The Ongoing Impact of Malware-as-a-Service

Critical Start CRU predicts the sophistication of Malware-as-a-Service (MaaS) is expected to rise due to the demand for more powerful attack tools, posing challenges for cybersecurity professionals and requiring advancements in defense strategies. These MaaS offerings will introduce new and adaptive attack vectors, such as advanced phishing schemes and polymorphic malware that continually evolves to evade detection.
The Ongoing Impact of Malware-as-a-Service
Malware-as-a-Service (MaaS) represents a sophisticated cybercriminal business model that revolutionizes the landscape of cyber threats. In this paradigm, individuals or groups can easily access and utilize advanced malware tools by either renting or purchasing them. The profound impact of MaaS is evident in the shifting dynamics of cyber threats, particularly in enabling less technically proficient actors to engage in malicious activities.
This approach has contributed to a noticeable surge in cyber-attacks, as it lowers the barrier of entry for individuals lacking extensive technical expertise. MaaS has, over time, evolved into a pervasive force within the cybercrime ecosystem. By democratizing access to highly sophisticated malware, it allows a broader range of threat actors to participate in malicious activities, posing a considerable challenge to cybersecurity measures.
The repercussions of MaaS are far-reaching, affecting individuals, businesses, and governments alike. Individuals may find themselves at an increased risk of falling victim to various cyber threats, ranging from personal data breaches to financial losses. For businesses, the threat extends beyond traditional security challenges, with potential assaults on operations, intellectual property, and customer trust. Even governments face challenges in addressing the national security implications as cybercriminals equipped with advanced malware can operate beyond geopolitical borders.
To effectively navigate this evolving threat landscape, it is imperative to comprehend the associated risks of MaaS. Cybersecurity strategies must evolve to counter the democratization of sophisticated malware tools. Implementing robust mitigation strategies, staying informed about emerging threats, and fostering a proactive cybersecurity stance are crucial components in the ongoing battle against the pervasive influence of MaaS.
Proliferation of MaaS Varieties
The proliferation of Malware-as-a-Service (MaaS) varieties represents a significant trend in the cybercriminal landscape, contributing to the diversification and accessibility of malicious tools for a wide range of threat actors. This expansion has given rise to an array of MaaS offerings, each tailored to specific capabilities and objectives, further complicating the cybersecurity landscape.
One key facet of this proliferation is the diversification of malware types accessible through MaaS platforms. Threat actors can now choose from an assortment of malicious tools, spanning ransomware, banking trojans, spyware, and specialized utilities, providing them with a versatile menu of options to align with their specific goals. This array of choices not only caters to the diverse objectives of cybercriminals but also amplifies the adaptability and scalability of their malicious activities.
Recent research reveals an unsettling reality: QakBot (QBot), SocGholish, and Raspberry Robin, three adaptable malware loaders, have collectively driven a staggering 80% of cyberattacks in the initial seven months of 2023. These loaders demonstrate remarkable versatility, enabling a wide range of malicious activities, including ransomware, viruses, trojans, and worms.
Top 3 Malware Loader
- QakBot: QakBot operators have displayed remarkable agility by frequently changing their delivery tactics. This adaptability allows attackers to target various industries and regions with ease. In recent developments, QakBot operators expanded their command-and-control (C2) network by adding 15 new servers, the majority of which were used to communicate with victim hosts and download additional malicious payloads. These payloads include Cobalt Strike and remote access tools like Atera and NetSupport.
- SocGholish: During the first half of 2023, SocGholish operators engaged in watering hole attacks, compromising the websites of prominent organizations engaged in everyday business activities. Unsuspecting users were lured into downloading malicious payloads through social engineering tactics.
- Raspberry Robin: Raspberry Robin has been a vector for delivering various ransomware strains, including Cl0p, LockBit, TrueBot, and Flawed Grace, along with Cobalt Strike. In the first half of the year, operators targeted a broad spectrum of sectors, including financial institutions, telecommunications, government entities, and manufacturing organizations, with a significant focus on Europe and some presence in the U.S. Notably, researchers also discovered instances of SocGholish operators collaborating with Raspberry Robin in the first quarter of 2023, targeting legal and financial services, indicating increased cooperation among cybercriminal syndicates and malware operators.
Top 3 malware
- Redline: A formidable data-stealing malware, Redline first surfaced in 2020 and has maintained its status as a persistent menace to Windows systems. What sets Redline apart is its ability to provide attackers with complete control over compromised computers. In Q2 2023, its usage witnessed a staggering 80% surge compared to the previous quarter, establishing it as the most widespread cyber threat globally. Attackers who deploy Redline gain unfettered access to sensitive data, including passwords, banking credentials, and even cryptocurrency holdings. This malicious software poses a substantial risk to organizations, both in terms of financial losses and damage to their reputation.
- Remcos: A Remote Access Trojan (RAT) active since 2016, Remcos is notorious for its data theft capabilities. Although there was a slight 1.2% drop in the number of Remcos samples submitted to ANY.RUN in Q2 compared to Q1, it retained its position as the second most common malware. Remcos can be delivered through various vectors, such as .exe or .docx files. Once it infiltrates a victim’s computer, it engages in various malicious activities, including stealing private information, modifying the system’s registry, and closely monitoring user activities. Organizations should remain vigilant because Remcos continues to be a persistent threat.
- njRAT: A Remote Access Trojan with a notorious history, njRAT has been active since 2013. It boasts a dedicated community of enthusiasts who have contributed to a wealth of educational content on its usage. njRAT equips attackers with a diverse arsenal of hacking tools, enabling activities such as keylogging, extracting passwords from web browsers, and capturing webcam images. In Q2 2023, njRAT witnessed a 4.2% increase in its usage, earning it the distinction of being the third most popular malware worldwide. Attackers frequently employ phishing emails as a means of distribution, disguising njRAT within fake attachments that appear legitimate. This malware’s prevalence underscores the need for organizations to remain proactive in defending against evolving cyber threats.
Lowering Entry Barriers
The democratization of cybercrime has further underscored the emergence of specialized service providers within the MaaS domain. Providers are concentrating on specific niches, such as offering ransomware-as-a-service, providing training modules, or supplying tools for executing phishing campaigns and stealing sensitive information. The specialization observed in these service providers allows threat actors to select offerings that align with their skill sets and objectives, facilitating a more accessible and customized approach to engaging in illicit activities.
Additionally, the proliferation of MaaS varieties extends beyond mere accessibility, reaching the realms of sophistication and customization. Some MaaS platforms prioritize user-friendly interfaces and offer customer support, making it feasible for individuals with limited technical expertise to participate in cyber-attacks. Concurrently, advanced, and tailored services are available for seasoned cybercriminals, enabling them to execute highly targeted and intricate operations with precision.
Real-World Examples:
- Classicam, a phishing platform, assists over 1000 attack groups globally offering a template-based service, allowing attackers to create brand impersonated webpages with localization support for global expansion. A total of 251 unique brands were impersonated in the last two years across 79 countries. The platform has been utilized by over 38,000 cybercrime groups, generating an estimated $64.5 million for Classicam from 2020 to the present.
- AlphaLock, a Russian hacking group, operates as a “pentesting training organization,” providing hacker training and monetizing their services through a dedicated affiliate program.
- ShadowSyndicate an initial access broker that obtains initial access to victims themselves and then sells that access to other cybercrime groups.
- The Krypton network is reportedly offering DDoS-for-hire services and has been involved in targeting Israeli organizations.
- Appin is known for providing offensive security training while engaging in covert hacking operations.
The trend of MaaS will continue to lower the entry barriers for individuals seeking to engage in cybercriminal activities. As the tools become more user-friendly, the number of novice cybercriminals are highly likely to rise, leading to a broader array of attacks.
Escalating Sophistication
The sophistication of MaaS introduces diverse risks across multiple dimensions. It enables a broader range of threat actors to engage in malicious activities, leading to an increase in the frequency and complexity of cyber-attacks. Moreover, the customization and specialization offered by MaaS platforms allow for targeted and adaptable threats, challenging traditional defense mechanisms.
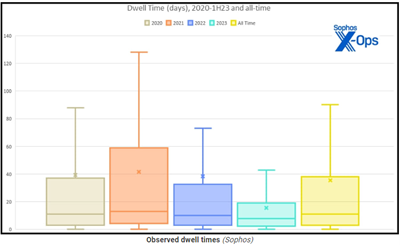
Dwell Time
The latest data and research findings underscore substantial shifts in dwell times – the duration between an initial network breach and its discovery – within compromised networks. This alarming trend emphasizes the critical importance of gaining a deep understanding of these evolving dynamics to effectively combat the growing menace of cyber threats.
In the first half of 2023, there has been a remarkable reduction in the median dwell time for ransomware attacks, from nine days in 2022 to just five days. This metric signifies how long threat actors remain hidden within compromised networks and underscores the agility of ransomware operators in their pursuit of illicit gains.
New Ransomware TTPs
Groundbreaking extortion methods utilized by ransomware gangs have come to light. The FBI has issued a warning about ransomware gangs adopting new tactics, including employing multiple ransomware strains in a single attack, `and using destructive tools beyond encryption or theft. These tactics involve custom data theft, wiper tools, and malware to pressure victims into negotiation. Additionally, the FBI has issued a warning regarding the emergence of dual ransomware attacks, where separate ransomware attacks are conducted within hours or days of each other against the same victim. These attacks typically occur within a 10-day timeframe, with the majority happening within 48 hours of each other.
Furthermore, some ransomware groups are combining two ransomware strains during these attacks, such as AvosLocker, Diamond, Hive, Karakurt, LockBit, Quantum, and Royal variants, making it challenging for defenders to prepare adequately. The use of dual ransomware variants results in data encryption, exfiltration, financial losses, and increased harm to victim entities. This trend has been tracked since early 2021, and it complicates recovery efforts and increases ransom payout potential.
The focus on data destruction is a notable aspect of this advisory, as it underscores the importance of removing all tools/accounts left behind by ransomware actors to prevent the activation of destructive tools. Destructive wipers have been observed in ransomware attacks deployed in the context of war or geopolitical conflict, extending their reach beyond Ukraine to 24 countries in the first half of 2022.
Unprecedented Extortion Tactics
A new ransomware group, operating through the “Ransomed” blog, presents victims with a stark ultimatum: pay to protect their stolen files or face fines resembling data protection regulations, such as the EU’s GDPR. The group follows a common ransomware blog strategy, publicly naming victims and issuing menacing threats to expose sensitive data unless ransoms ranging from $54,000 to $218,000 are paid. These sums are notably lower than authentic GDPR fines, potentially designed to boost victim compliance.
Ransomed’s blog includes several named companies, including the Metropolitan Club, TransUnion, and State Farm, none of them reported recent data breaches. Concerns escalate due to the group’s claim of possessing the source code of Raid Forums, an illicit hacking forum seized last year, suggesting possible transformation into a full-fledged hacker forum, adding to cybersecurity community anxieties.
Data Exfiltration Trends
The observed uptick in data exfiltration, standing at 43.42% and marking a 1.3% rise from the previous year, underscores a noteworthy trend in the realm of cybersecurity. This surge in incidents reflects an evolving landscape where cybercriminals are strategically targeting organizations with the intent of pilfering sensitive data. The implications of this trend extend beyond mere statistical growth, painting a nuanced picture of the escalating sophistication and persistence of data theft practices.
Temporal Patterns and Ransomware Preferences
Exploring the temporal aspects of these attacks unveils intriguing insights. Threat actors, including ransomware operators, target organizations late in the day on Tuesdays, Wednesdays, and Thursdays. These mid-week assaults are strategically timed to capitalize on understaffed IT teams, which are less likely to detect intrusions and threat actor movement. Notably, ransomware incidents peak on Fridays and Saturdays, exploiting the challenge of reaching tech teams and slower response times.
RDP Exploitation
Remote Desktop Protocol (RDP) remains a favored tool among cybercriminals, implicated in 95% of intrusions. Given its prevalence, securing RDP should be a top priority for organizations. Denying unauthorized access via RDP can significantly deter attackers, compelling them to invest more time and effort, thus increasing the likelihood of intrusion detection. (Examples of RMM tools: Atera, TeamViewer, SolarWinds RMM, and Kaseya VSA)
The advancing sophistication of MaaS is an ongoing influence on the cyber threat landscape. As technology progresses, threat actors exploit more advanced tools, presenting significant challenges for cybersecurity professionals. The dynamic evolution of MaaS, coupled with heightened sophistication in malware attacks, poses substantial risks across individuals, businesses, and governments.
Adaptive Attack Vectors
The range of MaaS offerings will introduce new and adaptive attack vectors. Organizations and individuals must remain vigilant against multifaceted threats, such as advanced phishing schemes and polymorphic malware that continually evolves to evade detection.
Linux Targeting
In the realm of malware, the increasing sophistication is evident in the targeting of diverse platforms. While Windows-powered devices were historically the primary focus, a notable shift includes the targeting of Linux and VMware ESXi hosts. This expansion highlights the adaptability of malware operators, leveraging new technology trends to maximize the impact of their malicious activities.
Recent developments emphasize this shift, as numerous active ransomware groups have placed a significant focus on infiltrating VMware ESXi servers and crafting specialized Linux encryptors specifically designed for this objective. What makes ESXi servers an enticing target for ransomware operators is their efficiency in targeting and encrypting virtual machines. Armed with potent payloads, cybercriminals can swiftly compromise and encrypt fully virtualized infrastructures within minutes, underscoring the speed and efficiency of these malicious attacks.
Additionally, to stay agile and versatile, ransomware operators are now opting to construct their malicious software using programming languages like Rust and Go. These languages enable threat actors to swiftly adjust their malware to various platforms, achieving feature parity across payloads designed for Windows, Linux, and ESXi systems. The utilization of memory-safe programming languages, such as Rust and Go, offers distinct advantages, facilitating faster and more complex encryption methods while providing deeper control over compromised systems.
This collective shift toward ESXi server exploitation reflects a concerted effort by cybercriminals to capitalize on vulnerabilities within ESXi systems. Consequently, organizations must fortify their security measures and take proactive steps to safeguard their virtualized infrastructure against the ever evolving and increasingly sophisticated ransomware threats.
Polymorphic Malware
Polymorphic malware is a highly sophisticated form of malicious software that continually modifies its code and appearance while retaining its core functionality. This dynamic nature poses a significant challenge for conventional antivirus and security systems, as the constantly evolving code makes detection and mitigation difficult.
Utilizing advanced techniques, polymorphic malware alters its code, generating multiple variants to evade detection by signature-based security measures. This adaptability sets polymorphic malware apart from static or traditional malware. The primary objective of polymorphism is to evade security tools’ detection, enabling the malware to persist and execute malicious activities.
Third Party Vendor Attacks
In 2022, a spike in targeting third-party vendors almost doubled from 2021, with 63 attacks on vendors being reported and 298 victims. This trend of increasing attacks on third-party vendors has only continued in Q1 of 2023 as several third-party vendors have reported being attacked by malicious campaigns. There are several dangers when third-party vendors are attacked. The insight the primary organization has into their vendors’ security protocols is reported as extremely limited as only 11% of companies feel they understand each party’s cyber security and practices. Only 32% of organizations report that they believe their suppliers will let them know in the instance of a breach. It was found that the average disclosure time between a breach occurring, and the vendor being notified was 108 days (about 3 and a half months). This was an increase of 50% from 2021 which provides threat actors with an additional month of time increasing the potential damage against vendors with stolen data.
- Unauthorized network access: These types of attacks generally originate from social engineering attacks through targeted phishing campaigns. Threat actors try to gain access to the network through stolen credentials or exploiting known vulnerabilities or a combination of the two.
- Ransomware: These attacks rely on threat actors acquiring internet infrastructure and maintaining ways to process payments which has become more difficult as monitoring of crypto currency has increased.
- Unsecured servers and databases: Unsecured assets such as databases and servers present a significant risk to companies allowing threat actors easy entry. If a third-party manages PII (Personal Identifiable Information) on behalf of another organization this risk can be even greater.
- Misconfigured server: This type of issue has become associated with cloud vendors or advertising companies leaking sensitive data. However, when an organization uses a cloud service there is a shared responsibility for maintaining the security of any information stored in the cloud. Server misconfiguration attacks exploit configuration weaknesses or security vulnerabilities found in web servers and application servers. Often cloud companies or advertising companies assume that the responsibility of security is with the primary organization while the organization assumes that the third-party vendor is responsible for the security.
Compromised Employee Credentials
Darknet Markets facilitate cybercriminals in acquiring employee credentials, enabling the use of genuinely compromised information to mimic normal employee behavior. Exploiting inadequately configured monitoring tools, hackers gain entry and meticulously observe organizational activities and employee behaviors. This methodical approach involves studying routine processes to navigate the network discreetly, delaying intrusive actions like data exfiltration to evade early detection.
Enhanced Cybersecurity Measures
In the ever-evolving threat landscape where breaches are inevitable, swift action is imperative. Adherence to established best practices, including multi-factor authentication, the principle of least privilege, zero-trust principles, and early detection mechanisms, is crucial.
Ineffective security architectures, compounded by understaffed and undertrained security teams, significantly prolong breach remediation timelines. Skill shortages and inadequate training compromise the effectiveness of cybersecurity teams, leading to misconfigurations of security tools and overlooking critical alerts.
Additionally, timely patch management, guided by threat intelligence, is imperative in effectively mitigating vulnerabilities. The human element, reflected in skill shortages and training gaps, emphasizes the need for streamlined security architectures and continuous skill development within cybersecurity teams.
Furthermore, automation and integrated security platforms are progressive measures that offer support to security personnel, addressing organizational shortcomings. These collectively contribute to a more resilient and responsive cybersecurity posture, essential in the face of the ever-evolving and persistent landscape of cyber threats.
Conclusion
Addressing these organizational gaps is crucial, underscoring the vital role of the human element in cybersecurity. To fortify defenses, organizations should proactively retain data, conducting regular checks for early threat detection. Proactive data monitoring is pivotal, providing insights for defenders and incident responders to swiftly address emerging issues.
The cybersecurity landscape spans a spectrum of threats, from minor intrusions to severe breaches, affecting businesses of all sizes. Cybercriminals, whether state-sponsored or individuals, employ diverse tools like malware and ransomware. As MaaS offerings expand, defenders must navigate a dynamic threat landscape by staying informed about emerging trends, understanding specific risks, and adopting proactive cybersecurity measures.
Detecting breaches swiftly is pivotal, indicating potential security deficiencies and emphasizing the role of Chief Information Security Officers (CISOs). Addressing systemic issues enabling persistent breaches should be a priority, necessitating a radical overhaul of security frameworks. The proliferation of MaaS varieties, lower entry barriers, escalating sophistication, and adaptive attack vectors highlights the need for constant vigilance, proactive security measures, and adaptive defense protocols in the evolving cybersecurity landscape.
Critical Start offers a pioneering solution to modern organizational challenges in aligning cyber protection with risk appetite through its Cyber Operations Risk & Response™ platform, award-winning Managed Detection and Response (MDR) services, and a dedicated human-led risk and security team. By providing continuous monitoring, mitigation, maturity assessments, and comprehensive threat intelligence research, they enable businesses to proactively protect critical assets with measurable ROI. Critical Start’s comprehensive approach allows organizations to achieve the highest level of cyber risk reduction for every dollar invested, aligning with their desired levels of risk tolerance.
References:
- https://blog.knowbe4.com/scam-as-a-service-classiscam-expands-impersonation-attacks
- https://thehackernews.com/2023/09/the-rise-of-malicious-app.html
- https://www.darkreading.com/attacks-breaches/researchers-uncover-raas-affiliate-distributing-multiple-ransomware-strains
- https://www.techradar.com/pro/security/theres-a-dangerous-new-malware-as-a-service-on-the-rise-heres-what-you-need-to-know
- https://blog.knowbe4.com/scam-as-a-service-classiscam-expands-impersonation-attacks
- https://thecyberexpress.com/snatch-ransomware-group-fdva-cyber-attack/
- https://news.sophos.com/en-us/2023/08/23/active-adversary-for-tech-leaders/
- https://www.inforisktoday.com/speed-demons-ransomware-attackers-dwell-time-shrinks-a-22906
- https://www.bleepingcomputer.com/news/security/ransomware-hackers-dwell-time-drops-to-5-days-rdp-still-widely-used/
- https://www.cybersecuritydive.com/news/ransomware-attack-dwell-times-sophos/691576/
- https://www.itpro.com/security/data-breaches/breached-for-years-how-long-term-cyber-attacks-are-allowed-to-linger
- https://www.securityinfowatch.com/cybersecurity/article/53028581/tips-on-reducing-dwell-time-of-bad-actors
- https://www.embroker.com/blog/cyber-attack-statistics/#:~:text=According%20to%20IBM%2C%20it%20takes,more%20trouble%20for%20your%20company
- https://www.varonis.com/blog/data-breach-response-times
- https://www.comparitech.com/blog/vpn-privacy/data-breach-statistics-facts/
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
