The Security Metrics that Matter and Why

According to CIO.com, 58% of organizations aren’t adequately measuring the effectiveness of their cybersecurity program. That number is even more shocking when you consider how the average global cost of a data breach reached $4.35 million in 2022. In the United States, that number was $9.44 million alone. (IBM.com)
Without the proper visibility into how well your program is performing, it can become even more difficult to identify potential gaps in security coverage, or empower your workforce based on individual and team performance. This can not only lead to the inability to efficiently measure your cybersecurity program, but dollars lost as well.
Beyond monitoring your cybersecurity program performance, it’s also essential to be able to communicate how your organization is being protected with non-technical people. There are many metrics out there, but drilling down to the metrics that matter, help tell a story, and that can be tied directly to business performance and outcomes is key. So, where do you start?
Managed Detection and Response (MDR) Providers: Going Beyond Protection
One could argue that as the stakes get higher, the data needed to support mitigation efforts becomes more significant and is no longer an afterthought. Cybersecurity leaders are tasked with showing metrics that matter and how those metrics impact the business, but are met with many challenges, such as:
- A lack of data to inform resource management
- Insufficient data to understand team performance
- Not enough operational metrics to identify risk and measure improvement
- Pressure to reduce time to detect and response
- Communicating value of cybersecurity with non-technical people
A Managed Detection and Response (MDR) provider should go above and beyond detection and response services, providing you with security metrics that matter to monitor performance and help secure cybersecurity spend. A robust provider with 24x7x365 coverage and availability will also give customers increased, real-time visibility across the entire security program, with metrics that can show bottom-line business impact.
You know you need certain metrics to better tell your story and justify your spending, but how do you narrow in on what’s important?
The Security Metrics that Matter Most
Critical Start’s Zero Trust Analytics Platform™ (ZTAP®) has robust navigation and value-add dashboards that enhance user experience and deliver the security operations metrics you need to continuously improve your security program and report on its success. This means that you can spend less time on manual reporting, and more time communicating your program’s value.
When determining and communicating the value and performance of your program, tune into these metrics:
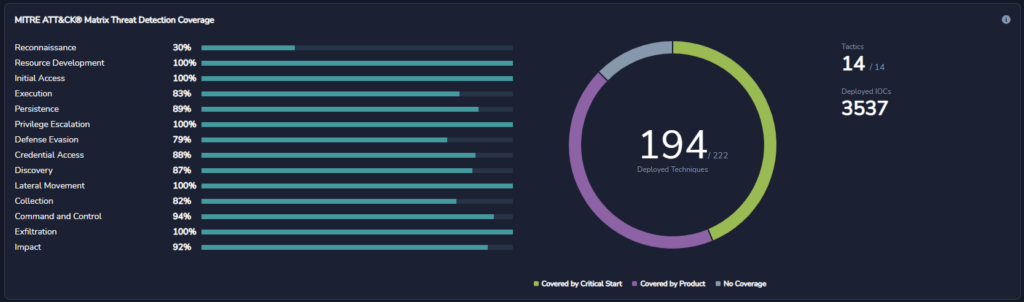
- Visibility of Security Coverage: Do you have visibility into how well your security tools are covering against the latest TTPs (tactics, techniques, and procedures)? And are your tools mapped back to a security framework like the MITRE ATT&CK® Framework?
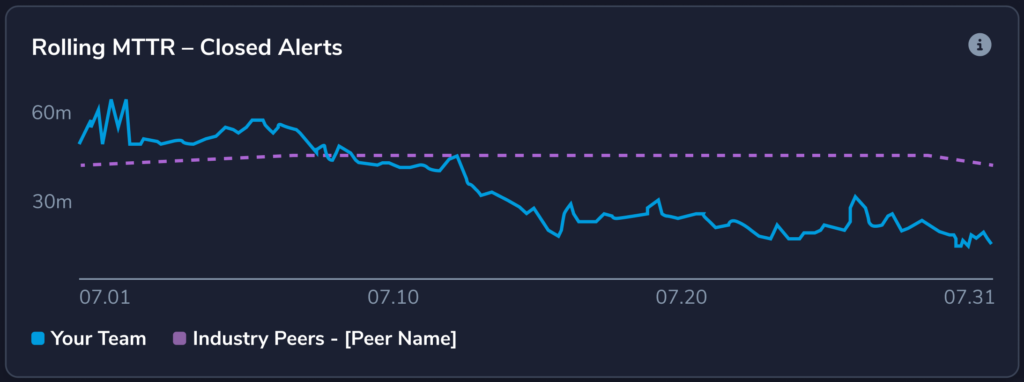
- Productivity and Staff Performance: Establishing analyst benchmarks internally and against industry peers to improve staff resource management and workload constraints is key to a productive program. Metrics around performance can let you quickly see:
- Do I need to hire additional resources to work on more important investigations?
- Do I need to spread out the workload amongst more people on the team?
- How am I benchmarking against industry peers?
- Do we need to leverage our MDR provider more extensively, like allowing them to take more response actions or use their mobile app to help mitigate the need to add more staff?
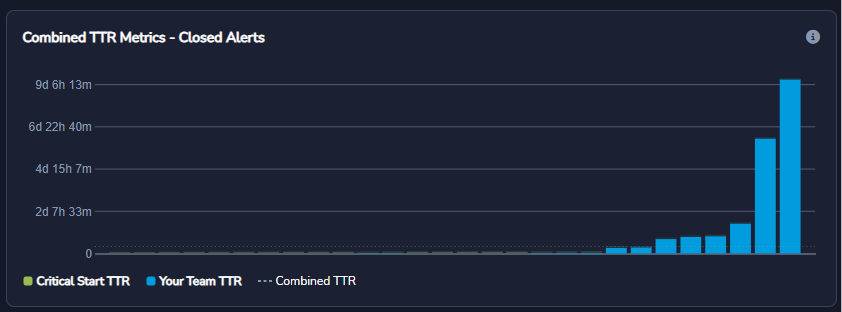
- Time to Detect and Respond: It’s essential to work with cybersecurity tools that provide a real-time actionable view of attacks in progress across your security environment with clear, step-by-step response guidance, including prioritized response based on asset criticality and where attacks are at in the kill chain.
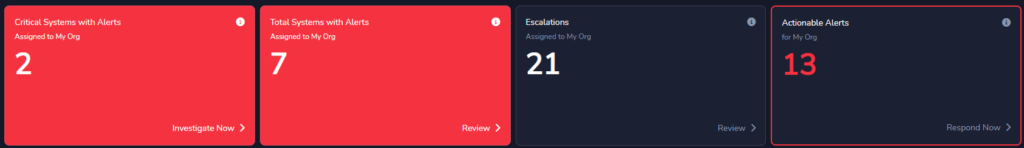
- Identifying Risk for Risk-based Decision Making: Do your tools enable risk-based decision-making and improve attack coverage effectiveness? Leaning into a cybersecurity platform that lets you classify alerts strategically and recognize exposures proactively lets you make risk-based decisions on attack coverage with real-time data you can trust.
- Security Spending: Cybersecurity leaders look to quantify their security spending while aligning budget. Do your tools have data and reporting that help you articulate the value of your program so you can align cybersecurity investments with business outcomes?
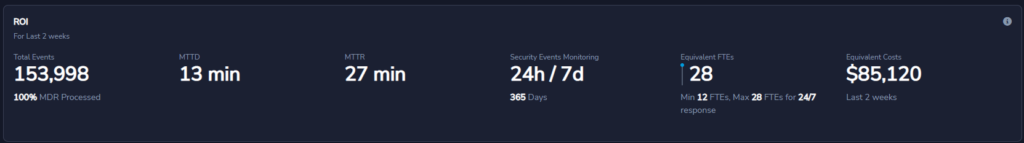
Once you have determined the metrics that matter and the processes and reporting you will need to have in place to measure them, you’re on your way to better determining the success of your cybersecurity program. From there, demonstrating a return on investment and communicating that value to your board becomes even simpler – if you have the right tools and dashboard in place.
At Critical Start, metrics are not just viewed as “We do our part, now you do your part.” We use metrics to show how we are performing as your MDR provider, and how your team is performing as well, so we can help improve our overall performance together.
For example, our data (over a six-month period) shows that 50%-60% of alerts come in after business hours, or during the off-hours of a business from 6:00 PM and 8:00 AM. This means that when you’re at your kid’s baseball game or trying to binge-watch your favorite show, you know that you’re covered, and any interruption has been scrutinized first by our expert SOC team.
We’d love to tell you more. Contact an expert today to learn about our services that show real-time metrics that focus on continuous improvement. To read more about how to evaluate your cybersecurity program, how well it’s protecting your organization, and how to use that information to secure your budget, check out our new Cybersecurity Leader’s Guide for Measuring Security Performance.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
