New IcedID Variants Surface in the Wild

The threat actors behind the IcedID (a.k.a. BokBot) banking trojan are making strides to update and improve the malware. Analysis of several recent campaigns show new variants of the malware are shifting away from its original functionality to deliver additional payloads instead, specifically ransomware. Additionally, the creators removed unnecessary functions making IcedID stealthier, and increasing its detection and evasion capabilities. This is the only update IcedID has had since its creation five years ago. This change in tactics mirrors that of the cyber landscape, moving away from banking malware to an increased focus on loaders for follow-on infections.
IcedID Variants
Standard IcedID: This is the most common variant used by several different threat actors and has largely been unchanged since it was originally discovered in 2017. This variant functions as a traditional online banking trojan and consists of an initial loader that contacts a Loader command and control (C2) server. The Loader C2 server then downloads the standard dynamic library link (DLL) Loader. Once the standard DLL Loader is downloaded on the host, it delivers the Standard IcedID Bot.
Lite IcedID: This variant was first observed in November 2022 and has only been dropped by Emotet malware. The Lite variant utilizes a static URL to download a “Bot Pack” file. The file contains the IcedID Lite DLL Loader which delivers the Forked version of IcedID Bot and does not include the webinjects or communication with a C2 server seen in the Standard IcedID variant. This indicates that the Lite IcedID variant does not exfiltrate host data. The exclusive use of Lite IcedID with Emotet malware leads researchers to believe this variant may have been a collaborative effort between the original creators of Emotet and IcedID.
Forked IcedID: Detected in February 2023, this variant appears to be a combination of the other two variants consisting of a Loader C2 server that retrieves the DLL loader and the bot like Standard IcedID. However, the DLL loader that is retrieved is closer in nature to the Lite Loader, loading the Forked IcedID Bot which lacks the banking fraud functionality. This variant has been distributed by two different threat groups acting as initial access brokers. The Forked IcedID campaigns target victims using Microsoft OneNote attachments and attachments with the .URL extension.
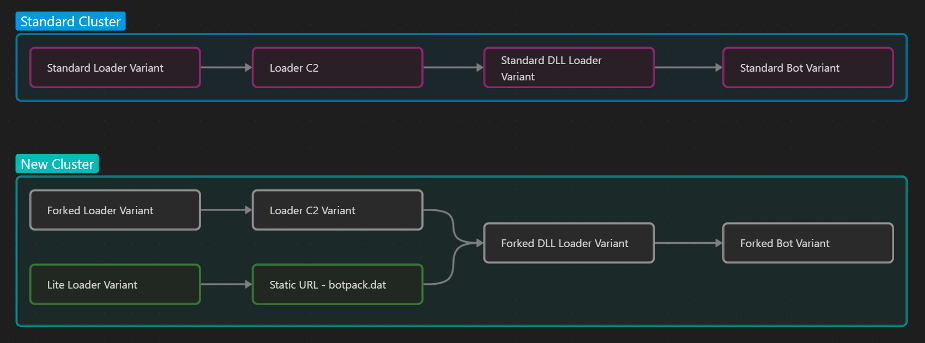
(Overview of three IcedID variants. Source: Proofpoint)
Conclusion
Recently several malware families have created multiple variants to increase their targeting opportunities and prospective for more affiliates using the Malware-as-a-Service model. Additionally, the potential collaboration between the creators of IcedID and Emotet offers a glimpse into the evolving cyber landscape of designing new bespoke variants. Drawing on the experience and expertise of seasoned malware writers enables the development of stealth and customizable malware posing a significant threat to organizations worldwide. This cooperation between threat actors highlights the need to stay vigilant and take proactive measures to safeguard against emerging threats.
The Critical Start Cyber Threat Intelligence (CTI) team will continue to monitor the situation and work closely with the Threat Detection Engineering (TDE) team and the SOC to implement any relevant detections. For future updates, the CTI team will post via ZTAP® Bulletins and on the Critical Start Intelligence Hub.
References:
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
