The Next Evolution in Cybersecurity

“Those who cannot remember the past are condemned to repeat it.”
-George Santayana, Spanish-American Philosopher
George Santayana’s ominous warning of cyclical focus is seldom considered in forethought. With few exceptions, the theory holds true across all things, including cybersecurity. From the early inception of cybersecurity, groundbreaking innovations have often cycled between detection (reactive) and prevention (proactive) in focus.
Here is a quick look at the evolution in the industry throughout the years, from Antivirus through Managed Detection and Response.
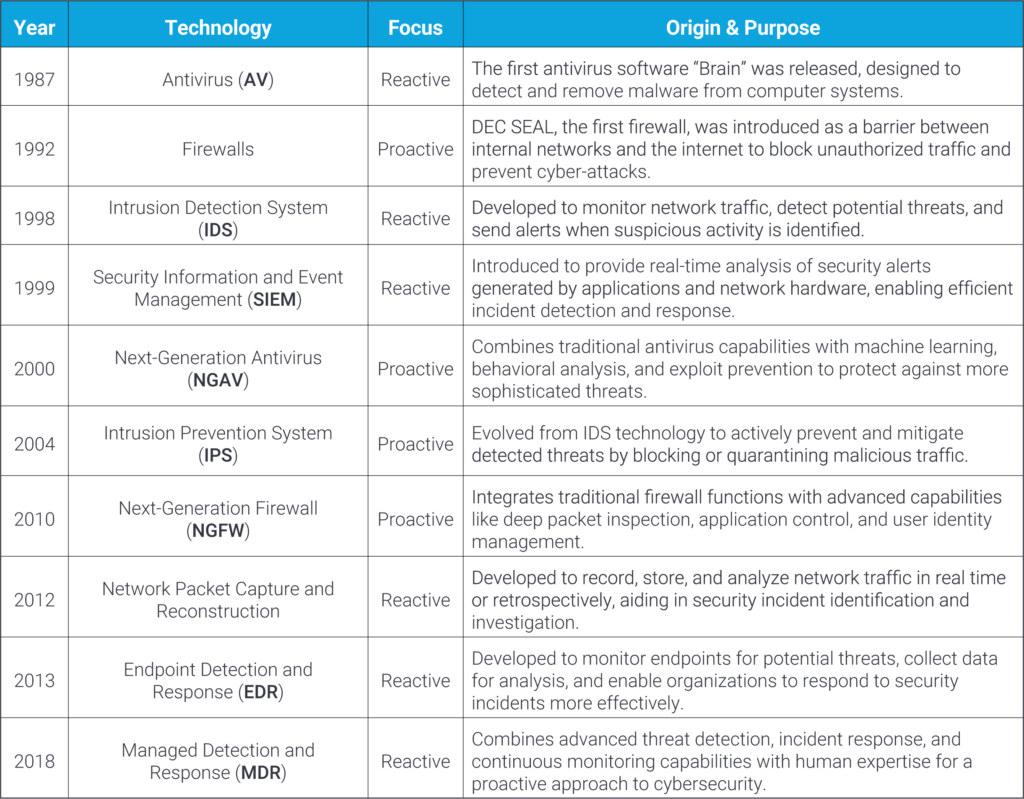
The Cybersecurity Evolution
While many arguments can be made for the reasons behind this continuous shift, I attribute it to three primary factors:
- Under-Resourced Cybersecurity Teams: With a shortage in both headcount and expertise exacerbating a security function that lags innovation in networking and infrastructure, security teams often shift focus based on the priorities of the business and the allocated resources.
- Technology Advancements and Vendor Competition: The integration of technology advancements, machine learning, and AI has empowered cybersecurity vendors to develop more sophisticated detection and protection solutions. Market demands for improved return on investment (ROI) for security purchases, coupled with rising regulatory requirements, have driven vendors to continuously innovate and compete to maintain their market share.
- Cybercriminal Innovation:
The result is a high-cost, high-stakes game of whack-a-mole detecting new TTPs, then putting preventative controls in place while the attacker develops newer TTPs less likely to be detected. From the business’ perspective, this lag, providing a window of opportunity to attackers, represents risk.
The primary concern among security professionals is a breach that disrupts their business operations. To manage cyber risk and reduce the likelihood of such a breach, organizations often utilize frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). The NIST CSF was originally released in 2014, with the latest release in 2018, and has become widely adopted across organizations as a tool for managing cyber risk, and buckets capabilities across five pillars: Identify, Protect, Detect, Respond, and Recover. By improving their NIST CSF maturity, organizations mitigate cybersecurity risks, which correlates with a decreased probability of experiencing a disruptive breach. Organizations have been overwhelmed by the proliferation of Ransomware-as-a-Service, cyberattack automation platforms, and the attacker’s ability to monetize both attacks and exploits with cryptocurrency. Coming in the throes of a detection trend, initial focus was applied to the detection and response categories of rapidly advancing TTPs.
How MDRs Help Manage Risk and Prove ROI
However, Critical Start has found that 67% of organizations have experienced a cyber incident despite having traditional threat-based security measures in place.
To recognize the ROI of their security investments and mitigate risk, many organizations have turned to MDR providers. Itself an evolution from compliance focused MSSPs, MDRs add the value of expertise and action to a subset of telemetry and products to reactively contain threats and lower attacker dwell time. The turnkey ROI and security maturity aligned to the “Detection” and “Response” NIST CSF categories created by MDR gives organizations the greatest reduction in reactive risk per dollar spent, given the right MDR provider.
Feeling some relief from outsourcing 24×7 investigation and response, many organizations are looking to further reduce cybersecurity risk by shifting focus back to proactive security controls of the “Identification” and “Protection” NIST CSF categories that make them less susceptible to intrusions, hopefully countered by MDR. Posture or exposure management has become a prominent topic over the last few years as an amalgamation of new and legacy controls from vulnerability management to attack surface monitoring. Though the mission of increasing cyber-resiliency is noble, the continued headcount and expertise shortage could relegate this to next lagging undulation in security trends as most security teams stretch to retain the talent to implement and operationalize the portfolio of posture-focused controls.
What’s the Next Step?
With the success of staff-augmentation applied to “Detection” and “Response” by MDR, there’s an opportunity to apply this logic to posture management controls aligned to the “Identification” and “Protection” pillars of NIST CSF, once again creating a more turnkey path to maturity and risk reduction for over-burdened and under-resourced security teams. This complete alignment to NIST CSF provides measurable progress in security maturity and risk reduction that can be communicated to organizational leadership.
This blog is partially an excerpt from an upcoming whitepaper co-authored by Jennifer Haney-Crowe, Critical Start Senior Director of Product Marketing, and me, slated for release on August 9th, 2023. Follow our blog and LinkedIn for some exciting developments, and the new whitepaper, coming soon!

CTO
As the Chief Technology Officer and an emerging thought-leader in the security industry, Randy is responsible for designing and executing the company’s strategic technology initiatives, which includes defining the strategy and direction of CRITICALSTART’s Managed Detection and Response (MDR) services delivered by the Zero-Trust Analytics Platform® (ZTAP). Previously, Randy served as the Director of Security Architecture, where he set the strategy for emerging vendor technologies, created the Defendable Network reference architecture, and set product direction for the company’s internally-developed Security Orchestration Automation and Response platform.
You may also be interested in…
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)