What do a $10 billion funding request for cybersecurity, a massive collection of 3.2 billion passwords hitting the web, and the godfather of threat detection have in common?
Among other things, they’re all featured in Episode 2 of our new SON OF A BREACH! podcast series, “Chuvakin be kidding me,” available now.
Tune in to hear host Randy Watkins, CRITICALSTART’s Chief Technology Officer, share his perspectives on recent news topics:
- President Biden’s cybersecurity funding request of $10 billion. “This is not a partisan issue, and this is also not a partisan podcast,” says Watkins. “I do think it’s interesting, though, that it was lumped into the COVID relief bill. What does cybersecurity have to do with COVID relief?” Watkins encourages listeners to ask their state representatives to introduce a standalone bill with funding for cybersecurity.
- The new normal of advanced persistent threats (APTs). “Given we’ve had two or three additional attacks since the initial discovery of the SolarWinds breach, it looks like APTs are becoming the new normal,” he says. “I’ve read a number of articles over the last couple of weeks that really emphasize the importance of not focusing on retaliation, but instead focusing on defense. I generally think that’s the correct approach.”
- The massive COMB (combination of multiple breaches) collection of 3.2 billion passwords hitting the web. Watkins points to the need for multi-factor authentication (“If there’s one thing we can depend on, it’s users reusing passwords”) and user education. He urges organizations to use this incident as an opportunity to bolster their own security practices, saying, “Let the users know you’re not just into it for the corporate security, but also the individual user security. Security starts at the user.”
Joining Watkins for this podcast episode is threat detection and security expert, Dr. Anton Chuvakin, who currently focuses on security solution strategy for Google Cloud.
For several years, Dr. Chuvakin covered security operations and detection and response topics at Gartner, where he was Research Vice President and Distinguished Analyst at Gartner’s Technical Professionals (GTP) Security and Risk Management Strategies team. He has authored several books and published dozens of papers on the topics of security information and event management (SIEM), log management, and Payment Card Industry Data Security Standard compliance.
Watch Out for These to Get the Most Value From SIEM
Some organizations falter with SIEM utilization, log management, and detection correlation, Dr. Chuvakin says, due to a variety of reasons.
“I have encountered more projects killed by mismatched expectations than anything else,” he says, adding that lack of headcount, talent, and sufficient resources to keep SIEM running, and lack of a use case approach have “sunk a fair number of projects, too.”
He also observes, “Lately, the frustrations of trying to make good insights, good security insights, out of bad data have kind of boiled over.”
Tips for Approaching SIEM and Detection Use Cases
Dr. Chuvakin recommends organizations step back and consider use cases before they actually implement SIEM in their environment.
“Start thinking, okay, what are my use cases?” he advises. “Am I buying for compliance? Reporting? Am I buying it to support my incident responders? If I’m detecting threats, what kind of threats? … What sort of data do I need to get?”
Instead of approaching SIEM as a huge detection project, Dr. Chuvakin suggests coming at it as “a sequence of use cases where you iterate, you learn, you implement simpler ones, and then you grow to others.”
Perspectives on Detection and Response Models
While at Gartner, Dr. Chuvakin coined the term “endpoint threat detection and response” to describe what was then a new family of tools designed to increase visibility by using endpoint data. From that came extended detection and response (XDR), which uses multiple data sources for even more visibility in detection and response.
Asked for his thoughts on XDR, Dr. Chuvakin says his perspective has evolved over the years. “My initial reaction a couple of years ago about XDR was kind of annoyance. But at the same time, it was invented at a competing analyst firm, so it’s sort of a normal reaction.”
He says he remains a SIEM fan, but the starting point for detection can be EDR as a viable alternative. “If you expand from that point, you become extended from EDR, and that’s XDR. So, to me, the XDR is a security threat detection monitoring model where the EDR leads, and then other things extend from that.”
Want to learn more about cybersecurity options for your organization? Contact us today.
Additional Resources:
- In need of a data privacy playbook, download here.
- Are you considering a Managed Detection and Response Service as part of your overall security infrastructure? Learn how to deploy an MDR platform that can protect any business in the guide to Managed Detection and Response.
- Dive into Infosec Reborn, a new playbook to understand, adapt, and overcome in the hyper-sophisticated threat environment of today’s world.
- Ready to talk to an MDR Expert? Contact us today.
![]()
Ransomware in 2025: The Real Risk, the Gaps That Persist, and What Actually Works
Ransomware attacks aren’t slowing down. They’re getting smarter, faster, and more expensive. In ...![]()
Security Operations Leaders: The Chaos Is Real
If you’re a CISO, SOC leader, or InfoSec pro, you’ve felt it. Alert volumes spike. Tools multipl...![]()
Transform Vulnerability Management: How Critical Start & Qualys Reduce Cyber Risk
In a recent webinar co-hosted by Qualys and Critical Start, experts from both organizations discusse...![]()
H2 2024 Cyber Threat Intelligence Report: Key Takeaways for Security Leaders
In a recent Critical Start webinar, cyber threat intelligence experts shared key findings from the H...![]()
Bridging the Cybersecurity Skills Gap with Critical Start’s MDR Expertise
During a recent webinar hosted by CyberEdge, Steven Rosenthal, Director of Product Management at Cri...![]()
2024: The Cybersecurity Year in Review
A CISO’s Perspective on the Evolving Threat Landscape and Strategic Response Introduction 2024 has...![]()
Modern MDR That Adapts to Your Needs: Tailored, Flexible Security for Today’s Threats
Every organization faces unique challenges in today’s dynamic threat landscape. Whether you’re m...![]()
Achieving Cyber Resilience with Integrated Threat Exposure Management
Welcome to the third and final installment of our three-part series Driving Cyber Resilience with Hu...Why Remote Containment and Active Response Are Non-Negotiables in MDR
You Don’t Have to Settle for MDR That Sucks Welcome to the second installment of our three-part bl...![]()
Choosing the Right MDR Solution: The Key to Peace of Mind and Operational Continuity
Imagine this: an attacker breaches your network, and while traditional defenses scramble to catch up...![]()
Redefining Cybersecurity Operations: How New Cyber Operations Risk & Response™ (CORR) platform Features Deliver Unmatched Efficiency and Risk Mitigation
The latest Cyber Operations Risk & Response™ (CORR) platform release introduces groundbreaking...![]()
The Rising Importance of Human Expertise in Cybersecurity
Welcome to Part 1 of our three-part series, Driving Cyber Resilience with Human-Driven MDR: Insights...![]()
Achieving True Protection with Complete Signal Coverage
Cybersecurity professionals know all too well that visibility into potential threats is no longer a ...![]()
Beyond Traditional MDR: Why Modern Organizations Need Advanced Threat Detection
You Don’t Have to Settle for MDR That Sucks Frustrated with the conventional security measures pro...The Power of Human-Driven Cybersecurity: Why Automation Alone Isn’t Enough
Cyber threats are increasingly sophisticated, and bad actors are attacking organizations with greate...Importance of SOC Signal Assurance in MDR Solutions
In the dynamic and increasingly complex field of cybersecurity, ensuring the efficiency and effectiv...The Hidden Risks: Unmonitored Assets and Their Impact on MDR Effectiveness
In the realm of cybersecurity, the effectiveness of Managed Detection and Response (MDR) services hi...![]()
The Need for Symbiotic Cybersecurity Strategies | Part 2: Integrating Proactive Security Intelligence into MDR
In Part 1 of this series, The Need for Symbiotic Cybersecurity Strategies, we explored the critical ...Finding the Right Candidate for Digital Forensics and Incident Response: What to Ask and Why During an Interview
So, you’re looking to add a digital forensics and incident response (DFIR) expert to your team. Gr...![]()
The Need for Symbiotic Cybersecurity Strategies | Part I
Since the 1980s, Detect and Respond cybersecurity solutions have evolved in response to emerging cyb...![]()
Critical Start H1 2024 Cyber Threat Intelligence Report
Critical Start is thrilled to announce the release of the Critical Start H1 2024 Cyber Threat Intell...![]()
Now Available! Critical Start Vulnerability Prioritization – Your Answer to Preemptive Cyber Defense.
Organizations understand that effective vulnerability management is critical to reducing their cyber...![]()
Recruiter phishing leads to more_eggs infection
With additional investigative and analytical contributions by Kevin Olson, Principal Security Analys...![]()
2024 Critical Start Cyber Risk Landscape Peer Report Now Available
We are excited to announce the release of the 2024 Critical Start Cyber Risk Landscape Peer Report, ...Critical Start Managed XDR Webinar — Increase Threat Protection, Reduce Risk, and Optimize Operational Costs
Did you miss our recent webinar, Stop Drowning in Logs: How Tailored Log Management and Premier Thre...Pulling the Unified Audit Log
During a Business Email Compromise (BEC) investigation, one of the most valuable logs is the Unified...![]()
Set Your Organization Up for Risk Reduction with the Critical Start Vulnerability Management Service
With cyber threats and vulnerabilities constantly evolving, it’s essential that organizations take...![]()
Announcing the Latest Cyber Threat Intelligence Report: Unveiling the New FakeBat Variant
Critical Start announces the release of its latest Cyber Threat Intelligence Report, focusing on a f...Cyber Risk Registers, Risk Dashboards, and Risk Lifecycle Management for Improved Risk Reduction
Just one of the daunting tasks Chief Information Security Officers (CISOs) face is identifying, trac...![]()
Beyond SIEM: Elevate Your Threat Protection with a Seamless User Experience
Unraveling Cybersecurity Challenges In our recent webinar, Beyond SIEM: Elevating Threat Prote...![]()
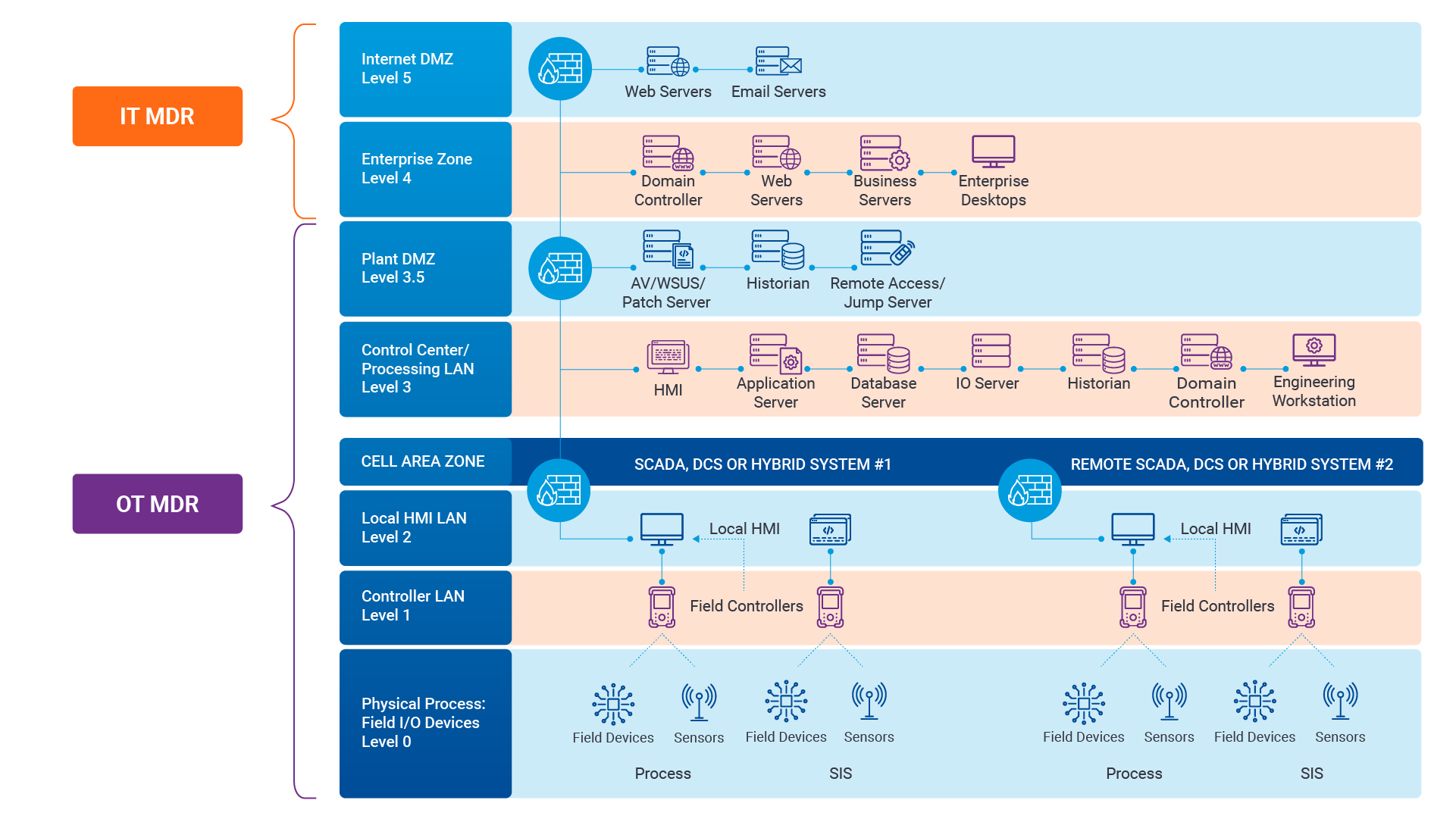
Navigating the Convergence of IT and OT Security to Monitor and Prevent Cyberattacks in Industrial Environments
The blog Mitigating Industry 4.0 Cyber Risks discussed how the continual digitization of the manufac...![]()
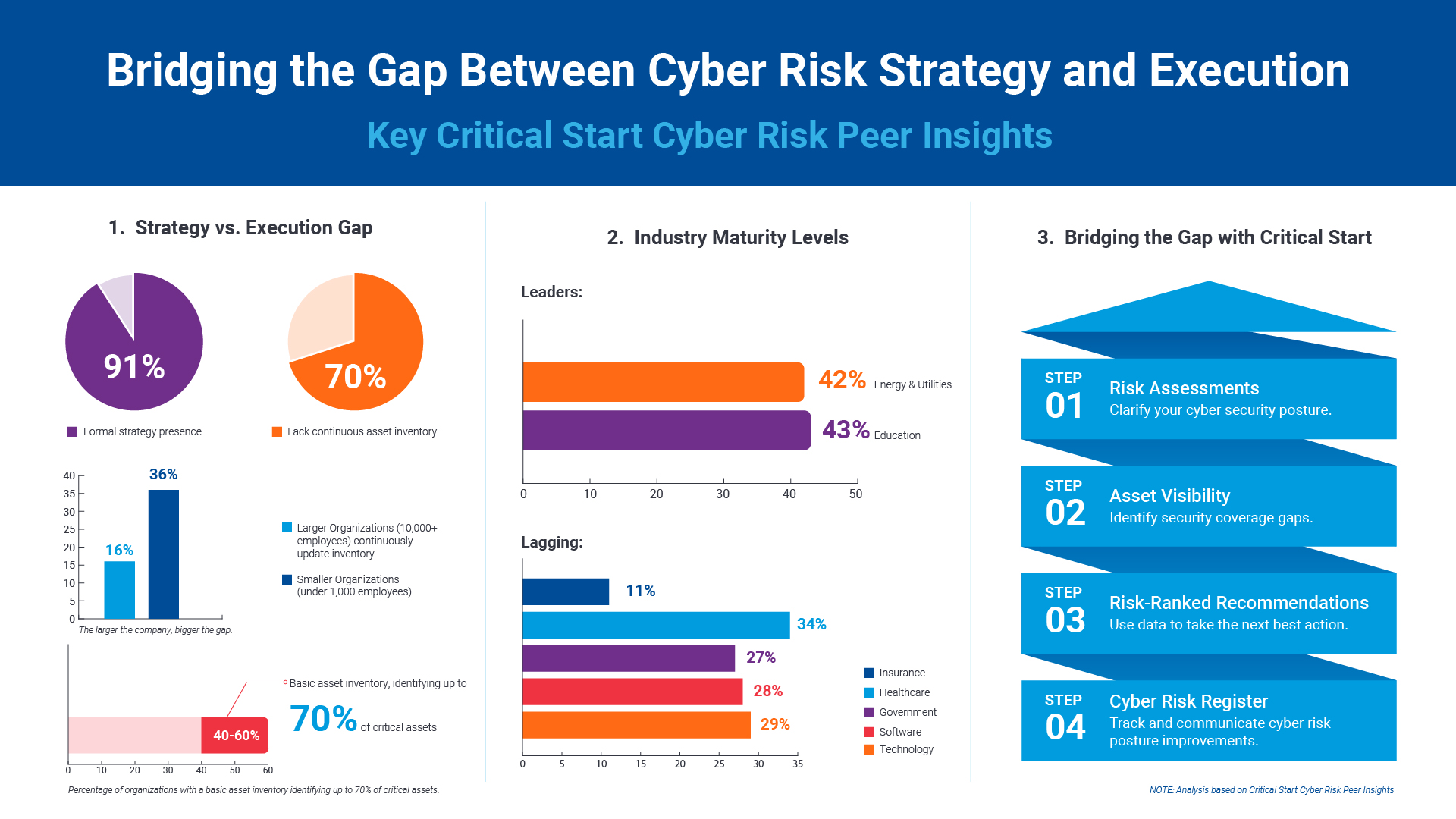
Critical Start Cyber Risk Peer Insights – Strategy vs. Execution
Effective cyber risk management is more crucial than ever for organizations across all industries. C...![]() Press Release
Press ReleaseCritical Start Named a Major Player in IDC MarketScape for Emerging Managed Detection and Response Services 2024
Critical Start is proud to be recognized as a Major Player in the IDC MarketScape: Worldwide Emergin...Introducing Free Quick Start Cyber Risk Assessments with Peer Benchmark Data
We asked industry leaders to name some of their biggest struggles around cyber risk, and they answer...Efficient Incident Response: Extracting and Analyzing Veeam .vbk Files for Forensic Analysis
Introduction Incident response requires a forensic analysis of available evidence from hosts and oth...![]()
Mitigating Industry 4.0 Cyber Risks
As the manufacturing industry progresses through the stages of the Fourth Industrial Revolution, fro...![]()
CISO Perspective with George Jones: Building a Resilient Vulnerability Management Program
In the evolving landscape of cybersecurity, the significance of vulnerability management cannot be o...![]()
Navigating the Cyber World: Understanding Risks, Vulnerabilities, and Threats
Cyber risks, cyber threats, and cyber vulnerabilities are closely related concepts, but each plays a...The Next Evolution in Cybersecurity — Combining Proactive and Reactive Controls for Superior Risk Management
Evolve Your Cybersecurity Program to a balanced approach that prioritizes both Reactive and Proactiv...![]()
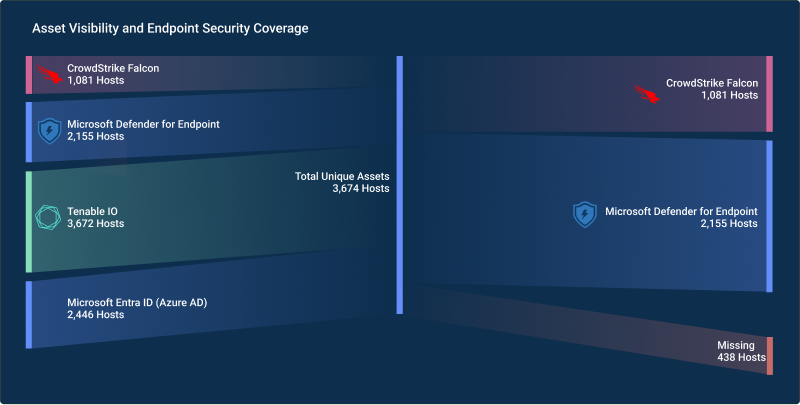
CISO Perspective with George Jones: The Top 10 Metrics for Evaluating Asset Visibility Programs
Organizations face a multitude of threats ranging from sophisticated cyberattacks to regulatory comp...- eBook
Ditch the Black Box: Get Transparent MDR with Critical Start
Tired of MDR providers leaving you in the dark? We totally get it. Our eBook, Unmatched Transparency... - eBook
Why the Most Secure Organizations Choose Critical Start MDR
Frustrated with MDR providers that fall short? We totally get it. Critical Start delivers unmatched ... ![]()
Drowning in Alerts: How to Cut the Noise and Focus on Real Threats
92 percent of organizations say they’re overwhelmed by an endless sea of alerts. It’s not just...
Newsletter Signup
Stay up-to-date on the latest resources and news from CRITICALSTART.
Thanks for signing up!