Navigating Rising Ingestion Costs: Leveraging Critical Start’s Managed SIEM Solution for High-Priority Detections and Coverage Gaps

Data volumes continue to increase exponentially, putting a strain on organizations grappling with the challenges of rising ingestion costs from their Security Information and Event Management (SIEM) vendors. With 43% of security professionals feeling like they are paying too much for their current SIEM solution, security teams counteract this by trying to ensure their SIEM is only ingesting the most relevant security data. However, without expert guidance, this can leave organizations open to compromise.
The need for more comprehensive threat detection capabilities does not need to equate to a strain on budgets. With Critical Start Managed SIEM, a solution designed to tackle the twin challenges of rising SIEM ingestion costs and security blindspots, businesses can manage escalating costs and ensure that they are not compromising on the effectiveness of their cybersecurity strategy.
Not As Simple As They SIEM: Pain Points and Where We Go From Here
SIEM solutions are complex and require dedicated resources to run and maintain. For this reason, customers don’t routinely audit and manage their SIEM ingest, leaving their SIEM solutions to turn into a “Roach Motel” where data checks in but doesn’t check out.
Old, no longer relevant data impacts security expenditures due to un-forecasted budget increases, exacerbated when customers don’t have the tools to measure the security effectiveness of the data sources (i.e., mapping threat detection content and validate MITRE ATT&CK® Framework coverage to confirm ongoing security relevance), the ability to identify and continuously analyze log sources to ensure they are of the highest fidelity and close SIEM coverage gaps, or the expertise to know when to use expensive analytic log storage versus less expensive, basic log storage or even cold storage.
Despite these challenges, SIEM solutions remain popular and are part of an effective and holistic approach to cybersecurity. To help customers navigate rising ingestion costs and get the biggest ROI from their SIEM solution, Critical Start maximizes and keeps your total cost of ownership predictable and manageable with Ingest Cost Analysis and helps you keep up with new threats and compliance requirements by ensuring that your data is being properly ingested and that SIEM coverage gaps are addressed.
Cost Optimization without Compromising Threat Detection
Ingest Cost Analysis is the cornerstone of cost-effective SIEM management, and when done correctly, it does not compromise the quality of threat detection—in fact, it increases its efficacy. Optimizing financial stewardship and simplifying resource management gives you more control over your SIEM data, the use cases it supports, and escalation processes and operations. To reach this level of optimization, we recommend a “continuous optimization” approach, moving from a “set it and forget it” mentality to constant SIEM tuning to identify inefficiencies, redundancies, and other areas for optimization.
By identifying and rectifying inefficient or inconsistent data ingestion, organizations can optimize their resource allocation while ensuring every data point ingested contributes meaningfully to threat detection. In one instance, a financial institution identified redundant data sources inflating their ingestion costs. By eliminating these redundancies, they not only reduced costs but also improved the accuracy of their threat detection.
Closing SIEM Coverage Gaps: Increase Cyber Risk Resilience While Tackling Budget Challenges Head-On
Budget challenges don’t end with rising ingestion costs; they extend to the potential coverage gaps that can emerge as a consequence. In an attempt to cut costs, organizations might inadvertently overlook critical data sources, leaving blind spots in their threat detection capabilities.
These SIEM Coverage Gaps expose organizations to the risks and ramifications of undetected threats. Whether it’s a sophisticated malware attack or a subtle insider threat, these blind spots can be exploited, leading to data breaches and operational disruptions.
By integrating proactive measures to bridge these coverage gaps, Critical Start has created another way to improve detection rates and reduce dwell time, translating into quicker response times and minimizing damage in the event of a security incident.
Tertiary Detections: A Balancing Act in a Cost-Driven Landscape
Not all threats are created equal, and focusing on high-priority detections ensures that resources are allocated where they matter the most. High-priority detections aren’t just about identifying and neutralizing threats; they also directly impact the bottom line.
However, while organizations can tailor their detection strategies based on the priority of threats, ensuring that high-priority threats are not lost in the noise of low-level security events, they must not overlook the significance of tertiary detections (Fig 1). Though less immediate, these lower-priority threats can still pose a significant risk if left unchecked. Balancing the focus between high-priority and tertiary detections is a delicate yet necessary act.
Recently, there was a case of a retail organization focusing solely on high-priority threats related to customer data. In doing so, they might inadvertently ignore lower-priority threats, such as phishing attempts targeting employee credentials. Over time, these tertiary threats can escalate into major security incidents.
Employing a tiered approach to threat detection ensures that both high-priority and tertiary threats are addressed. This not only provides a comprehensive security posture but also prevents the accumulation of risks over time.
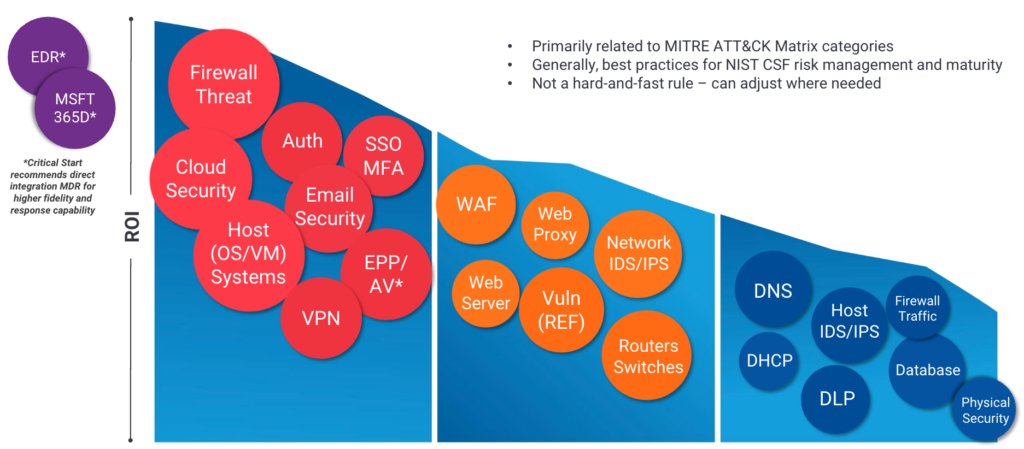
Aligning Critical Start Managed SIEM with Buyer Needs
The ultimate goal when deploying a SIEM is to ensure effective threat detection and prevention across the organization—and to get there by maximizing the SIEM’s performance. Critical Start helps make these goals a reality by empowering organizations to identify cost inefficiencies and actively work towards optimizing data ingestion for long-term cost-effectiveness tailored to their unique budgetary constraints and specific security needs. This involves thoroughly examining current data handling practices, identifying redundancies, and streamlining processes for maximum efficiency.
In addition, by addressing security coverage gaps, Critical Start ensures that every potential threat vector is accounted for, mitigating the risk of blind spots in threat detection.
The insights gained from Ingest Cost Analysis, coverage gap assessments, and prioritization strategies should be leveraged to enhance overall cybersecurity effectiveness. This involves aligning resources with the most critical threats, optimizing processes, and ensuring a proactive rather than reactive security posture.
A Solution for The Dual Challenges of Escalating Threats and Costs
As the cybersecurity landscape continues to evolve, the importance of strategic investments in threat detection cannot be overstated. With features including Ingest Cost Analysis and SIEM Coverage Gaps, Critical Start Managed SIEM not only mitigates the impact of escalating costs but also enhances overall cybersecurity effectiveness, helping organizations navigate the challenges of rising ingestion costs with confidence, ensuring a robust security posture without compromising budgetary constraints.
In a landscape where every dollar spent must yield tangible security outcomes, Critical Start Managed SIEM proves to be a strategic investment.
Click here for more information on Critical Start Security Services for SIEM, or contact an expert to have a conversation about your unique SIEM challenges and needs.

Director, Product Management | SIEM MDR
Steven Rosenthal, a cybersecurity expert, has spent his career assisting organizations in navigating technology threats. His experience includes a 12-year stint at IBM, managing complex data center projects, and leading IT program development at Dell EMC. As QTS Data Centers’ Head of Product Solutions, he guided product strategy and elevated the company’s market position. Steven is currently the Director of Product for Critical Start, where he shapes the company’s SIEM strategy and bolsters its cybersecurity posture. As a respected thought leader, Steven frequently shares his insights at industry events to help drive innovation and guide companies in building resilient and secure infrastructures.
You may also be interested in…
Stay Connected on Today’s Cyber Threat Landscape
RELATED RESOURCES
RESOURCE CATEGORIES
-
- Consumer Education(40)
- Consumer Stories(2)
- Cybersecurity Consulting(7)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(78)
- MobileSOC(9)
- News(5)
- Press Release(93)
- Research Report(11)
- Security Assessments(4)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)