Zero-day Targeting Exchange Servers: Steps to Evaluate the Risk to Your Organization
By: Charlie Smith & Travis Farral
A zero-day has been announced targeting Exchange Servers. If you are running on-premises Exchange Servers within your environment, public facing or in a hybrid configuration, stop what you are doing, finish reading this article, and patch your Exchange Servers immediately!
Note: Customers exclusively using Exchange Online are not affected.
This zero-day uses multiple exploits that allow the threat actor to compromise on-premises Exchange Servers, allowing access to user mailboxes and install malware. Microsoft Threat Intelligence Center (MSTIC) has high confidence the group responsible for this attack is HAFNIUM and suspected to be state sponsored. Most organizations have moved to Exchange Online, however, some still have an Exchange hybrid environment deployed.
When these threats arise (which they will), having a risk mitigation program is paramount to your organization to detect and respond to threats. Although you may not have direct control on how third- party software is written, you do have control over your environment. Deploying the right security solutions provides advance detection capability across the organization to detect and respond to threats.
Due to the nature of recent Exchange Server zero-day exploits, we want to arm you with the information and readiness to act.
With that said, we will walk through:
- Who does this affect?
- What needs to be done?
- Where can I find the Exchange Server patch?
- Have I been affected by this exploit?
Who does this affect:
Currently this zero-day targets on-premises Exchange Servers 2010, 2013, 2016, 2019. This includes Exchange Server(s) internet public facing and hybrid. As mentioned before, this does not affect customers who are exclusively on Exchange Online.
If you are running on-premises Exchange 2010, 2013, 2016, 2019, assume that you are breached and continue reading.
What needs to be done:
Based on the version of Exchange and patch level, we need to ensure the appropriate Cumulative Update (CU) has been applied:
- Exchange Server 2019 CU 8 or 7
- Exchange Server 2016 CU 19 or 18
- Exchange Server 2013 CU 23
- Exchange Server 2010 SP3 Update Rollup 32
To do this, we need to check if you are vulnerable to this exploit. This can be accomplished a number of ways, however the easiest is through Microsoft Defender for Endpoint (MDE) or running a PowerShell command against your Exchange Servers.
Option 1 – Microsoft Defender for Endpoint:
Microsoft Defender for Endpoint (MDE) has a built-in Threat and Vulnerability Management (TVM) feature that assesses what endpoints are vulnerable to what threats. This is done from the Microsoft Defender Security Center portal –> Dashboards –> Threat Analytics
Locate the “Exchange Server zero-days exploited in the wild” threat and see how many endpoints are affected.
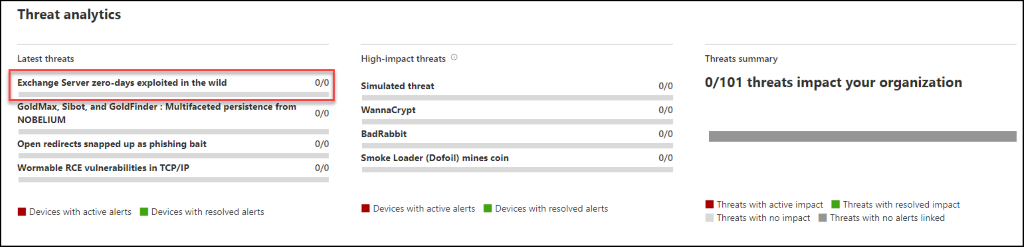
If you are vulnerable, this will list what devices are affected and the associated CVEs.
Option 2 – Exchange PowerShell:
Alternatively, we can run a few PowerShell commands to see what Exchange Cumulative Updates (CU) have been installed. This is done from an Exchange Server 2013, 2016, 2019 open the “Exchange Management Shell” console and run the following PowerShell command:
Get-ExchangeServer | Format-List Name,Edition,AdminDisplayVersion The “AdminDisplayVersion” field displays the build number (aka what CU you are currently on).
If you are running Exchange Server 2010, you will need to run the following PowerShell command:
Get-Command ExSetup | ForEach {$_.FileVersionInfo} Once we have the build number, it needs to be referenced using Microsoft’s Exchange Server build matrix grid (see below)
- Exchange Server 2019 found here
- Exchange Server 2016 found here
- Exchange Server 2013 found here
- Exchange Server 2010 found here
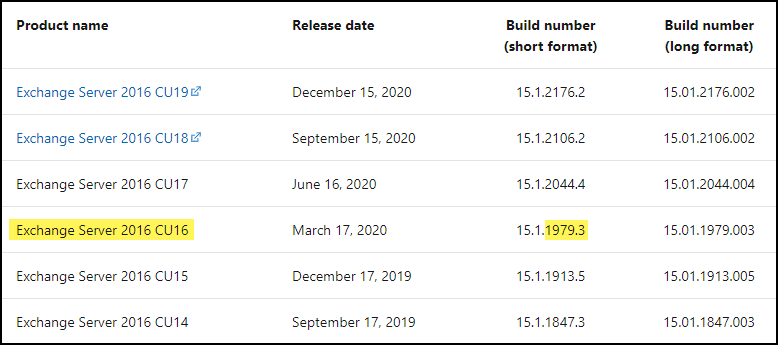
For example, if I am running Exchange 2016 and my build number is “1979.3“, this means I’m running “Exchange Server 2016 CU16” (see screen shot below). In other words, I need to apply “Exchange Server 2016 CU 19 or 18”
Where can I find the Exchange patch:
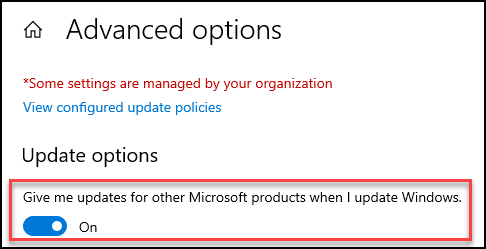
The simplest way to patch your Exchange environment is using good ol’ Windows Update. Just make sure the “Give me updates for other Microsoft products when I update Windows” is enabled (see screen shot below)
This method will pull down the latest updates for Exchange. Depending on your current patch level, you may have to run Windows Update a couple of times.
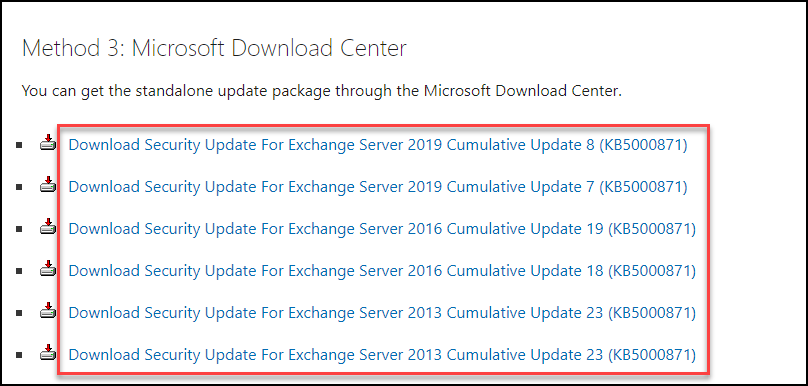
For those that need more of a “prescriptive” or “targeted” approach, you can also download the CU you need for your environment. Click here and download the CU you need (see screen shot below). For Exchange 2010, the update can be found here.
Have I been affected by this zero-day:
For our CRITICALSTART Manage Detection and Response (MDR) customers, our team has already created detections and is monitoring for this exploit.
For those that are not enrolled with our MDR services, here are a few steps you can take to see if you’ve been breached:
Step 1:
Microsoft has published a GitHub page (found here) to run a series of Powershell scripts to identify Proxylogons or BackendCookieMitigation
Step 2:
If you’re running an Endpoint Detection and Response (EDR) solution, such as MDE, look for the following behavior:
- Suspicious Exchange UM process creation
- Suspicious Exchange UM file creation
- Possible web shell installation (not unique to Hafnium attack)
- Process memory dump (not unique to Hafnium attack)
Reference: HAFNIUM targeting Exchange Servers with 0-day exploits
Step 3:
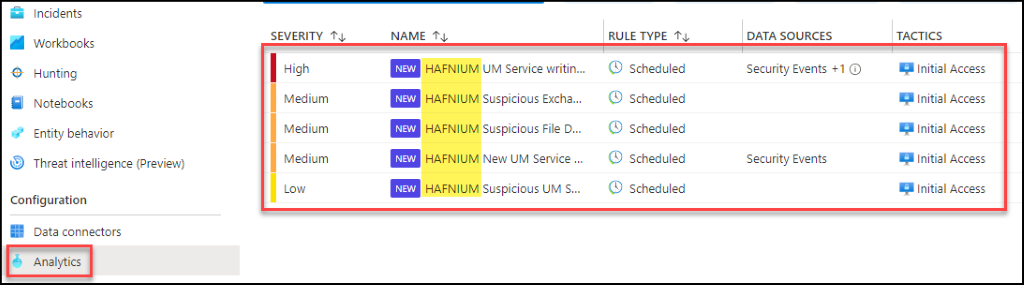
Using a SIEM such as Azure Sentinel, enable the following analytic rules (see screen shot below) and start monitoring for this attack
Based on results of the steps mentioned above, this will help determine if you have been breached.
Contact us today if you are concerned that you have been breached or would like to obtain additional information.
Put TEAMARES to work for you.
Offensive red team and defensive blue team services help you prepare your business for real-world threats. TEAMARES stands ready to help you understand your environment more deeply, assess how today’s attacks can impact your organization and how to better defend your environment from potential threats.
Incident Response (IR) and IR Retainers
Our Incident Response (IR) team helps you limit the dwell time of an attacker through immediate response, and we can proactively work with you to understand your preparedness with IR readiness services. Our IR retainers offer several options of professional service hours, and any unused hours may be applied to other IR and Professional Services engagements. Learn more.
Penetration Testing
We will conduct a compliance penetration test focused on the segmentation of Cardholder Data Environment (CDE) and other requirements set by PCI DSS compliance rules. Learn more.
Vulnerability Management
Our team will identify, classify, prioritize, remediate, and mitigate software vulnerabilities. Learn more.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
