Read-the-Manual Locker Upgraded for Linux Architecture

RTM Locker Summary
Read-the-Manual (RTM) Locker is a private ransomware-as-a-service (RaaS) provider that is now capable of targeting Linux machines. The locker malware developed to infect Linux was designed to single out Elastic Sky X integrated (ESXi) hosts to prevent the RaaS being executed on virtual machines running on a compromised host prior to commencing the encryption process. The goal of the RaaS is to extract as many files as possible from the compromised machine and store them on the RTM Locker gang servers to enable double extortion tactics. The code is statically compiled and stripped, making reverse engineering more difficult and allowing the binary to run on more systems. Additionally, the encryption function also uses pthreads, which allows the execution to be sped up. Once encryption and exportation of the files has been achieved, a ransom note is left on the victim’s machine urging victims to contact the support team within 48 hours via Tox. If the victim does not reach out within 48 hours, the RTM Locker gang will begin to publish sensitive data to coerce the comprised organization to pay the ransom.
Background of RTM Locker
RTM Locker RaaS is also tied to a cybercrime group called RTM Locker that has been active since at least 2015. The gang operates like a legitimate business, requiring affiliates to remain active or notify the gang of their leave. Additionally, there are strict rules for any affiliates using the RTM Locker RaaS to ensure that operations remain under the radar. The group deliberately avoids high-profile targets, such as critical infrastructure, law enforcement, and hospitals to ensure attention to the threat actors remains low. Furthermore, the group requires affiliates to update targeted organizations with gained information on their darknet panel allowing the RTM Locker gang to extort their victims twice. If victims refuse to pay the ransom the gang has been known to use double extortion, leaking the stolen data on public domains.
RTM Locker Attack Pattern
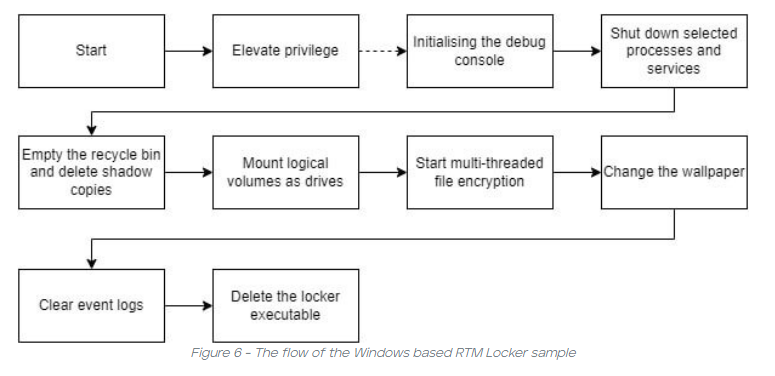
It is currently unknown how the RTM Locker gains initial access. Once the threat actor gains access to the device, the RTM Locker ransomware launches itself to check if it has administrative permissions on the built-in system domain. A dialog box requesting User Account Control will proceed to pop up if additional permissions are required. If the victim approves the execution, the new process instance is launched with the requested administrative permissions. However, if the victim denies the request, the Locker continuously requests it until the permissions are granted. The command-line argument then checks for a debug argument allowing the Locker to print debug data. At this point, the Locker looks to terminate any process that might hinder or block the malicious file from being executed. Additionally, the Locker will empty the recycle bin and delete shadow copies before the encryption process of the files begins. This reduces the amount of time the ransomware runs by decreasing the number of files being encrypted and stored on the threat actors’ servers. The malware will continue to run in the background on a sleep loop until all drives in the command line have been downloaded and encrypted. Upon completion, the wallpaper on the machine will change and the ransom note will be placed on the desktop. Lastly the ransomware clears the event logs wiping the system, application, and security logs from the machine before the Locker self-shuts down.
RTM Locker Targets
Linux Endpoint OS and Windows Endpoint OS
Conclusion
While RTM Locker ransomware can be truly devasting for an organization, the risk is slightly reduced due to the need for administrative privileges. Corporations are encouraged to limit administrative privileges to a select few within their network. Initial access for threat actors to try to gain access to these credentials could be achieved through multiple means to include phishing attacks, malicious spam, vulnerable publicly exposed systems, or even purchased on the black market. Organizations should remain vigilant and take appropriate steps to protect themselves from these types of threats, including implementing strong cybersecurity measures, investing in employee training and awareness, and regularly updating their security protocols.
The Critical Start Cyber Threat Intelligence (CTI) team will continue to monitor the situation and work closely with the Threat Detection Engineering (TDE) team and the SOC to implement any relevant detections. For future updates, the CTI team will post via ZTAP® Bulletins and on the Critical Start Intelligence Hub.
References:
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
