Threat Research: RustBucket Malware Takes Aim at macOS

Summary
A recently observed malware family dubbed “RustBucket” has been targeting macOS since early 2023. RustBucket is a multi-stage malware that focuses on secondary payload delivery. Cybersecurity analysts at Jamf Threat Labs have attributed the malware to BlueNoroff, a financially motivated division of North Korea-based advanced persistent threat (APT) Lazarus Group.
RustBucket’s Multi-Stage Infection Chain
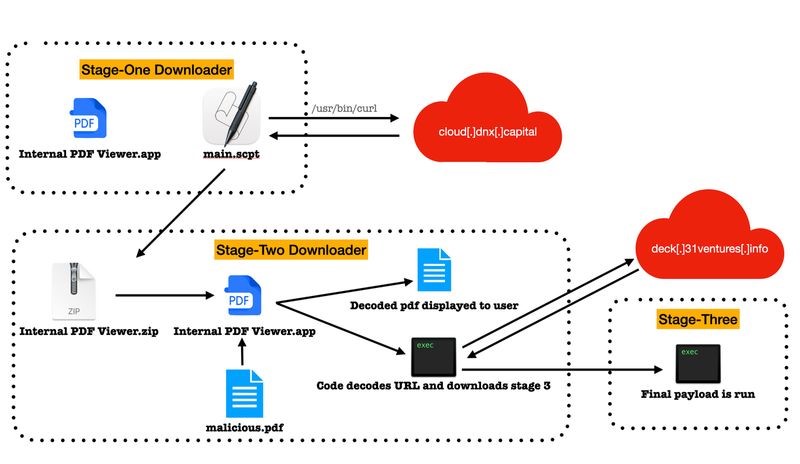
Analysis of RustBucket samples revealed three distinct stages of the malware infection. The first stage is included within an unsigned application called “Internal PDF Viewer.” It executes various shell script commands to obtain and execute the second-stage payload. The second stage, written in Objective-C, is a signed application masquerading as a legitimate Apple bundle identifier. The follow-on attack chain is triggered when a specially crafted PDF is opened through the app. This special PDF launches a decoy to the victim designed to appear as though it was taken from a website of a genuine venture capital firm. Once executed, it communicates with the attacker’s command and control (C2) server to obtain the stage-three payload; a signed trojan written in Rust that can run on both x86 and Access Rights Management (ARM) architectures. Post-infection, the malware gathers system details and allows the attacker to perform different actions on the infected machines.
The BlueNoroff Connection
Cybersecurity experts assess RustBucket is connected to BlueNoroff due to tactical and infrastructural overlaps with previous campaigns. Specifically, the domain used by the stage-one payload was used in prior BlueNoroff activity. Additionally, the social engineering lures used for the trojanized PDF are similar to previous fake domains utilized by the group.
North Korean-based BlueNoroff is known for cyber theft operations focused on infiltrating the SWIFT system and cryptocurrency exchanges. As one of the more advanced factions of the notorious state-sponsored Lazarus Group, it’s likely BlueNoroff has been inspired by Lazarus’ success in targeting macOS.
Conclusion
The discovery of RustBucket highlights the continued sophistication and evolution of BlueNoroff in the changing cyber landscape. The multi-stage composition of the malware, in addition to the use of Rust programming language and the targeting of macOS, make detection and prevention a significant challenge. As macOS increases its market share, it’s assessed more threat actors will develop malware specifically targeting the operating system to increase the number of possible targets. It is critical for individuals and organizations to remain vigilant and take proactive measures to secure their devices against such threats.
_______________________________________________________________________________________________________________
The Critical Start Cyber Threat Intelligence (CTI) team will continue to monitor the situation and work closely with our SOC to implement any relevant detections. For future updates, the CTI team will post via ZTAP® Bulletins and on the Critical Start Intelligence Hub.
References:
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
