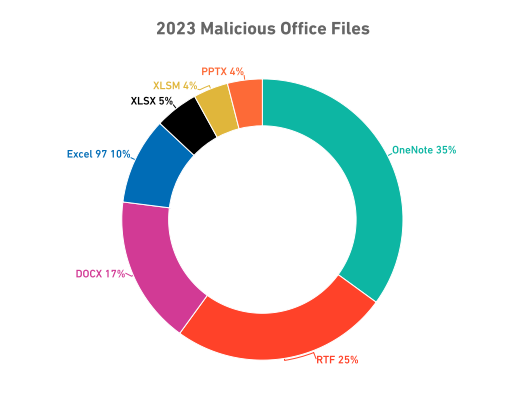
(Source: Sonicwall)
Ransomware
The education sector has become an attractive target for ransomware criminals due to the vast amount of valuable data it stores, including student records, financial information, research data, and intellectual property. As of 2023, 47% of institutions that have suffered from ransomware attacks have paid to retrieve their information. Unfortunately, it is likely that the threat actors maintain a copy to re-ransom the institute at a later date.
Implications for Education Institutions, Staff, and Students:
The implications for institutions, staff, and students can be far reaching. The trust and confidence of students, parents, and patrons in the institution’s ability to safeguard data and provide a secure learning environment can be severely damaged. For staff, the burden of incident response, data recovery efforts, and increased cybersecurity measures can be overwhelming, diverting their focus from core educational activities. Additionally, the psychological and emotional toll on students can be significant, as fear and anxiety over potential data exposure and academic setbacks take a toll on their well-being and academic performance.
How to Mitigate Education Sector Cyber-Attacks:
There are three different variables that impact the success of cyber-attacks on the education sector: institutions, staff, and students. Institutions should oversee resources for cyber security, best practices and hygiene, and provide training for their staff and students. Faculty members or staff should be properly educated and have a solid understanding of how to report cyber incidents to include potential phishing campaigns. Students should be provided with training on the dangers of cyber-attacks within the education sector and how they can mitigate being an avenue for cyber threat actors to use. Below are suggestions on how each variable can help limit exposure to a cyber-attack within the education sector.
Institution:
Limiting, monitoring, and controlling third party access; Only 55% of institutions are noted to have visibility on all the third-party vendors and outside companies that have access to their network. Third party vendor attacks have been on the rise and leaves and organizations vulnerable to attacks. A way to reduce third party vendor attacks is through managing access controls. Access controls act as a virtual checkpoint that stops users from going any further than they need to within a network. Institutions can implement access controls and monitoring via automated technology to save time and resources while reducing the potential for human error.
Education institutions must also have a plan in place to address CVEs to establish a process that prioritizes vulnerabilities identification and remediation of affected assets. Additionally, it is up to the school districts to ensure that their security vendors are offering this capability.
Finally, institutions need to provide cyber training to all faculty, staff, and students. This should include basic cyber awareness training that breaks down how each role can contribute to cybersecurity. As phishing campaigns are largely utilized within the education sector it would be recommended that schools train their staff and students on how to identify phishing emails and malicious files and how to properly report to their cyber security team.
Staff & Students:
Staff, students, and parents of K-12 are responsible for educating themselves on the risks of their individual or child’s information being targeted. Simple ways for staff, students, and parents to safeguard proprietary information include implementing multi-factor authentication and taking cybersecurity awareness training. Additionally, staff and students need to be using appropriate cyber hygiene.
Recommended steps for individuals to avoid phishing emails:
- Check the “from” email address for signs of fraudulence
- Watch for misspellings and incorrect grammar
- Be suspicious of hyperlinks
- Be careful with all attachments — and do not open questionable ones
- Be skeptical of urgency — it’s a common characteristic of phishing
- Protect your personal information
- Consider the time & date
- Trust your gut feeling
Government Funding:
The education sector uses a wide range of systems and networks but does not always have the appropriate funding to support these systems. Currently, the federal government does not provide educational institutions with additional funding to protect their staff and students’ sensitive information. The Federal Communications Commission Chairwoman Jessica Rosenworcel is currently seeking to create the first federal funding stream to help districts fight back against cybercriminals. This federal funding would allot $200 million to schools and libraries across the United States to enhance cybersecurity.
Conclusion:
The education sector uses a wide range of networks that provide easy information sharing and remote access for users, including students, instructors, parents, office staff, and administrators. This can leave the educational institution vulnerable if resources are not properly invested into cyber security. Schools are responsible for protecting personal identifiable information that they receive such as birth records, social security numbers, physical addresses, and even medical information. However, the education sector often lacks appropriate funding from the government to protect staff and students’ information. The protection must be maintained despite limited funds and a lack of cybersecurity awareness among its users, many of whom are students.
As discussed in, “The Escalating Threat of Ransomware Attacks in the Education Sector”, educational institutions must identify security vulnerabilities and evaluate the risks and potential threats to develop cybersecurity strategies. This includes prioritizing cybersecurity measures that enable the investment in advanced threat detection and prevention technologies and conduct regular staff training to fortify its defenses against cyber-attacks. Collaborative efforts between educational institutions, governments, and cybersecurity experts are essential to mitigate the impact of these attacks, secure valuable data, and ensure uninterrupted access to quality education for students and educators alike.
For more updates from our Critical Start Cyber Research Unit (CRU), follow our Intelligence Hub and latest Threat Research.
CRITICALSTART® offers a pioneering solution to modern organizational challenges in aligning cyber protection with risk appetite through its Cyber Operations Risk & Response™ platform, award-winning Managed Detection and Response (MDR) services, and a dedicated human-led risk and security team. By providing continuous monitoring, mitigation, maturity assessments, and comprehensive threat intelligence research, they enable businesses to proactively protect critical assets with measurable ROI. Critical Start’s comprehensive approach allows organizations to achieve the highest level of cyber risk reduction for every dollar invested, aligning with their desired levels of risk tolerance.
References:
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
