LOBSHOT: The Latest Malware Delivered via Google Ads

What is LOBSHOT?
A new malware was recently observed being distributed by malicious Google ads, highlighting the continued use of malicious ads as initial access to a host. Dubbed LOBSHOT, this new malware acts as both an information stealer and remote access trojan and employs numerous techniques to evade detection. One capability that sets LOBSHOT apart is its ability to establish and maintain long-term remote control of targets through a hVNC (Hidden Virtual Network Computing) module.
The Rise of Malicious Google Ads
Cybersecurity researchers have reported a dramatic increase in threat actors utilizing Google ads to distribute malware in search results since the beginning of 2023. Malvertising and search engine optimization (SEO) poisoning redirects users to fake websites to download trojanized installers of popular software. Known campaigns in the past have impersonated such applications as Zoom, 7-ZIP, VideoLAN Client (VLC), Open Broadcaster Software (OBS), Notepad++, CCleaner, TradingView, and Rufus. Previous malware distributed in this way includes Gozi, RedLine, Vidar, Cobalt Strike, SectoRAT, and Royal Ransomware. These tactics may be directed at remote workers trying to download common business software on their home workstations. Due to the success rate, cybercriminals are likely to continue to use malvertising and SEO poisoning as they are proven to be effective initial access points.
LOBSHOT Infection Chain
LOBSHOT’s infection chain starts with a simple Google search for legitimate software. Victims are met with a variety of ads, including some promoted results that are for malicious sites. Clicking on the ad sends the user to a legitimate looking landing page with convincing branding and a download now button. If selected, a Medium Scale Integration (MSI) installer launches PowerShell which downloads a dynamic library link (DLL) file containing LOBSHOT and then executes it with rundll32, before establishing communication with the attacker’s command and control (C2) server.
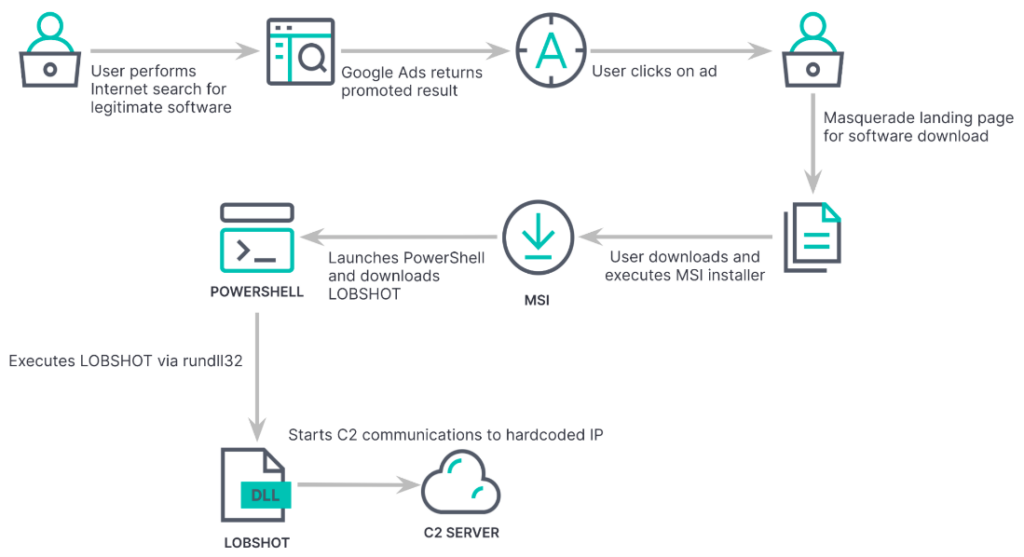
LOBSHOT employs multiple techniques to evade detection which has kept it under the radar until now. Like other malware, it checks if Microsoft Defender is running in the environment and will terminate execution if Defender is present. Dynamic import resolution is also used to evade security products and slow down identification of its capabilities. Additionally, LOBSHOT attempts to break the process tree ancestry by copying itself to the C:\ProgramData folder, spawning a new process using explorer.exe, then terminating the original process and deleting the original file. This makes it more difficult for analysts to identify the malicious activity. One of LOBSHOT’s most notable evasion techniques is its hidden virtual network computing (hVNC) component, which allows direct and unobserved access to the host. This allows attackers to control a hidden desktop, giving them full remote control of the device to include executing commands, stealing data, and deploy follow on payloads.
Conclusion
The rise of malicious Google ads as a distribution method for malware, as demonstrated by the emergence of LOBSHOT, highlights the ongoing threat posed by malvertising and SEO poisoning. LOBSHOT’s sophisticated infection chain and evasion techniques have enabled it to fly under the radar, making it a significant concern for cybersecurity professionals. The hVNC component of LOBSHOT, which grants attackers full remote control over compromised systems, further amplifies its threat level. Given the success and effectiveness of malvertising campaigns, it is expected that cybercriminals will continue to exploit these tactics. As such, organizations and individuals must remain vigilant and implement robust security measures to protect against such threats.
_______________________________________________________________________________________________________________
The Critical Start Cyber Threat Intelligence (CTI) team will continue to monitor the situation and work closely with the Threat Detection Engineering (TDE) team and the SOC to implement any relevant detections. For future updates, the CTI team will post via ZTAP® Bulletins and on the Critical Start Intelligence Hub.
References:
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
