How to Plan a Migration from SIEM Solutions to Microsoft Sentinel
by: Ronald Prasad, Microsoft Services Principal
Migrating to Microsoft Sentinel can help make your security operations (SecOps) team more efficient. Microsoft provides a shared responsibility model for Microsoft Sentinel, which means your team’s time and resources are spent dealing with security, not infrastructure. A cloud-native security information and event management (SIEM) platform such as Microsoft Sentinel also drives significant cost savings. Recent economic studies found that Microsoft Sentinel is 48% less expensive than traditional on-premise SIEMs.
Getting started with your SIEM migration project can seem daunting, especially if you have spent years building custom use cases and content for your existing SIEM tool. That is why it’s important to properly plan your migration to ensure that there are no gaps in coverage during the migration, which could put the security of your organization in jeopardy, and to confirm that all use cases and content are fully migrated before the final cutover.
CRITICALSTART has developed a migration plan to help you avoid potential pitfalls and ensure a smooth transition from an existing SIEM to Microsoft Sentinel.
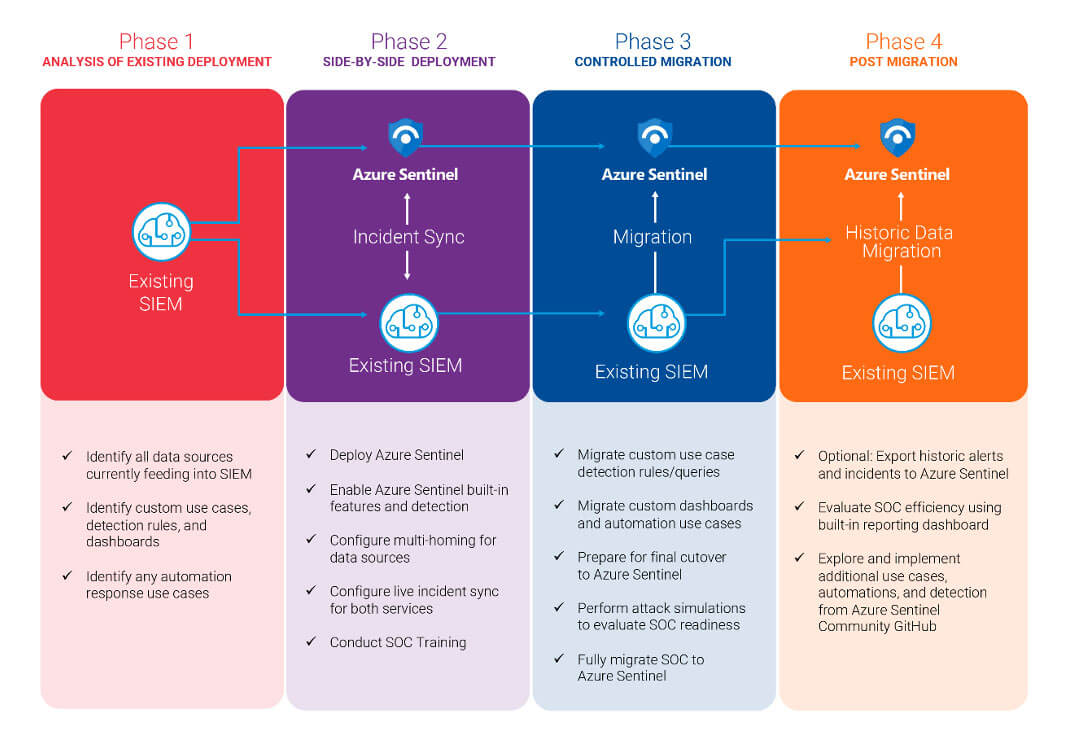
Our four-phased approach provides instructions on how to plan and perform a full production migration of an existing SIEM to Microsoft Sentinel, as follows:
Phase 1: Analysis of Existing Deployment
- Identify all data sources currently feeding into the existing SIEM
- List all network appliances, such as firewalls.
- Verify current log collection profiles for network appliances.
- List all virtual machines/endpoints currently monitored via SIEM.
- Identify all cloud-native services currently monitored via SIEM.
- Identify custom use cases, detection rules, and dashboards
- Identify and analyze all existing detection rules and queries.
- Identify and analyze any existing SOC flow implementations.
- List all required security operations center (SOC) reporting dashboards.
- Identify any automated response (SOAR) use cases
- Identify and analyze all SOC automated response workflows.
- Identify any existing ticketing automation workflows.
Phase 2: Side-by-side Deployment
- Deploy Microsoft Sentinel
- Deploy Microsoft Sentinel in a centralized subscription.
- Use Microsoft’s recommended best practice for Microsoft Sentinel deployment.
- Provide SOC team access. Permissions in Microsoft Sentinel | Microsoft Docs
- Enable Microsoft Sentinel built-in features and detection
- Enable log/data collection using built-in connectors for well-known services. Connect data sources to Microsoft Sentinel | Microsoft Docs
- Enable built-in detection rules.
- Enable CEF-based log collection from services that do not have an out-of-the-box data connector in Microsoft Sentinel.
- Configure multi-homing for data sources
- Configure additional log forwarding rules for network appliances to send logs to Microsoft Sentinel in parallel to existing SIEM.
- Configure multi-homing for log collection agents for virtual machines/endpoints.
- Configure live incident sync for both services
- Deploy Microsoft Automation to sync SIEM alerts to Microsoft Sentinel and vice versa.
- Conduct SOC Training
- Educate and train SOC team on how to perform investigations and incident lifecycle management in Microsoft Sentinel.
Phase 3: Controlled Migration
- Migrate use case detection rules/queries
- Use https://uncoder.io/ to transform existing SIEMs detection queries into Microsoft Sentinel KQL.
- Migrate dashboards and automation use cases
- Prepare for final cutover to Microsoft Sentinel
- Perform attack simulations to evaluate SOC readiness
- Perform attack simulation for network-based security products.
- Fully migrate SOC to Microsoft Sentinel
Phase 4: Post-Migration
- Optional: Export historic alerts and incidents to Microsoft Sentinel
- Deploy Microsoft automation for SIEM data exporting to Microsoft Sentinel.
- Evaluate SOC efficiency using built-in reporting dashboard
- Track SOC Metrics, such as mean time to triage and mean time to closure, using Security operations efficiency workbook.
- Explore and implement additional use cases, automations, and detections from the Microsoft Sentinel Community GitHub.
Summary:
The plan outlined above should help you ensure a successful migration. If you need assistance, the CRITICALSTART Cybersecurity Consulting Services for Microsoft Security team has performed numerous migrations to Microsoft Sentinel for large enterprises and is always available to assist with your migration effort. CRITICALSTART is a Microsoft MSSP Program Partner and member of the Microsoft Intelligent Security Association.
Contact your Microsoft or CRITICALSTART sales representative to learn more.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
