WannaCry? You Might.
Urgent Information Regarding WanaCrypt/WannaCry/WCry Ransom-ware Outbreak
Today, 12 May 2017, a massive ransomware outbreak has been reported across the globe. There are reports of computer systems completely locked up in Russia, Western Europe, East Asia, and North America. British hospitals and a Spanish telecom company have been the largest confirmed victims thus far, along with a Spanish financial institution. Critical Start Security Researchers along with additional 3rd party sources have also witnessed activity showing active infections across the remaining continents.
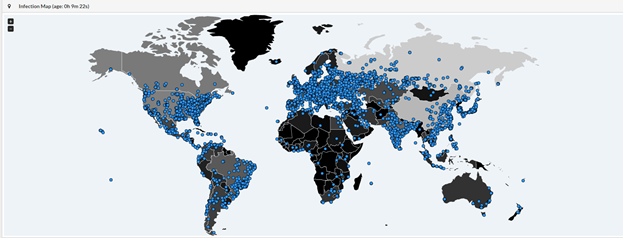
What Can I Do About It?
Immediate Recommendations:
If your enterprise has not installed the latest Windows Update bundles, this needs to be an immediate priority. Downtimes for upgrades and security patches will cost far less than potential data and productivity losses. Windows XP systems do not have a current patch available**, but some mitigation can be offered by properly configured firewall settings and network segmentation. For those leveraging Cylance, devices in an auto-quarantine policy have complete protection from file encryption.
For additional information, please feel free to contact your account manager. Follow our Security Blog for additional information on emerging technologies, security recommendations, and news.
Technical Details:
High Priority
WanaCryptor 2.0, WannaCry, WCry or WCryp is currently a world-wide ransom-ware outbreak. These are all versions of Crypto-locker, encrypting victim files and demanding payment via bit-coin. This vulnerability was patched in the Microsoft March update (MS17-010).
The following links contain information about the exploit that the new malware is using (based on ETERNAL BLUE) and the fix and temporary workaround for servers and local clients, as well as firewall configuration recommendations.
- SANS ISC InfoSec Write-up
- https://isc.sans.edu/forums/diary/ETERNALBLUE+Windows+SMBv1+Exploit+Patched/22304/
- EternalBLUE PCap data was also provided: https://isc.sans.edu/diaryimages/eternalblue.pcap
- How to disable SMB .v1 (lateral movement mechanism)
- https://docs.microsoft.com/en-us/windows-server/storage/file-server/troubleshoot/detect-enable-and-disable-smbv1-v2-v3
- This is the current exploit mechanism being used for moving within enterprise. The movement has been detected from Cloud Sync file-share as well.
- The link contains information on disabling SMBv1 (which is the only recommended service to disable) via Servers, Powershell, and local Client.
- Firewall Configuration
- Ensure that port 445 is blocked for firewall communications with all exceptions scrutinized and verified before adding.
Note: Microsoft did release a patch for Windows XP and Server 2003. See our newer blog posts for additional details.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
