Balancing Act: How MOBILESOC can Ensure Cybersecurity while Protecting Time with Family
By Tommy Scott, Senior Security Consultant | CRITICALSTART
Closing the laptop and mentally disconnecting from work is a critical component of work-life balance. But there’s one problem: There are no days off in cybersecurity.
For many of us, it takes time and effort to transition between the different mindsets required for work and home. When you’re at home, you’re often confronted with the unfortunate reality that, at any given moment, an alert can occur forcing you back into the security mindset. It’s an event that can drag you away from important moments with your family, or in the case of the dreaded on-call rotation, robs you of your sleep.
The ideal scenario of leaving work at the office often cannot be sustained when the threat of a cyberattack remains constant. Even with attention given to security, one mistake is all it takes for an attacker to be successful. As organizations mature through enhanced detection and response capabilities with increased automation, they still face the increasing sophistication of attacks.
When it comes to security events, Murphy’s Law could be updated to state: “Incidents only occur as you are sitting down for dinner or two hours after your kids have been put to bed.” These incidents don’t care whether you’re watching your child’s soccer game or if you are somewhere without Wi-Fi access. When a notification comes, all family obligations must be set aside because timeliness and proper communication during an incident can be the difference between successful remediation and a successful breach. And when you’re away from your desk and computer, it can make answering the following questions difficult:
- What is the timeline of the incident?
- Is there access to the right information?
- Are you viewing all relevant data to be able to make any necessary decisions?
- Who needs to be notified or what escalation needs to occur?
Alerts from different consoles, tracking in ticketing systems, email communications, and phone calls turn what might only be minutes of actual response work into hours spent managing the incident and all communication involved. While incidents will never stop coming, day or night, how they are responded to can be made much easier and less disruptive to essential relaxation and family time.
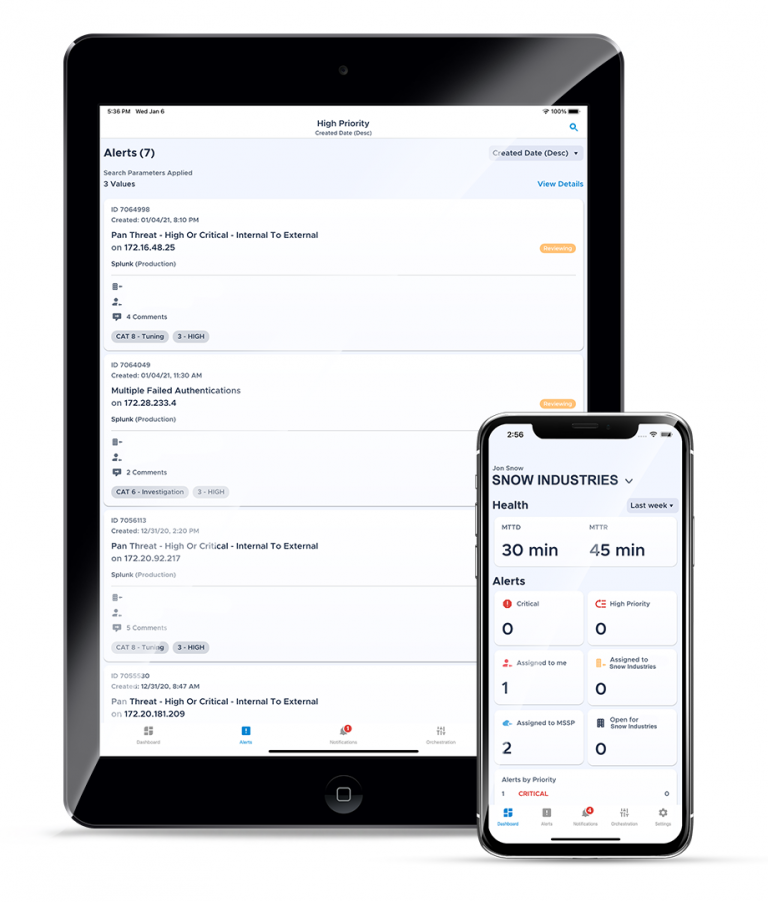
MOBILESOC Shifts the Balance
CRITICALSTART enables its customers to stop breaches by providing them a mobile security tool, MOBILESOC, backed by a 24x7x365 Security Operations Center. Escalations are made via push notification after an investigation by a highly trained CRITICALSTART analyst, reducing alert volume significantly. Providing complete transparency into why the escalation occurred, what actions have been taken, and prescriptive next steps empower our customers to quickly set the scope for a response.
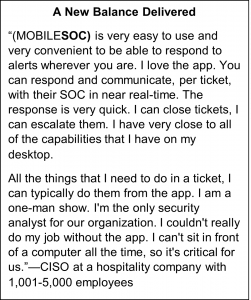
MOBILESOC allows CRITICALSTART Managed Detection and Response (MDR) services customers to be more decisive and certain when taking meaningful response actions to stop the breach in minutes rather than days. You can eliminate the need to step away from your family and pull out a computer to diagnose security incidents and determine what responses are necessary. With the information gathered from CRITICALSTART’s MDR platform, you can take responsive action straight from your phone and work directly with CRITICALSTART senior security analysts no matter your location.
MOBILESOC gives users the ability to isolate threats, stop breaches, and tip the scales back towards family and free time. And that balance can be worth its weight in gold.
Ready to talk to an MDR Expert? Contact us today.
Additional Resources:
- Dive into Infosec Reborn, a new playbook to understand, adapt, and overcome in the hyper-sophisticated threat environment of today’s world.
- Learn how Managed Detection and Response services boost the value of a traditional Security Operations Center. https://www.criticalstart.com/buy-vs-build/
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
