SECURITY TOOLS
THREAT ANALYTICS SEARCH CHROME EXTENSION
Current Version 5.0.3 – Updated on 5/10/2021.
Version 5.0.0 – The extension was refactored and includes a refreshed UI, performance optimizations and updates to supported libraries. Going forward, our extension is now fully on GitHub. Follow extension updates in the GitHub Repository Release page here: https://github.com/AdvancedThreatAnalytics/threat-analytics-search/releases/
Version 4.0 – Updated on 5/7/2015 to add support for the 3rd group and the ability to HTTP POST in addition to GET. Also updated search providers – go to Options and click the “Refresh Now” button to see the new providers.
Chrome permissions have changed in this version as we added the capability to redirect input from the Chrome Extension to a web server of your choice via HTTP POST. Content is sent only to the URL you add as a search provider, using Javascript. To see the actual code, press Ctrl-Shift-I to view the developer’s tools in Chrome.
Most users will NOT need to use the POST function – just ignore it. The POST function is useful when you want to POST (versus GET) a search term to an application or API. You would copy the destination URL to the ‘Link’ field and add the raw POST data in the ‘Add POST value’ field. The HTTP POST will come from the Chrome extension by default, which some applications/APIs will not allow. In that case, use a PROXY to send the POST. A simple proxy script can be found here.
Note – Virus Total has changed MD5 lookup – use this instead https://www.virustotal.com/gui/file/TESTSEARCH/detection
Version 3.3 – Updated on 12/5/2013 to fix bug when using SSL with Security Analytics enabled. Added Carbon Black support (beta)
Version 3.0.7 – Updated on 10/9/2013 to fix bug when saving new NetWitness Pivot Query
Version 3 – added integration with RSA NetWitness (Windows client)
Version 2 – added integration with RSA Security Analytics web interface
The extension is available at the Chrome Web Store. You need at least Chrome version 6.0.472 to install and use this extension.
The screen shot below shows the intended usage – being able to search an IP address, a domain, or MD5 hash easily by opening multiple security websites at the same time.
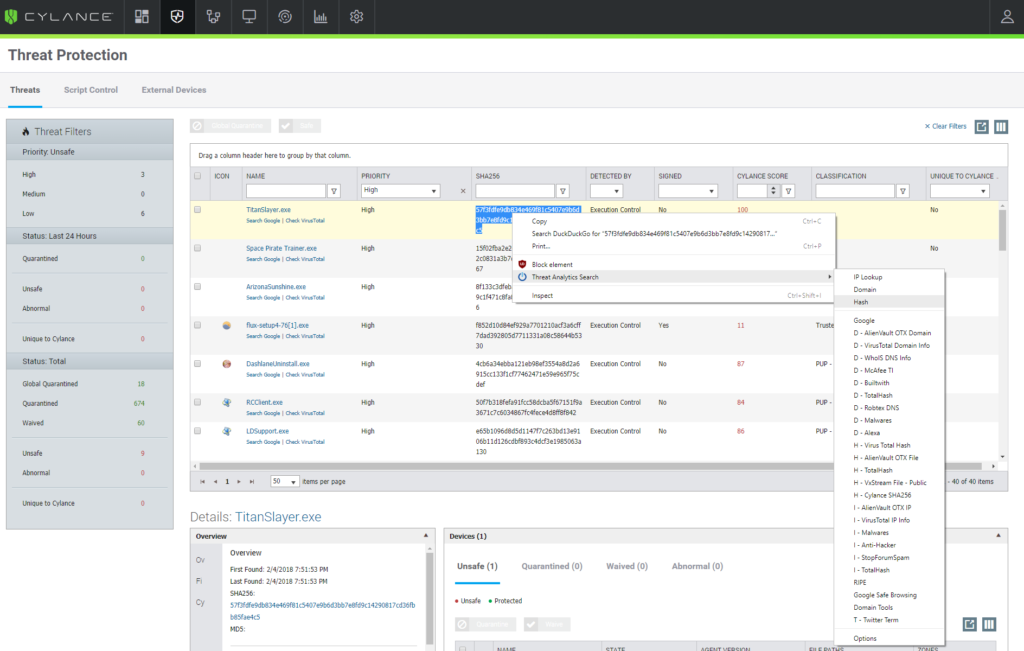
The screenshot below is an example of the configuration options. By selecting the URL and clicking on “Domain Lookup”, the entire group will be opened in new tabs. This saves valuable time for security analysts involved in the investigations of a plethora of events. You can edit the group names (IP Lookup, Domain) just by clicking in the column header. Drag the arrows to rearrange search providers.
The initial configuration is downloaded from our website here. It looks like:
{“searchproviders”:[[“-1″,”Virus Total Hash”,”https://www.virustotal.com/file/%s/analysis/”,true,true,0],[“-1″,”Bit9 MD5 Hash”,”https://fileadvisor.bit9.com/services/extinfo.aspx?md5=%s”,true,true,0],[“-1″,”Google”,”http://www.google.com/search?q=TESTSEARCH”,true,true,3],[“-1″,”Google Safe Browsing”,”http://www.google.com/safebrowsing/diagnostic?site=%s”,true,true,3],[“-1″,”Central Ops”,”http://centralops.net/co/DomainDossier.aspx?addr=%s&dom_dns=1&dom_whois=1&net_whois=1″,true,true,3],[“-1″,”Malware DL”,”http://www.malwaredomainlist.com/mdl.php?search=%s&colsearch=All&quantity=50″,true,true,3],[“-1″,”URL Void”,”http://urlvoid.com/scan/%s/”,true,true,2],[“-1″,”URL Void IP”,”http://urlvoid.com/ip/%s”,true,true,1],[“-1″,”Robtex IP”,”http://ip.robtex.com/%s.html”,true,true,1]],”groups”:[[“1″,”IP Lookup”],[“2″,”Domain Lookup”]],”config”:[[“https://www.criticalstart.com/cschromeplugin/criticalstart.txt”,”true”,”false”,””,””]]}You can also make your own configuration file and host it yourself. Use the example one supplied as a guide. The first boolean value for each search provider (true/false) determines if the search provider is enabled by default. The second boolean value shows if the provider came from the remote configuration file or was added manually. The last item determines if the search provider is a member of no groups (0), group 1 (1), group 2 (2), or both groups (3).
If you have suggestions for search providers or improvements, please send an email to [email protected]. This will automatically open a case in our ticketing system.
Stay Connected on Today’s Cyber Threat Landscape
RELATED RESOURCES
![]() Datasheet
DatasheetManaged Detection and Response Services
Human-Driven MDR Enhanced With Proactive Cybersecurity Intelligence Increase your security operation...![]() Video
VideoStop Drowning in Logs: How Tailored Log Management and Premier Threat Detection Keep You Afloat
Are you overwhelmed by security logs and complex threat detection? Watch our on-demand webinar to le...![]() Datasheet
DatasheetCritical Start MDR Services for Operational Technology
Gain 24x7x365 visibility and threat detection across Information Technology (IT) and Operational Tec...
RESOURCE CATEGORIES
-
- Consumer Education(40)
- Consumer Stories(2)
- Cybersecurity Consulting(7)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(78)
- MobileSOC(9)
- News(5)
- Press Release(93)
- Research Report(11)
- Security Assessments(4)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)



