Azure Sentinel: Notifications of New Detection Rules
The CRITICALSTART Cybersecurity Consulting Services for Microsoft Security team is dedicated to helping you maximize the value of your cybersecurity investment. With that in mind, we will be posting periodic blog updates to keep you informed of the latest developments affecting your Microsoft Security solutions.
Today, we will examine the intersection of two key Microsoft Azure Sentinel workstreams for the modern security operations center (SOC):
- Nearly- constant enhancements for data connectors
- Nearly- constant new detection rules
Since Microsoft does not currently provide notifications when a new detection rule is published, security teams must manually monitor new detection rules and connectors.
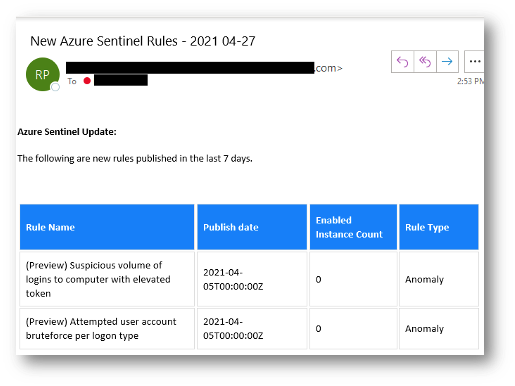
Our Azure Sentinel automation playbook for new detection rule alerting is designed to streamline this process. The automation is primarily composed of an Azure Logic App that queries the Microsoft Graph Security application protocol interface (API) for new rules published in the last seven days, composes the update, and sends an email notification to your security team.
End Result:
Deploy:
To deploy the template:
- Download template here.
- Go to the Microsoft Azure Portal.
- In the top search bar, type Deploy.
- Choose “deploy a custom template”.
- Choose ”Build my own template in the editor”.
- Upload the JavaScript Object Notation (JSON) file from the GitHub template.
- Click Save.
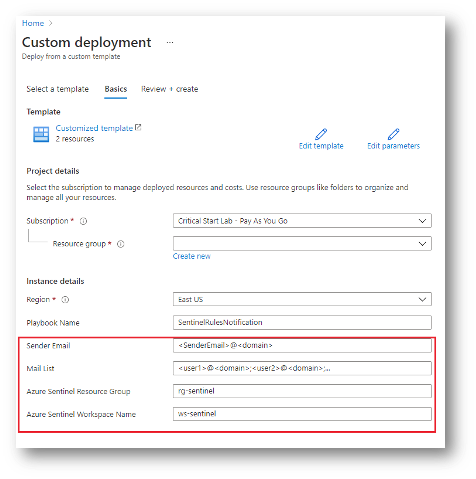
- Select Subscription and the resource group in which the logic app should be deployed.
- Update Parameters:
- Sender Email -> Office 365 email account that will be used to send the email
- Mail List -> Comma separated email addresses of recipients
- Azure Sentinel Resource Group -> Resource group where Azure Sentinel log analytics workspace is deployed
- Azure Sentinel Workspace Name -> Azure Sentinel log analytics workspace name where Azure Sentinel is deployed
- Click Review + Create to deploy the logic app.
You will need to authenticate a connection for the Sender Email account:
- Navigate to Resource Group where the logic app was deployed.
The template also creates an API Connection resource which will be given a name like the name you provided for the logic app.
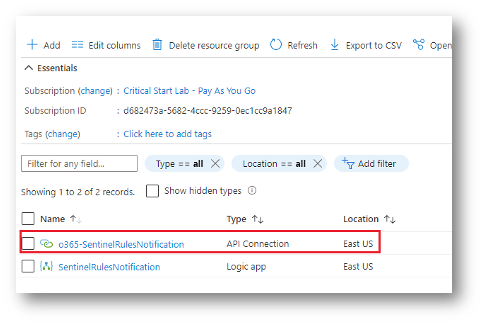
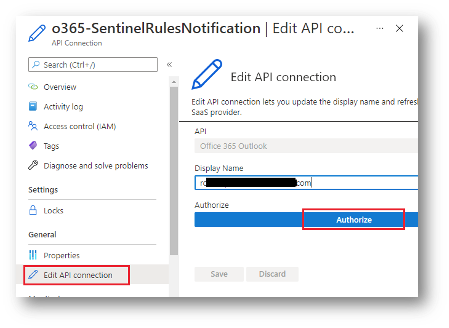
- Click the API Connection to open its configuration blade.
- Select Edit API Connection from the left menu.
- Click Authorize.
Lastly, you will need to enable Managed Identity for the logic to use for the Microsoft Graph Security API calls.
- Navigate to the logic app created earlier.
- From the left menu, select Identity and set the status to ON.
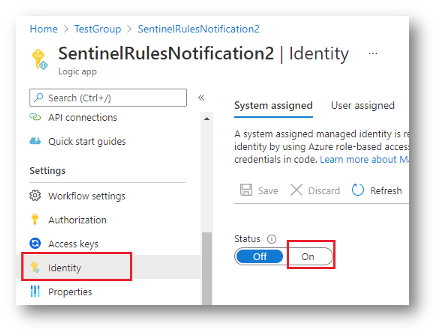
- Once enabled you will be able to assign the new Managed Identity roles.
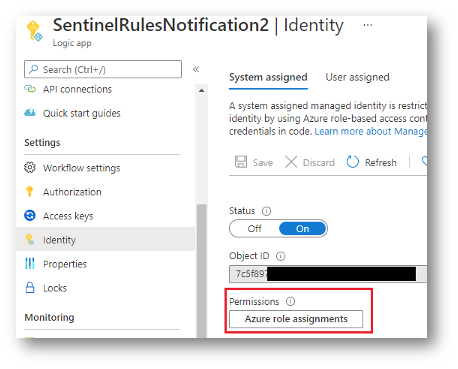
4. Assign Azure Sentinel Contributor role at the resource group level where Azure Sentinel workspace is deployed.
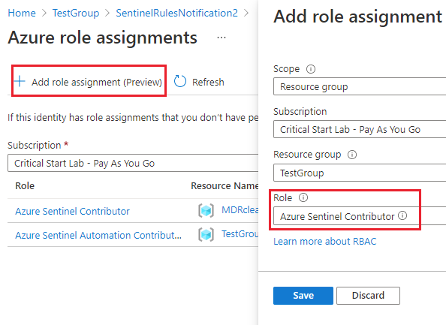
- Go back to your logic app and click Run.
After the initial run, the logic app will activate every seven days.
You have successfully configured the solution, and your security team should be receiving email notifications every seven days with details of newly published detection rules.
If you have any questions, please email: [email protected].
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
