CRITICALSTART® Security Services for SIEM
+ Devo
CRITICALSTART® Security Services for SIEM
+ Devo
Unlock the full potential of your Devo SIEM with our Managed Detection and Response (MDR) services.
Security Information and Event Management (SIEM) solutions don’t have to be complex.
With Devo’s cloud-native logging and SIEM capabilities and Critical Start’s proactive approach to MDR, you can simplify breach prevention, enhance your security posture, and gain unparalleled insights into your security framework.

Get optimal data ingestion into the Devo platform to expand visibility across your security operations landscape.

Benefit from precise log management by adding new Devo log sources and reducing false positives

Strategically add new data sources while continuously validating MITRE ATT&CK® Framework coverage.

We do all the heavy lifting for your SOC team with the combination of our Cyber Operations Risk and Response™ platform and seasoned Security Operations Center (SOC) and Threat Detection Engineering teams.
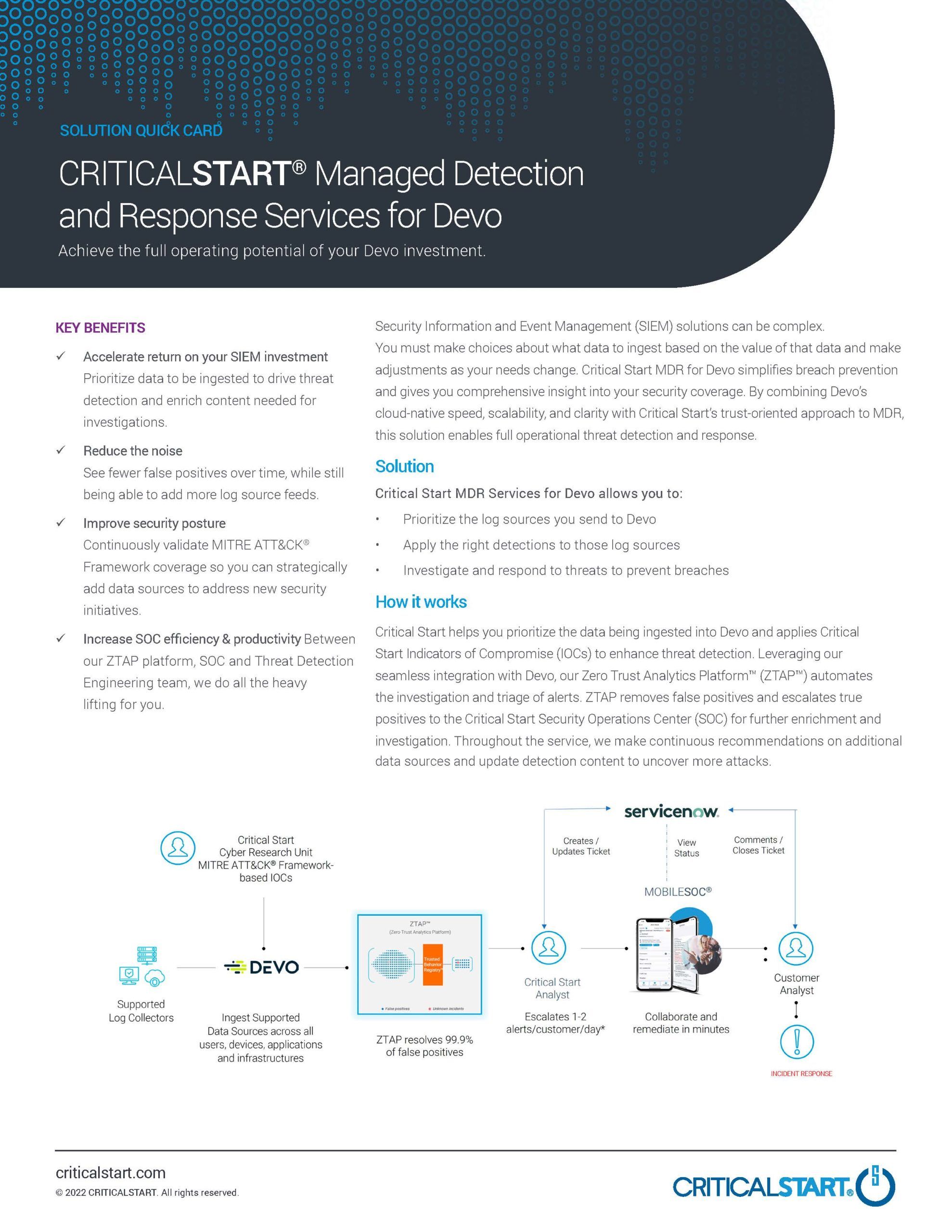
We help you prioritize the data ingested into your Devo SIEM and apply Critical Start Indicators of Compromise (IOCs) to enhance threat detection.
We validate that log sources are correctly configured and ingesting data by identifying and resolving SIEM coverage gaps, helping you maximize the threat-detection capabilities of your investment. Our experts help you sort out the highest fidelity, actionable telemetry, such as firewall threats, host systems, VPN, and cloud security. We also use data such as DNS, firewall traffic, vulnerability, and physical security for specific detections or enrichment.
Our platform automates the investigation and triage of alerts while eliminating false positives. True positives are escalated to our Security Operations Center (SOC) for further enrichment and investigation.
And it doesn’t stop there—we continuously recommend other data sources to add and update detection content to uncover new and emerging attacks, giving you a better return on investment (ROI) from your Devo solution.
A leading oil and gas company achieved these results in just one month after implementing Critical Start MDR for Devo:

We take on the complexity of cybersecurity while simplifying your daily operations. As a result, your security team is more efficient and productive, because they aren’t wading through an overwhelming number of alerts.

Onboard quickly:
Experience a Median Time to First Value (TTFV) of 2.66 days with our proven process that shortens the time it takes to start seeing results. Complete your total multi-product onboarding process quickly with a dedicated Customer Success Team that partners with you to ensure a seamless experience.
Personalize based on your unique requirements:
To improve threat detection and enrich the content needed for investigations, we’ll help you prioritize your Devo data sources and create playbooks to reduce false positives. We also use automation to help investigate and triage alerts across users, devices, applications, and infrastructure with our platform, which is seamlessly integrated with Devo.


Investigate and resolve alerts:
You get 24x7x365 security monitoring, investigation, and response from our U.S.-based SOCs with complete transparency and guaranteed 60-minute or less SLAs for Time to Detection (TTD) and Median Time to Resolution (MTTR) on every alert.
You can expect an approximately 90% reduction in false positives on the first day of production monitoring. We also boost your team’s efficiency by escalating only 1-2 alerts a day, and we never send you the same alert twice.
Our relationship continues after onboarding is complete. Your named Customer Success Manager will check in with you regularly to make sure that our services are still meeting your needs — even as your requirements change.
Mature your Devo investment:
As we work together, we’ll continue to help you achieve full operating potential for threat detection. As a result, your team will have more time to focus on strategic initiatives, and you’ll get the most out of your Devo security investment.

Our dedicated Threat Detection Engineering (TDE) team has deployed SIEMs in numerous Fortune 500 companies and has experience across multiple threat vectors and industries:
We take a different approach than most MDR providers by resolving every alert and only forwarding those that truly warrant additional investigation.
As a result, your team is more productive and can focus on strategic initiatives.
Our highly skilled analysts work in a SOC 2 Type 2 certified Risk and Security Operations Center (SOC) 24x7x365 to investigate, escalate, contain, and respond to threats, significantly reducing attacker dwell time.
Take threat detection and response on the go with MobileSOC, our full-parity iOS and Android application. An industry-leading first, MobileSOC puts the power of our platform in your hands so you can contain breaches and talk to our SOC right from your phone.
Security Information & Event Management (SIEM) solutions can be complex. Our MDR services for Devo simplifies breach prevention, reduces the noise of false positives and accelerates the return on your Devo investment.

Learn how our Managed Detection and Response (MDR) services for SIEM simplify the complexity of Security Information and Event Management (SIEM) implementations and help you get the most out of your SIEM investment.