Protecting your free time – a 3-part plan to get more time away from the office

Time away from the office, sitting on a warm beach, toes in the sand. This is a common fantasy in today’s culture, but maybe time away from the office for you means something totally different. Maybe it’s making your daughter’s play or visiting your grandfather every Friday. Maybe it’s volunteering on a river cleanup initiative or working on that project in the garage. Whatever the purpose, it’s your fantasy so when you do slip away, you need that time to be as free from stress and distraction as possible.
Let’s be honest, it can be tough to slip away when you’re in charge of your organization’s cyber-defenses. You find yourself caught between the need to disconnect and enjoy your time away from the office with your desire to keep tabs on what’s going on. You need a mechanism that’s respectful of your time yet allows you to jump in to aggressively remediate an issue if the situation demands, right?
So, how do you turn fantasy into reality? Perhaps working with the right mix of technology, people and processes is the answer to being “present” without being “present.”
Here’s a three-part plan to make it happen for you:
Technology
Endpoint detection and response (EDR) solutions are extremely valuable because they are used to respond to threats that have already affected the endpoint, and aggregates data from multiple endpoints for forensic investigation.
Conversely, XDR offers security teams a holistic view across networks, cloud workloads, servers, security information and event management, as well as other elements. It also collects and correlates data across multiple endpoints¹ and can traverse numerous security layers to accelerate investigations by providing a complete picture of every threat through improved threat intelligence and artificial intelligence (AI) / machine learning (ML) analysis via a unified platform that provides a single point of reference for security analysts.
In a nutshell, XDR breaks the traditional silos of detection and response. ²
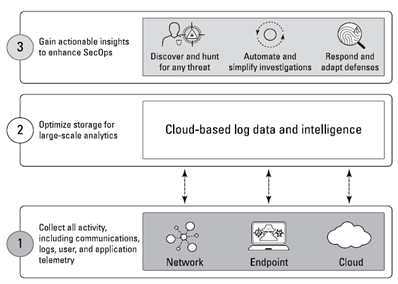
Palo Alto Networks Cortex® XDR™ is one such example of an XDR platform that unifies prevention, detection, investigation and response in one platform for unrivaled security, accelerated investigation and response, simplified security operations, and operational efficiency.
Cortex XDR provides visibility and detection capabilities across your entire environment and possesses the ability to correlate these data sources to understand how various events are linked and when a certain behavior is (or isn’t) suspicious based on context. ² Cortex XDR also helps to secure your users and digital assets by stitching together network, endpoint, and cloud data with AI, behavioral analytics and custom correlation rules to remove blind spots and construct a complete picture of a situation helping security teams make sense of the avalanche of incidents in today’s typical environment.
“XDR provides a far more robust view across networks, cloud workloads, servers and endpoints. One of the limitations that we see with focusing solely on EDR (endpoints) versus XDR (endpoints, cloud, networks, etc.) is that it requires the security team to do the work manually that XDR automates. Many agencies are already using an EDR solution, but it’s important for them to think more broadly about how endpoint security fits into their zero-trust journey,” Drew Epperson, senior director of federal engineering and chief architect at Palo Alto Networks.3
Technology and People: Managed Detection and Response
Managed Detection and Response (MDR) services deliver monitoring and intelligence-based detection capabilities plus the security expertise and technology required to develop comprehensive security infrastructures. MDR services fully enhance the capabilities of an organization’s security team, adapt to shifting threat landscape conditions, and fully execute on threat detection and response activities 24x7x365.
In the case of CRITICALSTART®, our MDR service is all about simplifying your security. While others are focused on finding bad, we focus on finding good. While others prioritize or suppress alerts, we say, bring it on! Bring us every alert because we developed the industry’s only Trusted Behavior Registry™ (TBR) within our Zero-Trust Analytics Platform™ (ZTAP™) purpose-built to resolve all alerts.
We built our MDR service to ingest every alert from supported security tools, like Cortex® XDR™ by Palo Alto Networks, into ZTAP where they are compared against known good behaviors in the TBR and playbooks auto-resolve known good incidents at scale. Incidents not matching the TBR are escalated to our Security Operations Center (SOC) for further enrichment and investigation by Cortex XDR certified analysts 24x7x365. Best of all, Critical Start can take response actions on your behalf and we will work with you until remediation is complete.
Additionally, our Cyber Research Unit stays ahead of the latest threats that your organization may be facing. The unit manages, maintains and curates Cortex XDR out of-the-box detections and Behavioral Indicators of Compromise (BIOCs). We also maintain our own MITRE ATT&CK® based proprietary detections and BIOCs, curate original and third-party threat intelligence to develop new detections and BIOCs and add new intelligence to your security technologies to enhance threat detection.
Technology, People and Process: MOBILESOC
You’re probably thinking, “but wait, there’s a piece still missing — the piece that allows me to take the personal time I need while keeping on top of what’s happening in my security environment.” Well, your wait is over. The final piece that turns fantasy into your reality is MOBILESOC®. The pièce de resistance of our MDR service that puts the power of the ZTAP platform in your hands, giving you the ability to triage, escalate and isolate attacks in-the-moment from your iOS or Android phone regardless of your location or time of day.
MobileSOC fits snugly together with your MDR team and XDR platform and features 100% transparency so you never miss an event. With MobileSOC, you’re able to see the full event data that our analysts see and allows you to directly communicate with SOC security analysts in-app.
MobileSOC = Freedom + Control
Greg Biegan, Director of Security, for Cherwell Software summed up the value his organization’s experience through MobileSOC this way: “It has been worth its weight in gold. Since we are a global company, my team is getting pinged at all hours of the night. And it’s nice; those that are on-call can actually have their phone. They don’t have to be tied to their computer. They can communicate with the consultant that’s there, they can look at what’s going on, they can determine the action, and it’s just like texting. And once it’s done, it’s done.” Biegan says the best part is that his team does not get pinged more than is necessary. “It’s nice to know that you have that extra safeguard, that extra layer of security with that MobileSOC.”
To learn more about Critical Start and MobileSOC, contact us today.
Additional Resources:
Are you considering a Managed Detection and Response Service as part of your overall security program? Learn how to deploy an MDR service to protect your business in the Guide to Managed Detection and Response.
¹ https://www.paloaltonetworks.com/blog/2021/10/edr-requirements-xdr/
² https://www.paloaltonetworks.com/resources/guides/xdr-for-dummies
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
