The Rise of the Cybercriminal

Critical Start CRU predicts the rapid evolution of cybercrime, along with the increasing use of APT tactics by cybercriminals, is set to significantly impact the cybersecurity landscape in 2024. Cybercriminals are expected to further refine their APT techniques, complicating detection, and mitigation. This refinement may involve using artificial intelligence, machine learning, and advanced social engineering in spear-phishing campaigns. Their ability to persist in victim networks and carry out precise attacks will pose a grave risk to various entities. The adoption of APT techniques by cybercriminals represents a significant shift in the cybersecurity landscape, impacting governments, businesses, and individuals.
The Rise of the Cybercriminal
The evolution of cybercrime, spanning from its origins in the 1990s to its current trillion-dollar status, parallels the developmental trajectory of legitimate businesses, driven by a continuous pursuit of enhancing return on investment (ROI). Initially motivated by personal prestige, cybercrime transitioned to profitability with the recognition of internet-based financial opportunities between 1990 and 2006. The World Economic Forum (WEF) now ranks cybercrime as the world’s third-largest economy, impacting businesses of all sizes. Criminals, even with low technical skills, exploit affordable access to networks and malware, launching sophisticated attacks, particularly targeting healthcare, education, and business. The preferred method involves exploiting security gaps for ransomware deployment.
Projections estimate cybercrime to generate $8 trillion in revenue by the end of 2023 and $10.5 trillion in 2025, with ransomware contributing significantly. This revenue encompasses various costs, including damage to data, stolen funds, lost productivity, intellectual property theft, personal and financial data breaches, embezzlement, fraud, post-attack disruptions, forensic investigations, data restoration and deletion, and reputational harm. Additionally, recent data reveals that 25% of ransomware attacks in 2023 were orchestrated by new players in the cybercriminal domain.
The analysis indicates an increasing convergence of tactics, targets, and personnel between criminal and nation-state actors. Traditionally relying on ransomware or phishing attacks for quick monetization, cybercriminals have shifted towards more lucrative and sustainable methods as cybersecurity measures improved. Advanced Persistent Threat (APT) tactics have become a favored approach. Looking ahead to 2024, the rapid evolution of cybercrime and the increasing use of APT tactics are expected to significantly impact the cybersecurity landscape. APTs, characterized by persistence and prolonged presence within a victim’s network, are no longer exclusive to nation-states, posing a formidable challenge with their custom malware, zero-day vulnerability exploitation, and advanced evasion techniques.
The Adoption of APT Tactics
The adoption of APT techniques by cybercriminals signifies a profound and consequential shift in the cybersecurity landscape, exerting far-reaching implications across governments, businesses, and individuals alike.
In the realm of government entities, the integration of APT techniques introduces a formidable challenge to national security. Traditionally associated with nation-states pursuing sensitive information or aiming to disrupt critical infrastructure, APTs now extend their influence beyond geopolitical borders. This expansion of APT tactics to non-state actors amplifies the complexity of defending against cyber threats at a national level. Governments must contend with the reality that cybercriminals are no longer confined by geographical boundaries, posing a potent risk to classified information, critical infrastructure, and the overall stability of nations.
For businesses, the adoption of APT techniques represents a direct assault on the heart of organizational operations and intellectual property. APTs are characterized by their persistence and prolonged presence within a victim’s network, allowing cybercriminals to stealthily navigate through systems, exfiltrate sensitive data, and orchestrate precise attacks. The impact on businesses extends beyond financial losses, encompassing the compromise of proprietary information, disruption of operations, erosion of customer trust, and potential legal ramifications. The need for sophisticated cybersecurity measures becomes paramount as organizations navigate this evolving threat landscape.
At the individual level, the adoption of APT techniques equates into heightened risks to personal privacy and security. Cybercriminals leveraging APT tactics may target individuals with precision, exploiting vulnerabilities in personal devices, networks, and online activities. This intrusion into private lives can result in identity theft, financial losses, and unauthorized access to personal information. The pervasiveness of APT techniques underscores the importance of individual cybersecurity awareness and the implementation of robust personal protective measures.
APT Techniques being utilized by Cybercriminals:
- Extended Campaigns: APT-style cybercriminals engage in extended campaigns, infiltrating a victim’s network and remaining undetected for long periods. This allows them to quietly exfiltrate valuable data, such as intellectual property, financial information, or personal data.
- Spear-Phishing: Just like APT groups, cybercriminals have refined their spear-phishing techniques. These attacks are highly targeted, often involving the creation of convincing emails or documents that appear legitimate. They aim to trick specific individuals into revealing sensitive information or downloading malicious payloads.
- Zero-Day Exploits: Cybercriminals are now using zero-day exploits, previously a hallmark of APT actors. Zero-day vulnerabilities are those for which no patch or fix exists, making them highly valuable for launching effective attacks.
- Infrastructure Mimicry: To avoid detection, cybercriminals mimic the tactics, techniques, and procedures (TTPs) of known APT groups. They utilize similar command and control servers, malware delivery methods, and evasion techniques.
- Concealing Presence: Cybercriminals invest time and effort in concealing their presence, employing tactics to avoid detection by security systems. This includes using anti-forensic techniques to erase their tracks and blend in with normal network traffic.
Real-World Examples:
- Ryuk Ransomware: Ryuk is a prime example of cybercriminals adopting APT-style tactics. It often starts with a spear-phishing campaign, gains access to a network, moves laterally, and carefully selects high-value targets for ransomware deployment.
- DarkTequila Banking Trojan: DarkTequila is another illustration of APT-style tactics in cybercrime. It targets financial institutions and has an extensive infrastructure designed for data theft. It evades detection by constantly changing its delivery mechanisms and command and control servers.
Heightened Sophistication
In the evolving landscape of cybercrime, several key trends are poised to shape the future of cybersecurity. Cybercriminals are anticipated to enhance their Advanced Persistent Threat (APT) techniques, posing increased challenges for detection and mitigation. The cyber landscape reveals a restructuring of cyber gangs into an as-a-service model, incorporating artificial intelligence and machine learning. Cybercriminal organizations now offer kits for various attacks, creating a pervasive malware-as-a-service ecosystem, with 91% of advertised exploits costing under $10, attracting non-technical individuals.
Notably, the study by the World Economic Forum (WEF) identifies ransomware-as-a-service (RaaS), cyber insurance, and material gain motivation as top contributors to cybercrime. The criminal underground exhibits a convergence of cybercrime gangs and nation-states, with major syndicates operating from geopolitically adversarial nations like Russia, China, Iran, and North Korea. RaaS shows a consistent increase year over year, with a significant spike observed in 2023, particularly in ransomware attacks. In March 2023, ransomware attacks spiked 91% in comparison to March of 2022 and a 62% increase in February 2023 compared to February 2022. The top RaaS provider in March of 2023 was Cl0p which accounted for 28% of all victims while LockBit 3.0 came in second with 21%. Royal, a non-affiliated ransomware group, was the third most active with attacks increasing 106% from February 2023 to March 2023 attacks.
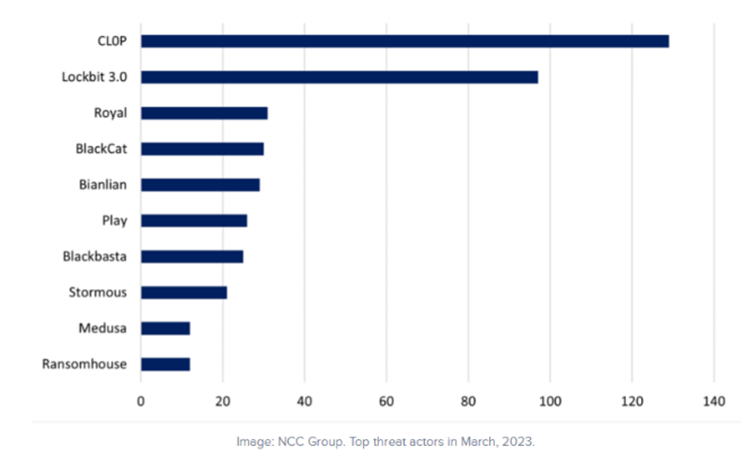
Furthermore, a significant development within cybercrime involves the creation of specialized groups focusing on selling storage space and providing training. These groups play a crucial role in shaping the cyber threat landscape by facilitating the exchange of digital storage resources among cybercriminals and imparting knowledge to new actors. This symbiotic relationship acts as a force multiplier, enabling cybercriminal organizations to scale operations and innovate rapidly. The commodification of storage space contributes not only to enhanced operational efficiency but also to the covert infrastructure supporting various cyber threats.
Simultaneously, training-focused groups in the cybercriminal underworld act as cyber academies, lowering the entry barrier for aspiring individuals. Structured training programs nurture the capabilities of new actors, resulting in a new generation of threat actors armed with advanced proficiencies. This educational dimension significantly contributes to the sophistication of cyber threats, creating a dynamic and challenging cybersecurity landscape.
Cybercriminal Groups Collaborating
From a collaborative perspective, the evolving dynamics of darknet markets, especially with the surge of Russian language platforms, signify a transformative shift in the way cybercriminals collaborate and conduct illicit transactions. The emergence of Russian language darknet markets is not merely a reflection of individual enterprises vying for dominance; rather, it portrays a collective effort within a linguistic community to reshape the landscape of cybercriminal collaboration.
Russian Darknet Markets
- Blacksprut: $20 million in March, 2023
- Kraken: $10 million in March, 2023
- Mega: $40 million in March, 2023
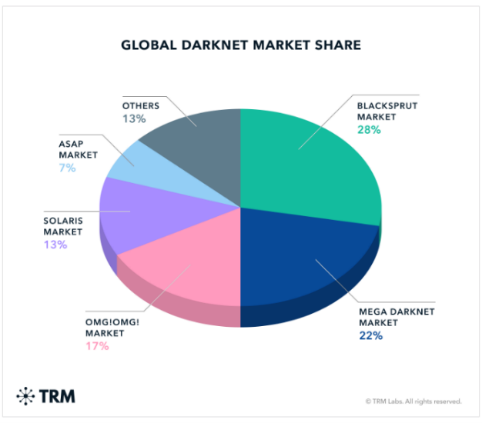
These platforms, swiftly ascended to prominence and collectively contributed to an astounding 80% of overall darknet market revenue, exemplify a collaborative initiative within the Russian-speaking cybercriminal community. The adaptability of illicit online marketplaces highlights a shared understanding and cooperative effort to establish these platforms as major revenue contributors. This collaboration speaks to the sophistication and extensive reach of a network of cybercriminal enterprises operating collaboratively within the darknet ecosystem.
The prevalence of Russian language darknet markets underscores the global nature of cybercriminal activities, transcending geographical boundaries through a shared linguistic medium. The concentration of illicit transactions and cyber activities within this linguistic sphere suggests a high degree of collaboration, potentially facilitated by a common language and cultural context. This collaborative effort goes beyond individual endeavors, marking a departure from the traditional structure of clandestine online marketplaces towards a more interconnected and cooperative paradigm.
The factors propelling the ascendancy of Russian language darknet markets are diverse and complex. The collaboration within this linguistic community is likely fueled by a combination of growing expertise and technical prowess among Russian-speaking cybercriminals, a robust infrastructure supporting these collaborative platforms, and unique economic factors that foster collective participation in illicit activities. The strategic adaptation to capitalize on a burgeoning user base, leveraging shared language and cultural context, further exemplifies the collaborative nature of these platforms.
The rise of Russian language darknet markets as major revenue generators represents a collaborative milestone in the ever-evolving realm of cybercrime. This collaborative trend not only underscores the adaptability and interconnectedness of cybercriminal enterprises but also emphasizes the imperative for a collaborative and comprehensive global approach to cybersecurity. As these collaborative platforms continue to shape the darknet economy, understanding the collaborative forces driving their prominence becomes essential for collaboratively mitigating cyber threats on a global scale.
Cybercriminal Groups Collaborating:
Hive, Royal, Black Basta
The first group of threat actors that have been sharing TTPs involve Hive, Royal, and Black Basta. In recent ransomware attacks by these groups the same granular similarities in the forensics of the attack revealed they all used the same specific usernames and passwords to gain access to the targets systems. Additionally, all three RaaS groups delivered the .7z payload with the same executing commands with the same batch scripts and files on the infected systems.
FIN7 and Ex-Conti hackers
FIN7 and ex-Conti hackers have both been using the new Domino malware family to spread info-stealers or Cobalt Strike. The Domino malware is a new family of malware discovered in 2023, allegedly created by the FIN7 threat group. The malware leverages DNS security gaps to breach corporate systems and has two components – a backdoor and a loader that injects an info-stealing malware DLL into the memory of another process.
Rhysida Ransomware and Vice Society
Rhysida is a relatively new threat actor that has developed ransomware that utilizes a set of unique TTPs similar to Vice Society. Vice Society activity has recently ceased, and the group is assessed to have disappeared. This has led to speculation that these two groups have potentially merged which would explain why the TTPs utilized were identical. Additionally, both cybercriminal groups are known to target the same industries of the education and healthcare sector.
8Base, RansomHouse, Phobos
8Base ransomware group was recently noted as using a ransom note that appeared to be a direct copy of RansomHouse’s ransom notes. Additionally, 8Base used the same language and data leaks portals that RansomHouse uses. Furthermore, a Phobos ransomware sample was discovered that used the “.8base” file extension suggesting that Phobos and 8Base are connected.
Broadening Target Sectors
The expansion of Advanced Persistent Threat (APT)-style tactics beyond their traditional association with espionage and critical infrastructure disruption is a pivotal development in the contemporary threat landscape. These sophisticated tactics, characterized by their persistence and prolonged presence within a victim’s network, are now proliferating across various sectors. This expansion poses heightened risks for specific industries, with financial institutions, healthcare organizations, and large corporations being particularly susceptible due to the potential financial gains associated with successful attacks.
The risk assessment stratifies critical infrastructure, which includes utilities and hospitals, as being at a Very High risk, indicating the severity of potential cyber threats. Additionally, sectors such as banks, telecommunications, technology, chemicals, energy, and transportation services are categorized as High-risk, signifying a substantial level of vulnerability within these domains.
A notable concern arises from the impact of cyberattacks on targeted organizations, as evidenced by the alarming statistic that 60% of entities subjected to cyberattacks reportedly go out of business within six months of falling victim. Financial motivations remain the primary driving force behind cybercriminal activities, highlighting the lucrative nature of the cyber threat landscape. The motivations within the cybercrime realm predominantly revolve around monetary incentives, compelling organizations of all sizes to fortify their cybersecurity measures.
The evolving landscape of cyber threats necessitates a proactive and adaptive approach to cybersecurity, especially given the collaborative nature of the cybercriminal ecosystem. This collaborative paradigm, reminiscent of legitimate business development, emphasizes the imperative for continuous skill enhancement and the rapid evolution of skill sets within the cybercriminal community. As cybercriminals, including new entrants, invest efforts in refining their skills, companies face an elevated risk of becoming prime targets. The dynamic and evolving nature of cyber threats requires organizations to be vigilant, proactive, and responsive in fortifying their cybersecurity posture to mitigate potential risks and safeguard against the ever-growing sophistication of cyber adversaries.
Regulatory and Legal Consequences
The active involvement of government organizations in responding to ransomware attacks and aiding companies in their recovery processes has marked a transformative shift in the cybersecurity landscape. This increased engagement has yielded a notable reduction in ransom payments by organizations, underscoring the positive impact of collaborative efforts between public and private sectors. As companies grapple with the escalating financial repercussions of cyber-attacks, a strategic response has emerged in the form of the widespread adoption of cyber insurance.
The incentive behind companies turning to cyber insurance is rooted in the desire to mitigate the out-of-pocket costs associated with responding to ransomware incidents. However, the landscape of cyber threats is dynamic, and cybercriminals have swiftly adapted to this risk mitigation strategy. Recognizing that the maximum cyber insurance payout for ransomware incidents surpasses their initial ransom demands, threat actors have adjusted their tactics accordingly. This adaptation has manifested in an increase in ransom demands within ransom notes, with threat actors now targeting amounts as high as $800,000 to align with the maximum insurance payout rate.
The surge in the adoption of APT techniques within the realm of cybercrime introduces a new layer of complexity to the threat landscape. This sophisticated approach, characterized by persistence, and prolonged presence within a victim’s network, is anticipated to draw increased regulatory scrutiny and legal consequences. As a response to the evolving threat landscape, the introduction of stricter cybersecurity regulations is foreseeable. Law enforcement agencies are expected to intensify their efforts to identify and prosecute cybercriminals employing APT tactics, reflecting a broader trend towards increased accountability and legal repercussions for those utilizing advanced and persistent cyber threats.
Challenges for Defenders
The dynamic evolution of the cyber threat landscape is underscored by a concerning trajectory marked by the rising utilization of shared tools and low attribution techniques among cyber threat actors. This not only diminishes the precision of identifying culprits but also poses a formidable challenge for defenders in discerning adversaries. Consequently, a diverse and expanding pool of cybercriminals continues to emerge, introducing complexity to the task of accurately identifying and countering persistent and sophisticated threats.
Adding to the challenge, the collaborative dynamics within the cyber threat landscape are further heightened by clusters of cyber threat actors engaging in coordinated efforts. This collaboration is evident in the open exchange of technical expertise, coding, and a streamlined timeline between ransomware updates. Moreover, these actors may share valuable target information, creating opportunities for double extortion within collaborating groups. This collaborative trend within the cyber threat landscape introduces a heightened level of agility, facilitating rapid shifts in security within the ransomware ecosystem. Therefore, cybersecurity experts are faced with an increasingly complex task of developing effective mitigation techniques to stay ahead of these evolving threats.
Furthermore, the prevailing landscape of economic uncertainty has emerged as a significant catalyst for the notable surge in cybercriminal activities. This economic backdrop propels individuals toward cybercrime, initiating a progression from seemingly innocuous activities to deeper involvement in sophisticated criminal networks. The allure of illicit activities becomes more enticing as traditional economic structures face disruptions, and individuals grapple with financial instability.
Navigating this intricate landscape, cybersecurity professionals find themselves confronting adversaries equipped with sophistication and persistence traditionally associated with nation-state actors. The blurred boundaries between nation-state APTs and cybercriminals further complicate attribution and threat intelligence efforts. This multifaceted challenge demands a nuanced and adaptive approach to cybersecurity to effectively address the ever-evolving nature of cyber threats.
Conclusion
The influx of new actors into the cybercrime landscape introduces a dynamic and evolving element, necessitating a proactive approach to cybersecurity. The growing adoption of APT tactics by cybercriminals is set to raise the bar for cyber threats, presenting a serious risk to various entities. Their capacity to persist in victim networks and execute precisely targeted attacks amplifies the threat landscape. Projections indicate a continuous increase in the cybercrime economy year over year, with threat actors exploiting the same victims over extended periods. A recent surge in cybercrime entities collaborating has been noted, intensifying the severity and sophistication of future attacks and targeting strategies.
Threat actors are expected to persist in targeting companies that have not patched their software, emphasizing the importance of proactive cybersecurity measures. Recommendations include the implementation of secure access controls, network segmentation, multi-factor authentication, and regular testing and evaluation of backup strategies to mitigate the impact of potential ransomware attacks. Organizations are advised to conduct inventories of externally facing services to minimize the attack surface available to threat actors. Ongoing employee training and bolstering email security solutions are crucial for detecting and thwarting threat actors before they breach network perimeters, contributing to overall network health.
In this ever-changing and escalating arms race against cybercrime, defenders must anticipate the continuous evolution of adversaries. Collaboration and information sharing within the cybersecurity community emerge as vital components in staying ahead of these adaptive cybercriminals. As the threat landscape evolves, the battle against cybercrime demands a collective and concerted effort to ensure the resilience and security of digital ecosystems.
References
Critical Start CRU Published: https://www.criticalstart.com/the-evolution-of-cybercrime-adapting-to-apt-techniques/
- https://cybersecurityventures.com/cybercrime-to-cost-the-world-8-trillion-annually-in-2023/
- https://i-hls.com/archives/117897
- https://cybernews.com/editorial/cybercrime-world-third-economy/#:~:text=Cybercrime%20has%20grown%20to%20become,and%20%2410.5%20trillion%20by%202025
- https://thecyberexpress.com/a-year-after-hydra-darknet-market-shut-down/
- https://www.trmlabs.com/post/eight-months-after-the-hydra-shutdown-new-russian-language-darknet-markets-fill-the-void
- https://www.techrepublic.com/article/ransomware-attacks-increased-march/
- https://www.securityweek.com/how-next-gen-threats-are-taking-a-page-from-apts/
- https://www.splunk.com/en_us/blog/learn/apts-advanced-persistent-threats.html
- https://ts2.space/en/advanced-persistent-threats-a-new-era-of-cyber-warfare/
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
