Establishing Provable Security Maturity with Managed Cyber Risk Reduction
A groundbreaking approach for cybersecurity professionals to demonstrate how they’re effectively addressing organizational cyber risk.
Are we doing the right things? Is what we’re doing working?
These are fundamental questions in cybersecurity. Company leadership asks security teams to prove their approach works, and to back budget requests with data, but they lack concise data to articulate their strengths and weaknesses.
In speaking with customers and prospects, we learned that few are confident in their existing security approach. As we reported in the Critical Start 2023 Cyber Risk Confidence Index, 66% of cyber leaders say they are not very confident in the effectiveness of their current strategies for evaluating and mitigating major cyber risks. What they need and want is to move past reactive, threat-based detection and response efforts, but no third-party vendor could meet that need.
Until now.
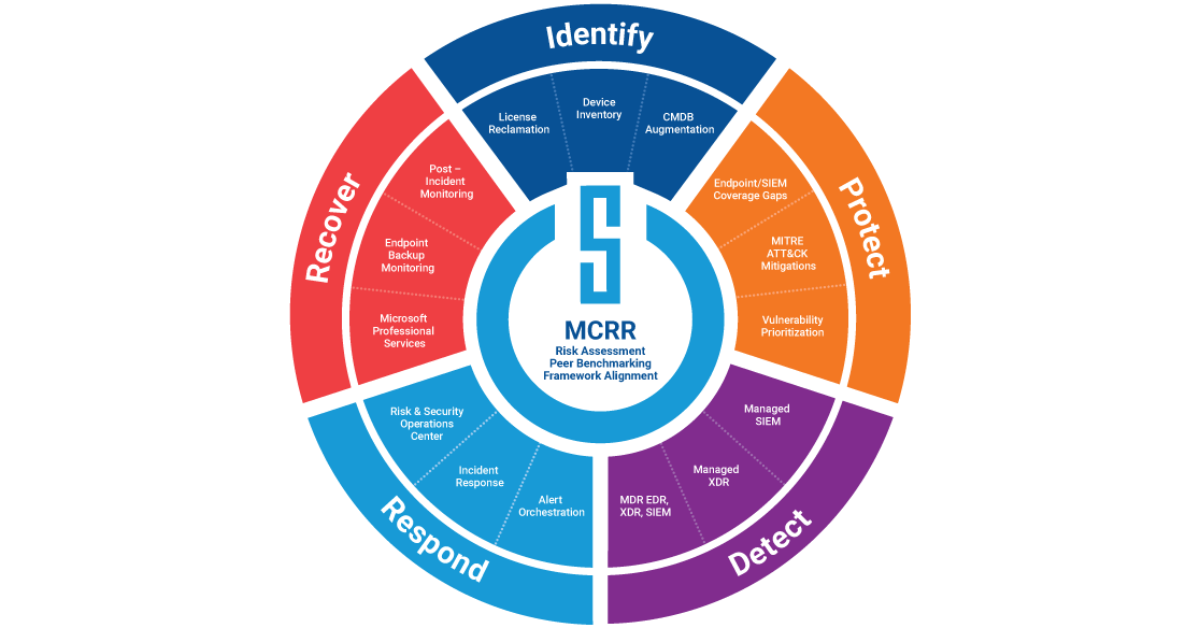
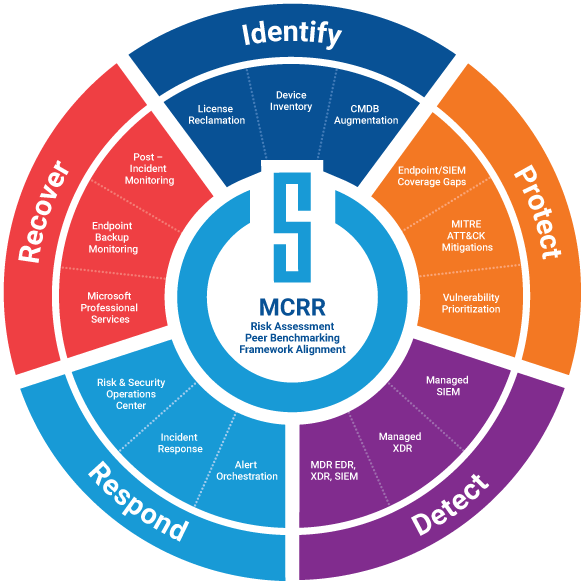
Critical Start Managed Cyber Risk Reduction (MCRR), the next evolution of MDR, is a portfolio of products, managed services, and professional services that address risks, vulnerabilities, and threats, expressly designed to go beyond threat-based detection and response to support organizational security programs across all five functions of the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF): Identify, Protect, Detect, Respond, and Recover.
MCRR’s development was driven by customer needs, so we’d like to share the thinking that went into this first-of-its-kind approach. This is the first in a series of articles, and in the coming weeks, we’ll dive deep into MCRR and how it addresses the cyber risk challenges facing organizations.
We’ll show how other services fall short of addressing the challenges security leaders face and demonstrate how MCRR ties risk analysis to actions that demonstrate measurable improvement.
To get started, let’s look at what MCRR is, why it’s important, and how provable security maturity can become a reality for your organization.
Identifying, Measuring, and Acting on Cyber Risk – What’s the Problem?
For security leaders, the pressure to demonstrate effective cyber risk management, align cyber protection measures to a company’s risk appetite, and do more with less never ends. There’s external pressure, too, including the U.S. Securities and Exchange Commission’s (SEC) new requirement that publicly traded companies file a Form 8-K report within four business days of a cybersecurity incident. With potential consequences going beyond brand damage and lost business to charges against a company’s senior executives, the stakes for securing data and mitigating breaches are higher than ever.
Unfortunately, identifying, measuring, and acting on cyber risk is hampered by the:
- Lack of a consolidated cyber risk view with peer benchmarking
- Challenge of obtaining a risk-ranked list of actions, prioritized by greatest potential impact
- Inability to produce trusted cyber risk reports
- Absence of company-wide visibility into activities of IT, DevOps, and other teams
- Wide-ranging and evolving risks that demand attention from security teams
- Under-resourced Security Operations Center (SOC)
Fortunately, MCRR mitigates these roadblocks by providing security coverage across the five NIST Cybersecurity Framework functions. This alignment lets your organization:
- Gauge organizational security maturity in comparison to your industry peers.
- Understand which of your security investments provide the largest risk reduction impact.
- Confidently demonstrate measurable security improvements over time.
- Uncover gaps in EDR, SIEM, and XDR controls coverage, ensuring the SOC receives expected signals.
- Understand which assets require protection.
- Engage our expert risk and security and operations team 24x7x365.
Armed with the data and resources provided by MCRR, you can finally enable orchestrated, well-informed, and cost-effective, risk-aware protection to identify, protect, detect, respond, and recover faster, and with greater confidence.
Provable Security Maturity – Generating a Continuous Cycle of Risk-Aware, Data-Driven Improvement
If those tasked with protecting an organization aren’t confident in the security measures in place, how can they instill confidence in stakeholders?
They can’t. Unless they tap into Critical Start Risk Assessments.
Critical Start’s Risk Assessments are user-friendly tools for assessing cybersecurity status, no matter your organization’s current cyber maturity level. With two types of assessments available, you can opt for a free Quick Start to gain a high-level understanding of your risk profile, or you can dive deep, with a comprehensive, framework-aligned risk assessment. The platform offers assessment comparison, reporting, tracking, risk rankings, and effective mitigation techniques. Your existing assessments can be imported into the platform, streamlining the transition from manual or disparate processes and allowing you to build on past efforts in a standardized and automated way.
The Cyber Risk-Ranked Reduction Recommendations delivered via Critical Start Risk Assessments help you:
- Use risk assessments as the baseline for cyber health and constantly move the needle toward security maturity.
- Create a risk-informed roadmap with stack-ranked recommendations for improvements.
- Draw on real-time and historical insights to illustrate security maturity advancements over time.
- Know where your organization ranks in cyber risk management vs. industry peers.
- Create detailed reports that demonstrate the value of security investments and justify budget requests.
Want more detail about building provable security maturity with Critical Start Risk Assessments? Download this datasheet.
We’re Just Getting Started
Our primary goal with MCRR is to give you the tools you need to advance your security program over time with a strategic, risk-based approach to mitigate risks — in the most cost-effective ways possible. In this piece we covered a bit of the thinking that went into developing this one-of-a-kind offering, but in the coming weeks we’ll be digging deeper into how MCRR both reduces complexity and increases your control over your environment, so be sure to check back.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
